Malwarebytes experts have discovered an interesting MageCart script (web skimmer) that not only infects online stores and steals bank card details of their visitors, but also parasitizes on other hackers’ malware.
Let me remind you that initially the name MageCart was assigned to one hack group, which was the first to introduce web skimmers (malicious JavaScript) on the pages of online stores to steal bank card data.However, this approach turned out to be so successful that the group soon had numerous imitators, and the name MageCart became a common name and now denotes a whole class of such attacks.
Let me also remind you that MageCart malware operators accidentally disclosed addresses of hacked stores.
Researchers discovered the new skimmer while investigating a wave of hacks in online stores running the outdated Magento 1. While the presence of malware on such sites is not surprising, the malware infecting them turned out to be interesting.
“The attackers have developed a special version of the script that knows about sites already infected with another skimmer for Magento 1. The second skimmer simply collects credit card data from pre-existing fake forms that were inserted into the site by previous attackers”, — Malwarebytes analysts write.
Costway was one of the victims of these attacks, which used Magento 1 for its online stores in France, the UK, Germany and Spain.
That is, the first hack group hacked the company’s websites and introduced them with fake payment forms that steal financial data of buyers. The second hack group additionally uploaded their own custom web skimmers to these sites from the securityxx[.]top domain.
So, one script collects data from an already existing skimmer of the first group, and the second is activated only if the store has been cleared of malware introduced during the initial Magento 1 hack.
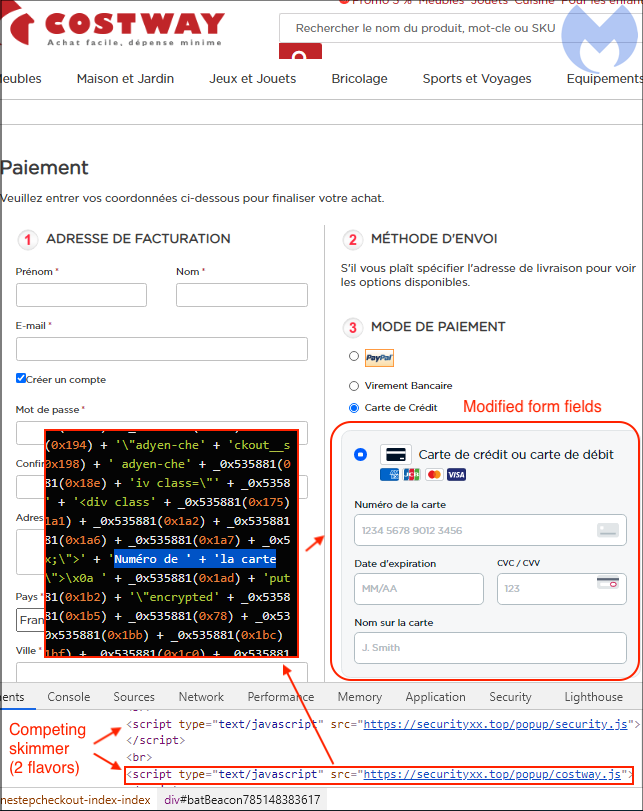
Thus, two hacker groups introduced three different MageCart scripts to the sites of the hacked stores. The researchers note that such situations are not uncommon, and MageCart groups often compete with each other, destroying or trying to use the malware of their “co-workers”.
Let me remind you that we wrote that IS experts discovered a link between North Korean hackers and MageCart attacks.