For Business
-

Mirai Botnet Comes with new 11 Exploits to Attack Enterprise Devices
Researchers saw a new variant of the Mirai botnet, which now involves 11 new exploits. Among the goals of the…
Read More » -

Android Q beta release with security and privacy improvements.
Google has released the first beta version of the new version of the mobile operating system Android 10 or Android…
Read More » -

Coinhive will shut down its cryptomining service in March 8, 2019
The famous service Coinhive for the legitimate mining of cryptocurrencies, which many intruders so fond of, will soon cease to…
Read More » -

Wendy’s agrees to pay $50 million.
WENDY’S AGREES TO PAY $50M TO SETTLE DATA BREACH CLAIMS Wendy’s American chain of fast-food restaurants agreed to pay $50…
Read More » -

Xiaomi M365 scooters can be hacked and managed remotely
Xiaomi M365 electric scooters are vulnerable – the security problem in these vehicles was discovered by expert Reni Idan from…
Read More » -
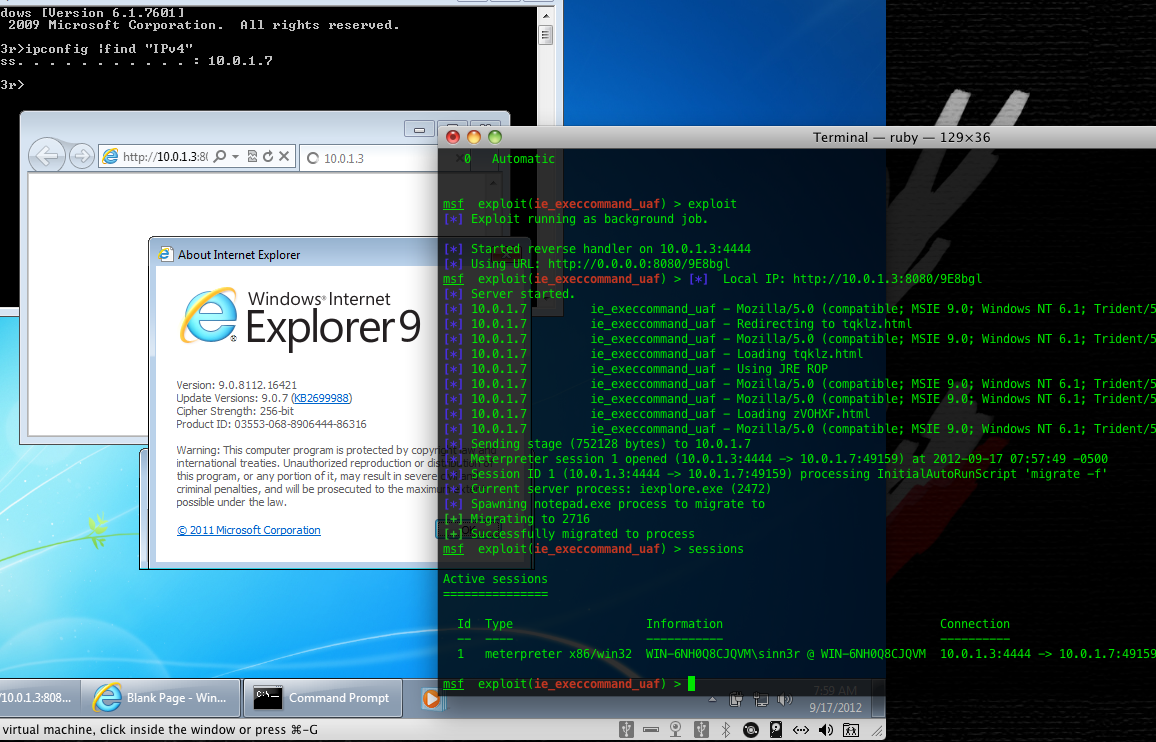
Microsoft has eliminated 0-day in Internet Explorer & Exchange Server
Microsoft has released a regular monthly set of patches, eliminating fairly serious security problems. First of all, we are talking…
Read More » -

620 million accounts from 16 different sites was found in Dark Web.
On the Dark Web sites, data of 617 million accounts were discovered, which were stolen from 16 different websites. Vendors…
Read More » -

Apple threatens to remove iPhone apps caught recording user activity
Apple has delivered an ultimatum to application developers who are hiding the screens of device owners on iOS. Now, developers…
Read More » -

Data Protection basis for everyone
This guide explains the effect and purpose of each principle that relates to data protection. The independent authority of the…
Read More »

