Chrome Extensions May Be Tracking the User on the Internet
A researcher known as z0ccc claims that Chrome extensions may be tracking user activity on the Internet.
z0ccc created the Extension Fingerprints site, which collects data on installed extensions for Google Chrome and, based on this data, creates a user profile. This profile can then be used to track a person on the Internet.
Let me remind you that we talked about the fact that North Korean hackers exploited 0-day bug in Chrome, and also that The researcher has published an RCE exploit for Chrome, Opera, Brave and other Chromium browsers.
This method relies on the fact that when you create a Chrome extension, you can declare certain assets as web-accessible resources, and they can be accessed by web pages or other extensions. Typically, these resources are image files that use web_accessible_resources, as specified in the extension’s manifest file.
Back in 2019, a study was published proving that such resources available via the Internet can be used to collect data about installed extensions and then fingerprint the user’s browser.
To prevent this, some extensions use a secret token that is required to access a web resource. However, z0ccc discovered a method that still allows collecting information about installed extensions.
While some extensions, such as MetaMask, don’t provide any resources at all, z0ccc writes that it’s still possible to tell if they’re installed by checking typeof window.ethereum and see if it’s undefined.
To illustrate how his method works, z0ccc created the aforementioned site that checks the visitor’s browser for available resources for 1170 popular extensions from the Google Chrome Web Store (including popular solutions like uBlock, LastPass, Adobe Acrobat, Honey, Grammarly, Rakuten, and ColorZilla).
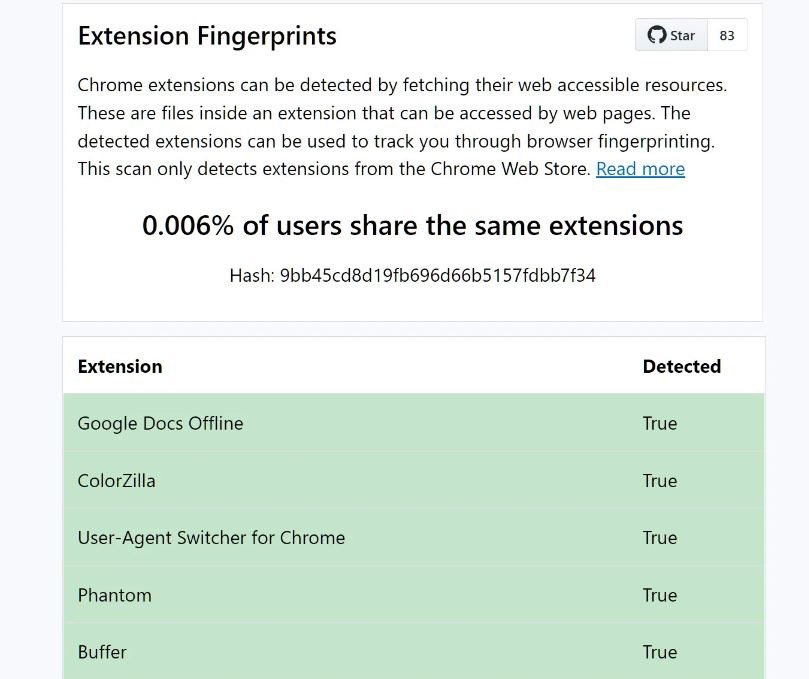
Based on the collected statistics, the site generates a hash that can then be used to track a specific browser.
Although z0ccc does not collect any data on installed extensions, its tests showed that uBlock is the most common extension, and the most popular option turned out to be no extensions installed at all.
Edition Bleeping Computer notes that installing three or four extensions reduces the percentage of users with a similar set to 0.006%. That is, the more extensions installed, the smaller percentage of people will have similar combinations. Z0ccc notes that the result of 0.006% indicates that this is the only user with this combination of extensions. Although the percentages will change as more people visit the site.
The sources for the Extension Fingerprints project are available on GitHub.