Ikea fights cyberattack on company mail system
Media reports that Ikea is fighting an ongoing cyberattack on its email system by using internal phishing against employees using stolen email chains.
Such attacks are based on the fact that cybercriminals steal legitimate corporate correspondence and then integrate into existing email chains, sending victims links to malicious documents, which then install malware on recipient devices. Since such emails are legitimate emails and are usually sent on behalf of compromised accounts and internal company servers, recipients tend to trust such emails.Bleeping Computer writes that its editors have obtained internal emails in which Ikea warns its employees about the ongoing cyberattack using email chains. Such letters come to employees both from internal mailboxes and from other hacked organizations and Ikea business partners.
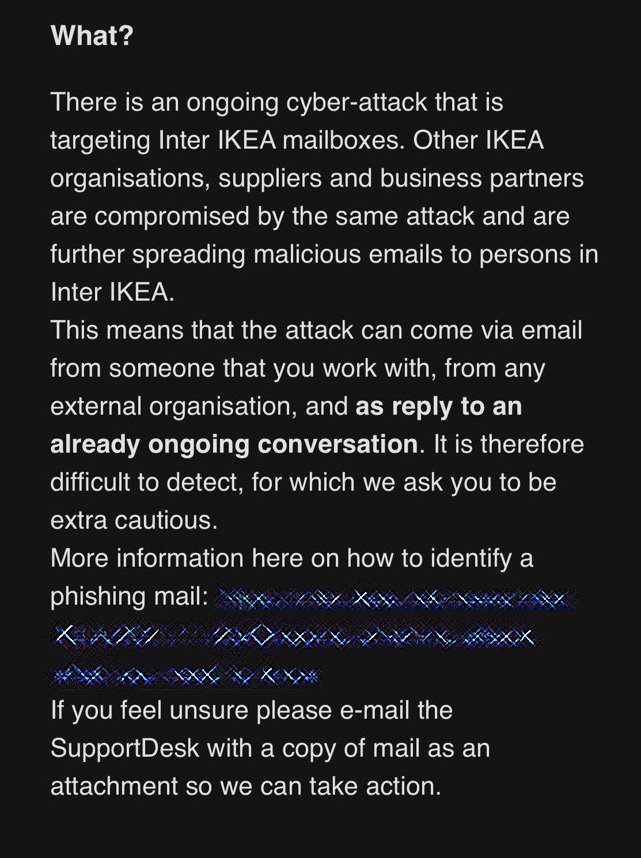
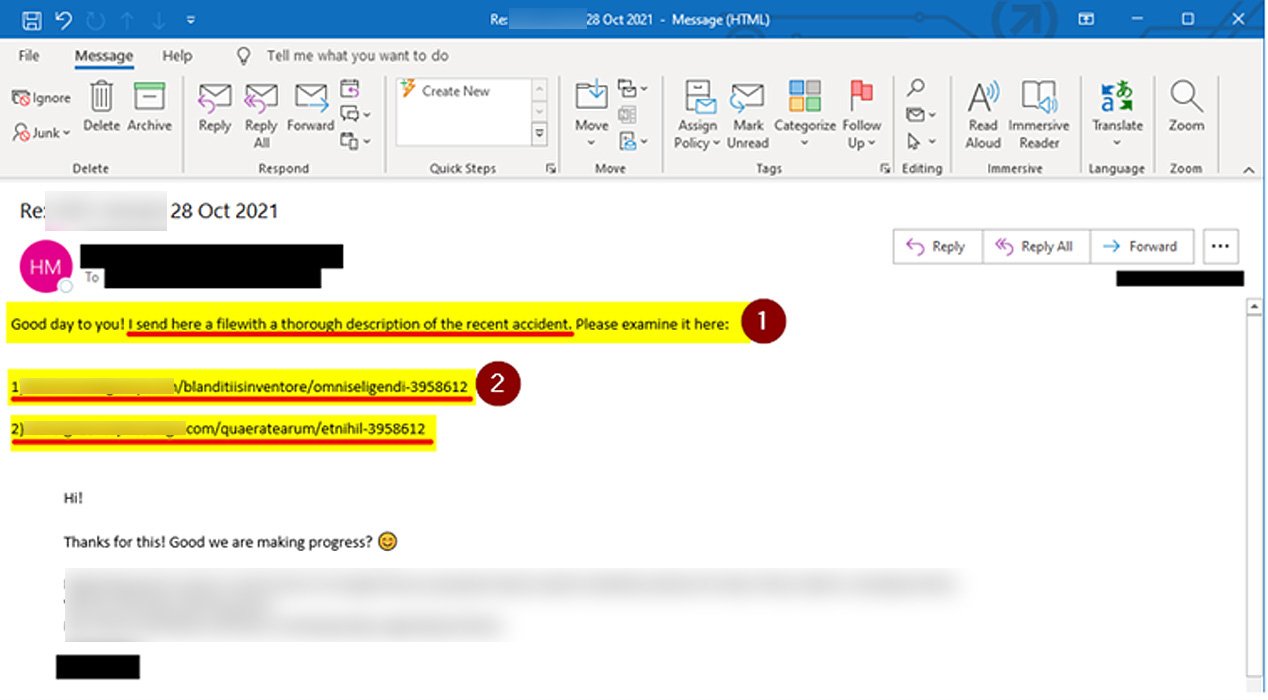
The company’s IT specialists report that such emails contain links with seven numbers at the end, and give an example of such a message. Currently, employees are generally advised not to open emails, regardless of the sender, and immediately report any suspicions to the IT department.
The publication recalls that recently, Trend Micro specialists also warned about such attacks.
Experts wrote that cybercriminals are breaking into Microsoft Exchange servers around the world in order to gain access to their messaging capabilities and send malicious emails to customers and company employees. According to them, hackers are attacking Exchange servers that are vulnerable to problems such as ProxyLogon (CVE-2021-26855) and ProxyShell (CVE-2021-34473 and CVE-2021-34523). Once they gain access to the server, they use the Powershell function to read and interact with the server’s mail storage system, and also integrate into existing conversations, sending new malicious messages to all participants.
Let me remind you that we also talked about the fact that Hacked Oxford server was used for phishing attacks on Office 365.





