Check Point experts unveiled a sophisticated cybercriminal campaign aimed at collecting corporate data and compromising Microsoft Office 365 accounts through phishing attacks.
To avoid detection, the attackers used the servers of well-known organizations – Oxford University, Adobe and Samsung. 43% of these attacks were targeted at European companies, while the rest were seen in Asia and the Middle East.Recall that recently APWG Noted Three-Year Phishing Record.
Researchers say that in recent years, the use of Office 365 in the corporate sector has significantly increased. The popularity of the products attracted the attention of cybercriminals, who began to launch phishing campaigns to attack this platform.
“So, in the detected campaign, the attackers compromised the mail server of the University of Oxford and sent spam from there. These emails contained links that redirected victims to the Adobe server that was previously used by Samsung“, – report Check Point experts.
This allowed hackers to simulate legitimate Samsung domain and lull the vigilance of victims and defense mechanisms. As a result, the victims were redirected to the fake login credentials page for Office 365.
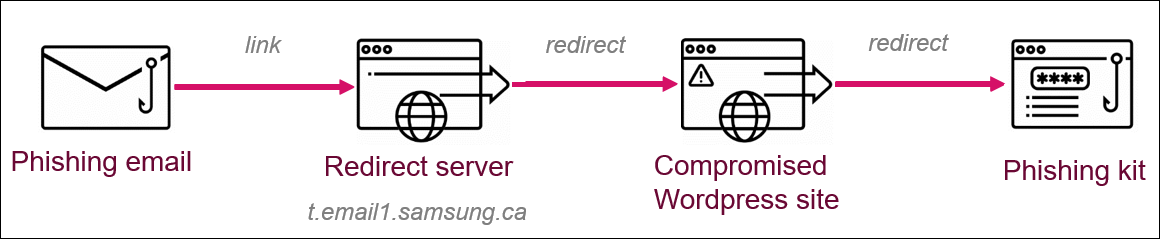
Essentially, the hackers abused the Adobe Campaign open redirect mechanism and used the Samsung domain to redirect victims to the Office 365 phishing site. They took advantage of the fact that the domain of a reputable company like Samsung would not arouse suspicion and would not be blocked by security solutions.
“Essentially, the links that redirected the victims to the Adobe server previously were used by Samsung during the Samsung Cyber Monday 2018 marketing campaign”, – say the researchers.
In other words, the link embedded in the original phishing email belonged to the Samsung domain, from where the victims were redirected to a site controlled by hackers.
It all started with the fact that at the beginning of April 2020, Check Point researchers examined emails with the topic “Office 365 Voice Mail” received by the victims. These letters reported that to listen to a message, the user needs to click on the link.
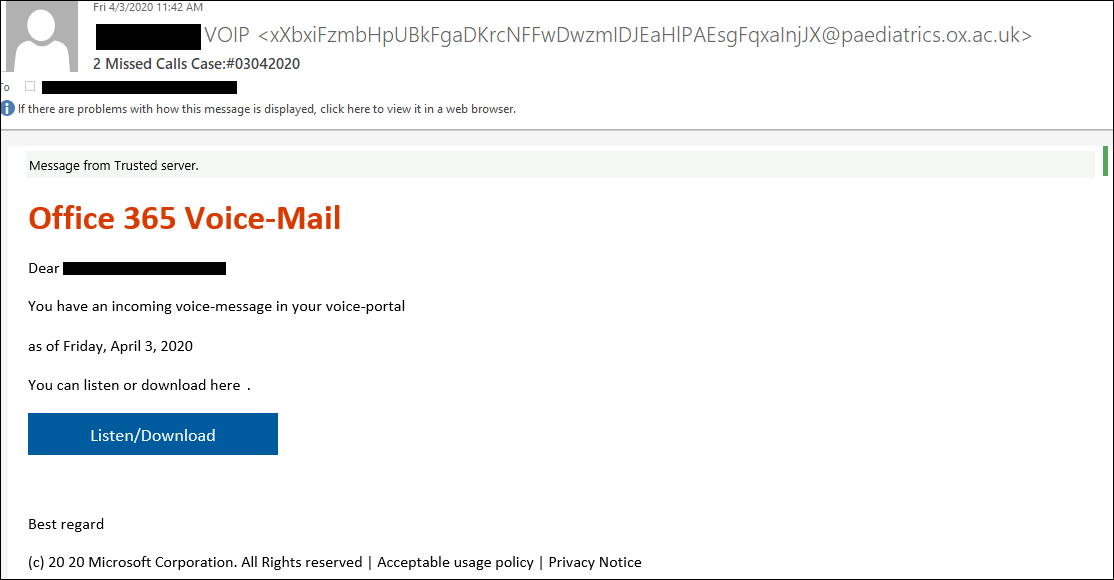
If the victim clicked on the link, it was redirected to a phishing page masked as an Office 365 login page. In fact, this redirection consisted of two stages: the first stage used the existing redirect scheme on a legitimate domain (for example, samsung[.]Ca), and the second stage redirected the user to a compromised WordPress site.
The phishing kits used in the second stage of the attack were hosted on several hacked WordPress-based sites. At the same time, hackers checked whether visitors came to the hacked site through a phishing email, and if not, they stopped the attack and lead users to the real site instead of a phishing page.
The mentioned malicious emails came from several addresses that belonged to real subdomains of different departments of Oxford University. The headers indicated that hackers had found a way to use one of the Oxford SMTP servers for their own purposes.
The final page, which hosted the phishing kit and was used to collect and steal credentials from Office 365, was completely obfuscated, and for each victim were created separate virtual directories and each was assigned unique URLs.
“Using real Oxford SMTP servers allowed attackers to bypass a sender domain reputation check. In addition, there was no need to risk real email accounts to send phishing emails, because attackers could generate as many email addresses as they wanted”, — write the researchers.
In addition, in this campaign, attackers constantly changed and improved redirection methods and URL parameters in phishing links to make them independent from a specific domain and Adobe Campaign servers, and to avoid detection.
Experts note that Adobe engineers have already taken appropriate measures to prevent such attacks through their servers.
And we will warn you that attackers could exploit the vulnerabilities of Alexa and Google Home to phishing and spying on their users