Parrot TDS Malicious Service Uses 16,500 Websites to Spread Malware
Avast security experts have discovered a malicious Parrot TDS (Traffic Direction System) service that relies on hacked servers hosting 16,500 university, municipal government, adult content, and personal blogs.
As in other similar cases, Parrot is used for malicious campaigns, in which potential victims that match a certain profile (location, language, operating system, browser are taken into account) are redirected to fraudulent resources, such as phishing sites and sites with malware. Essentially, attackers buy TDS services to filter incoming traffic and redirect victims to their desired destination with malicious content.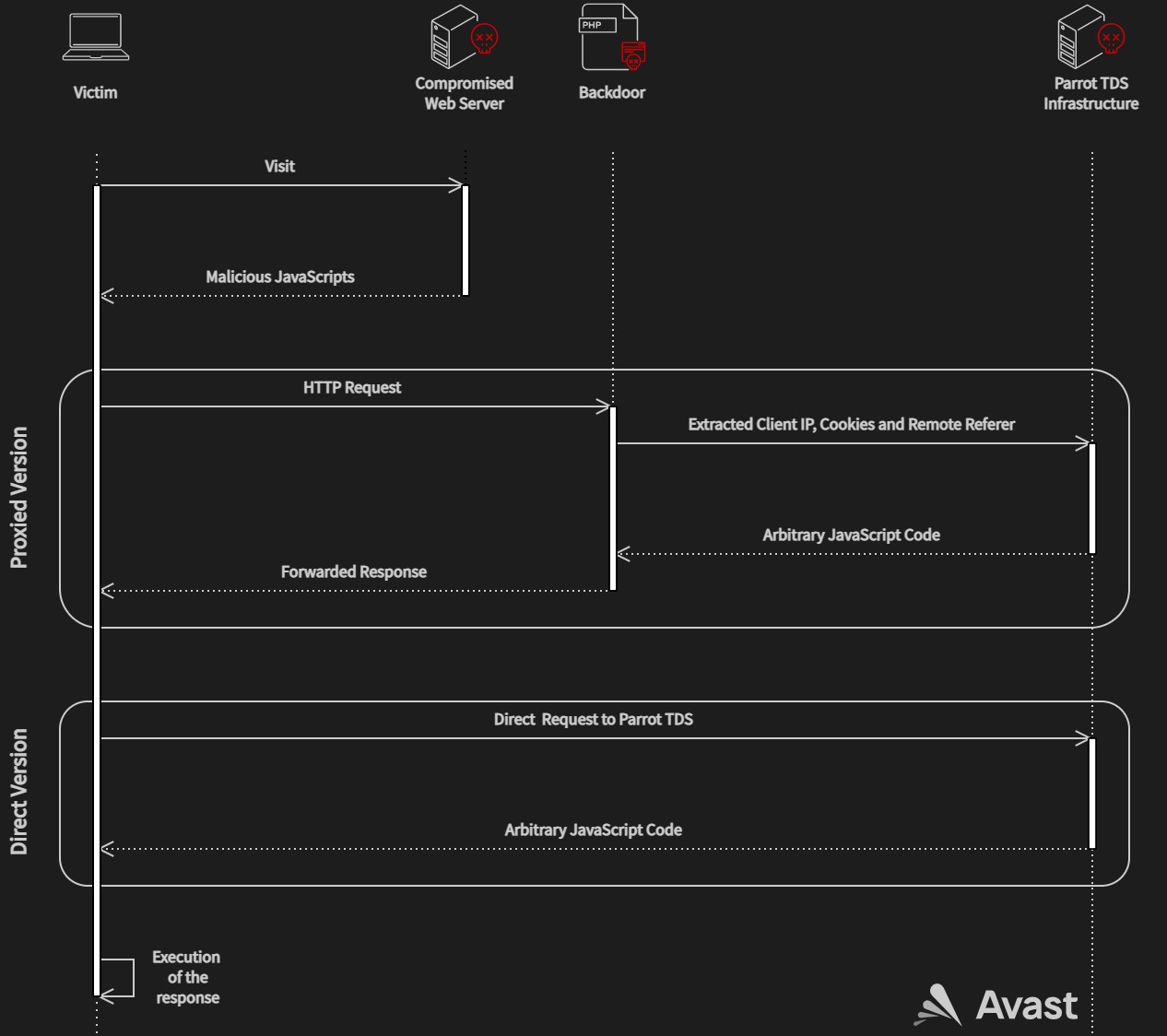
To be fair, TDS is often used quite legally by advertisers and marketers, although some of these services have been used for spam campaigns in the past.
Analysts write that Parrot TDS is currently being used for a campaign called FakeUpdate, which mainly spreads Remote Access Trojans (RATs) through fake update notifications.
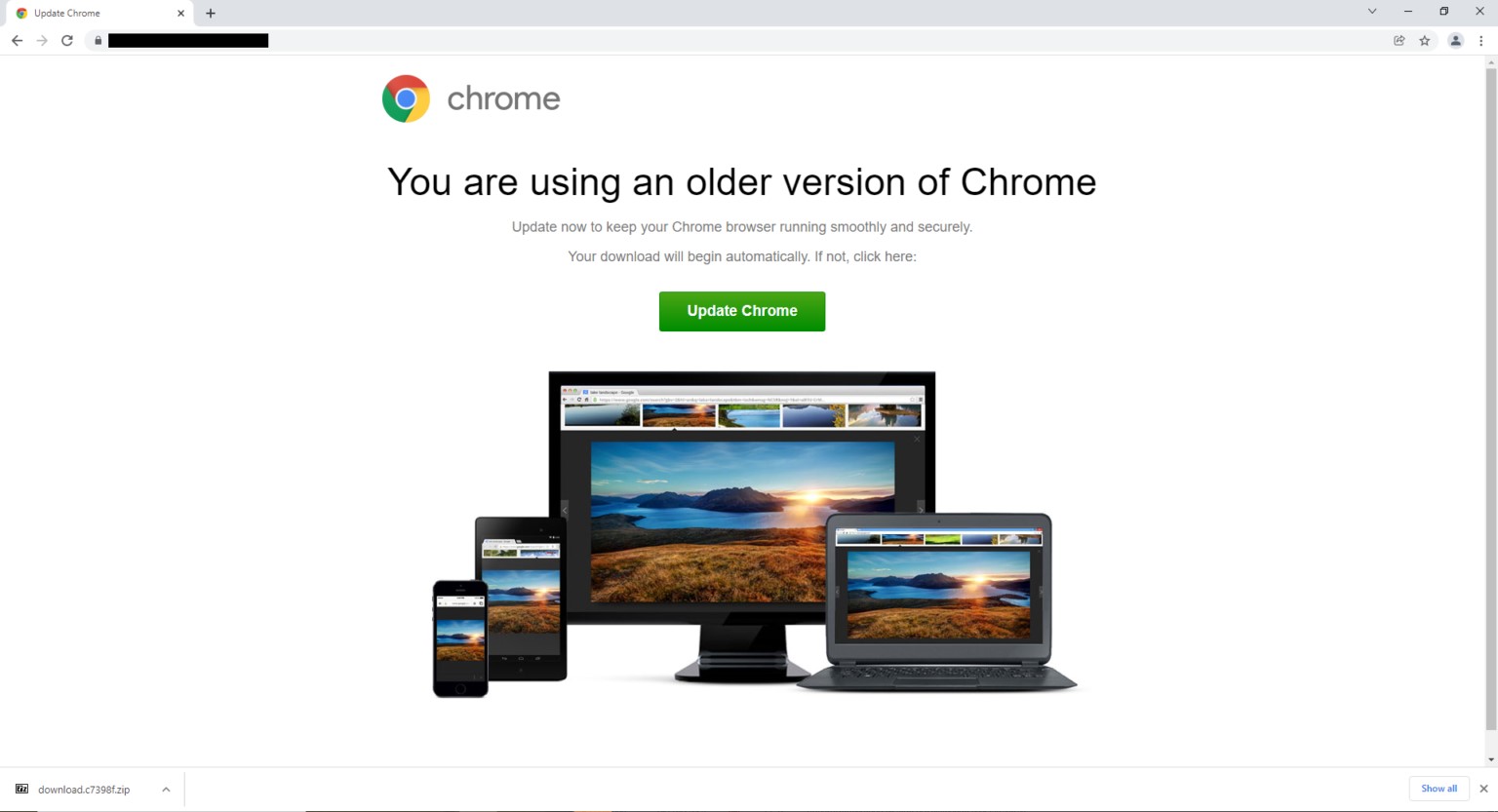
This campaign started in February 2022, but the first signs of Parrot activity could be seen as early as October 2021.
Attackers install web shells on such servers and then copy them to different places under the same names. Hence the name Parrot – from the English “parrot”, repeating the same thing over and over again.
In addition, the attackers use a backdoor in the form of a PHP script that extracts information about the client and redirects requests to the Parrot TDS control server. In some cases, operators use a shortcut without a PHP script, sending requests directly to the Parrot infrastructure.
At the same time, filtering of users works so precisely that among thousands of redirected users attackers can target a specific person, experts say. As a result, users are redirected to unique URLs based on an extensive summary of their hardware, software, and network profile.
RAT NetSupport most often serves as a payload and is configured to work in automatic mode, which provides its operators with direct access to compromised machines. Phishing sites are also hosted on some infected servers. Their landing pages resemble a real Microsoft sign-in page, and visitors are asked to enter their account credentials.
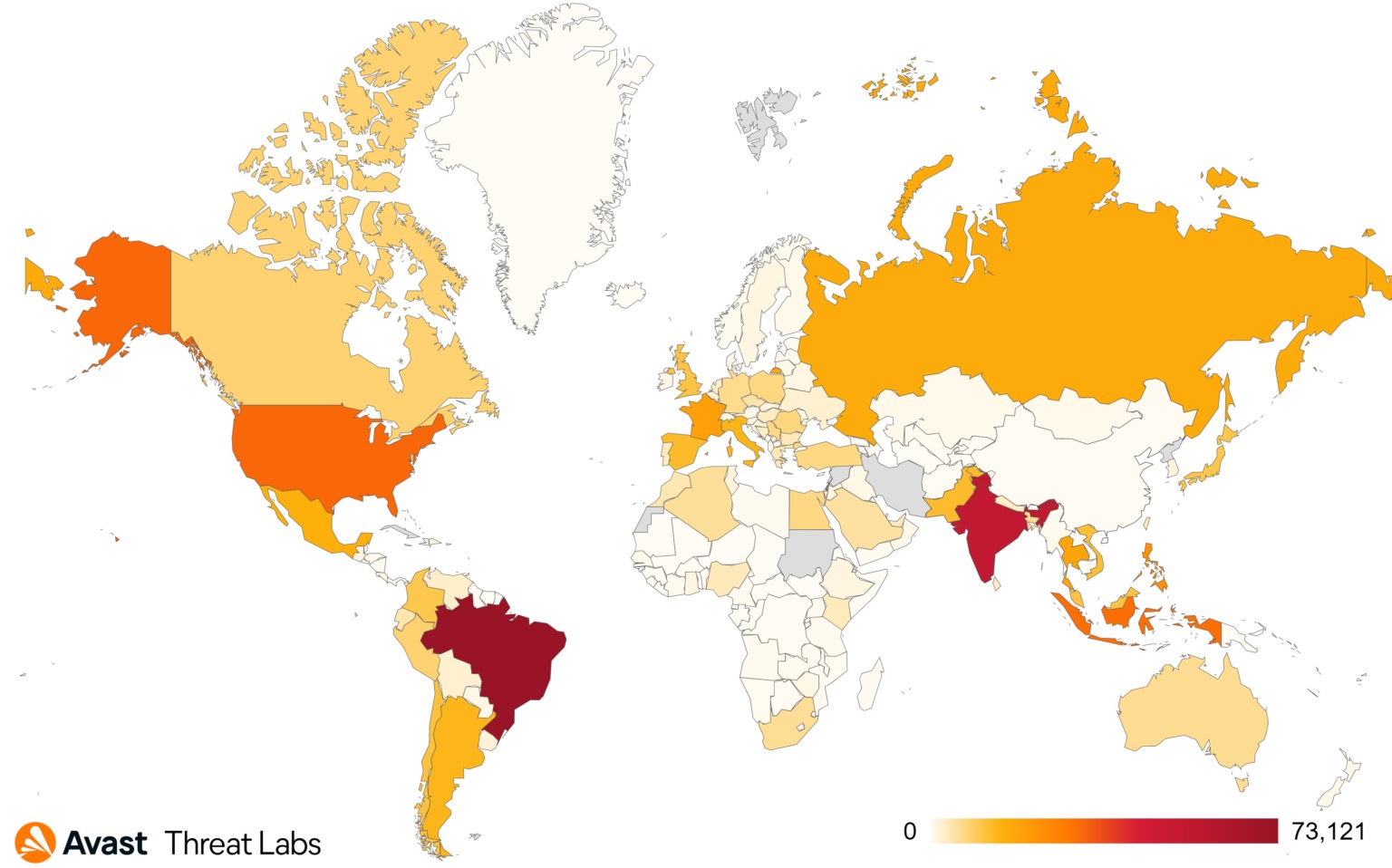
Avast analysts report that in March 2022 alone, they managed to protect more than 600,000 customers from visiting infected sites, which indicates the huge scale of Parrot TDS. Most of the users who were victims of malicious redirects were in Brazil, India, the United States, Singapore, and Indonesia.
Let me remind you that we also talked about the fact that Emotet botnet is growing slowly but has already infected over 130,000 machines, and also that Trickbot ransomware wanted to open offices in St. Petersburg.