Emotet botnet grows slowly but has already infected over 130,000 machines
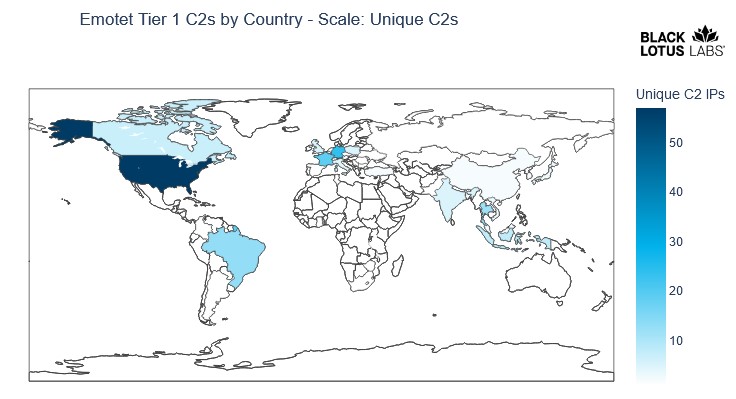
The Emotet botnet, which resumed activity at the end of 2021, is growing and still continues to develop slowly. So far, it has infected more than 130,000 devices in 179 countries, according to researchers.
Let me remind you that in January last year, Europol, the FBI and law enforcement agencies in many countries of the world, including Canada, the Netherlands, France, Germany, Lithuania, the UK and Ukraine, conducted a large-scale coordinated operation to eliminate Emotet. Preparation for this operation lasted two years. Then law enforcement officers managed to seize control over the botnet infrastructure, disrupting its operation. As a result, criminals lost the ability to use hacked machines, and the malware stopped spreading to new targets.However, at the end of 2021, ten months after this operation, the researchers again discovered malware activity. It turned out that another well-known botnet, TrickBot, helped Emotet operators get back on their feet by installing Emotet malware on systems already infected by TrickBot itself. It soon became apparent that the hack group Conti was behind Emotet’s comeback.
Analysts from Black Lotus Lab decided to take a closer look at the new round of Emotet development. As you can see in the chart below, the botnet started to slowly recreate itself in November last year, and since January 2022 has grown much faster thanks to phishing campaigns.
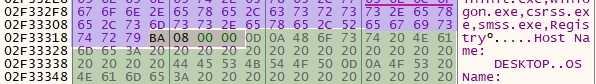
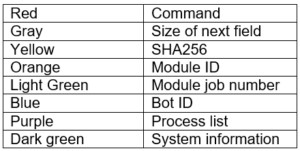
This Emotet distribution campaign also possesses some new features, such as a new elliptic curve cryptography scheme that replaces RSA encryption. Also in the new version, the process list module is deployed only after establishing a connection with the control server. In addition, the authors of the malware have added to their product more opportunities for collecting information and better profiling the system.
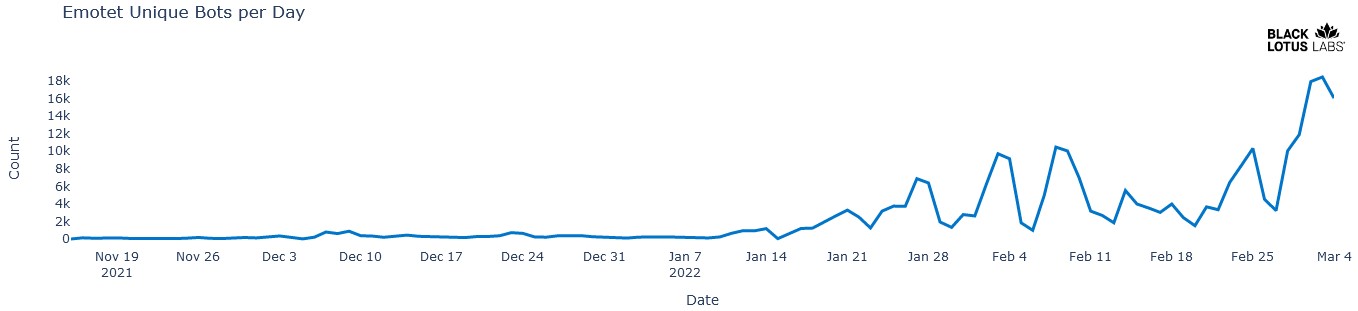
Black Lotus reports that there are currently around 200 unique management servers supporting the Emotet resurgence, and the number is steadily growing. The average time of activity of one server is 29 days.