North Korean Hackers Use the Sinbad Cryptocurrency Mixer through Which They Launder Money
Blockchain analysts say North Korean hackers have found a way to bypass US-imposed sanctions and are still laundering stolen money and cryptocurrencies.
In particular, according to Chainalysis, the criminals laundered almost $25 million worth of cryptocurrencies using the new Sinbad mixer service.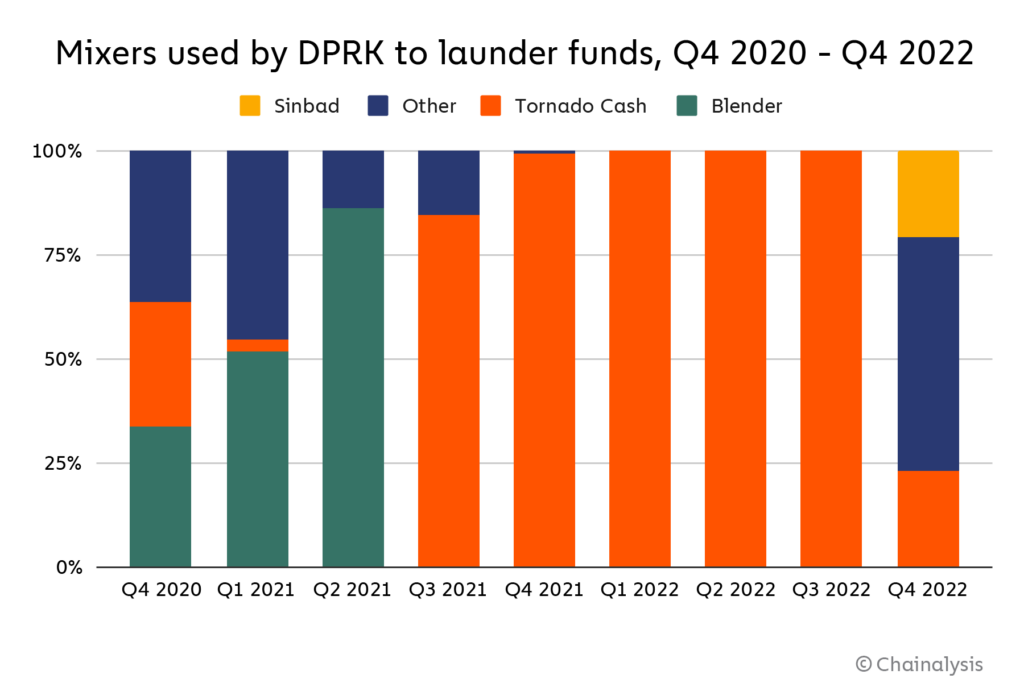
Last year, U.S. authorities imposed sanctions on mixing services like Blender and Tornado Cash, which were used by North Korean Lazarus hackers to launder about $500 million in illegally obtained cryptocurrencies.
Let me remind you that the media indicated that North Korean hackers attack IS specialists again.
I note that although Lazarus is usually referred to in expert reports as a single group, in fact, this term refers to many groups of North Korean hackers who are tasked by the government to collect intelligence or steal money to support national projects.
According to the authorities, funds stolen by hackers as a result of the Harmony hack (about $ 96 million) passed through the mentioned Tornado Cash, funds received as a result of the compromise of the Ronin blockchain, which is closely related to the popular NFT game Axie Infinity (more than $ 600 million was stolen, through mixer laundered 455 million), as well as about 7.8 million dollars received during the compromise of the Nomad cryptocurrency bridge.
Although these sanctions did not stop Tornado Cash from operating (many in the cryptocurrency industry did not like the government’s actions at all), the Blender operators soon disappeared along with their service, allegedly taking with them $ 22 million in bitcoins.
As Elliptic analysts now write, apparently, in the fall of 2022, Blender operators launched a new service called Sinbad, which North Korean hackers are again using to launder stolen assets.
Suspicions about the connection between Lazarus and Sinbad arose among researchers after the Harmony Horizon cross-chain bridge was hacked. This heist, which took place last summer, resulted in the theft of $100 million worth of cryptocurrency assets. And this time, the hackers used the Sinbad bitcoin mixer to “clean up” the stolen funds.
Unlike Tornado Cash, Blender and Sinbad are custodial mixers, that is, all cryptocurrency entering the service is under the control of operators.
That being said, Elliptic’s analysis shows that Sinbad is highly likely run by the same people who were behind Blender. For example, the researchers found that Sinbad’s “official” address received bitcoins from a wallet believed to be owned by Blender operators.
In addition, the same wallet was also used to pay for advertising the new mixer and fund almost all of the initial transactions that went through Sinbad (about $22 million).
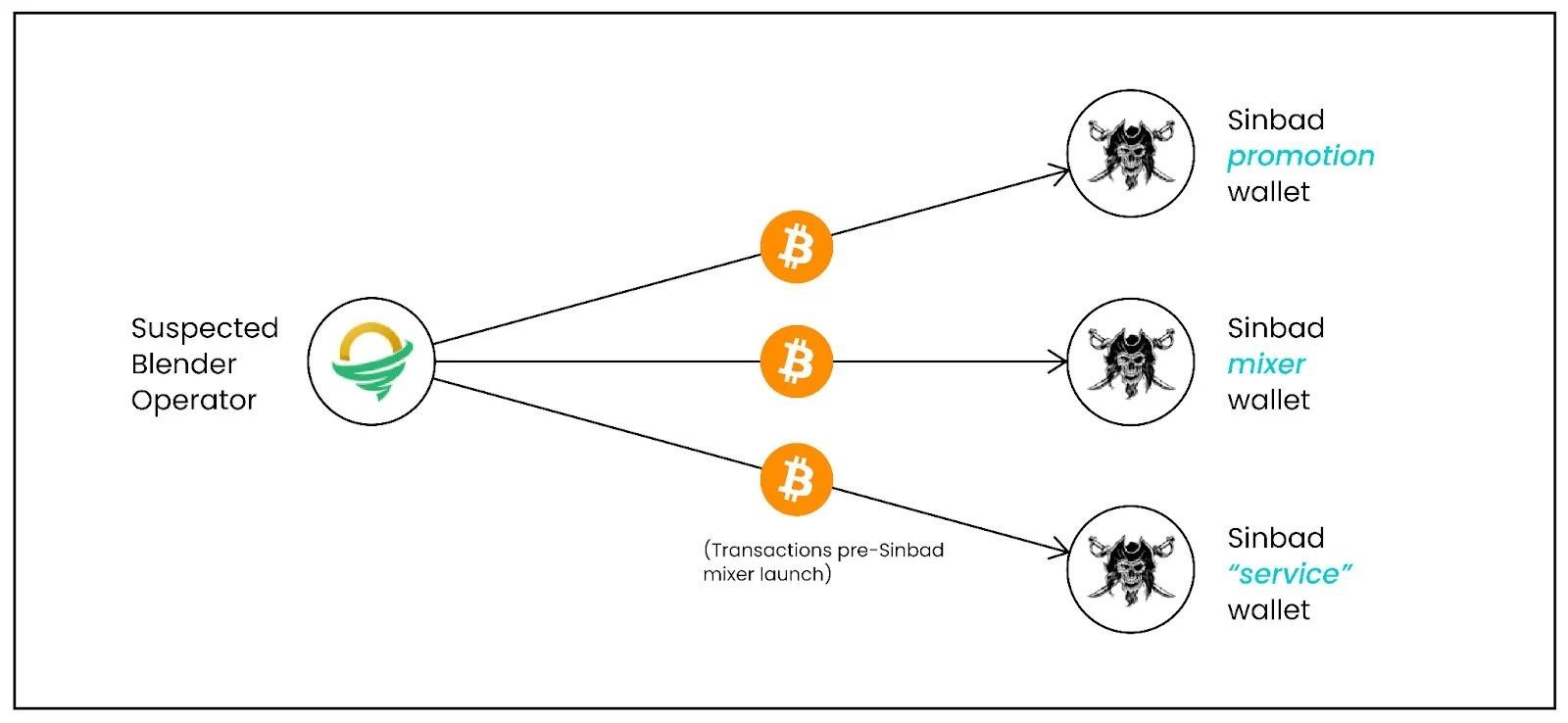
In addition, the researchers noticed similar network behavior for both mixers: “The way the Sinbad mixer works is largely identical to Blender, including ten-digit mixer codes, letters of guarantee signed with a service address, and a maximum transaction delay of seven days.”
Interestingly, in an interview with Wired, the Sinbad administrator called the service “a legitimate technology project that helps maintain privacy.”





