FBI Links North Korean Lazarus Hackers to Harmony Hack and $100 Million Theft
The FBI has officially linked the Harmony Horizon cross-chain bridge hack to Lazarus, a cyber-espionage group with ties to the North Korean government. The robbery, which took place last summer, resulted in the theft of $100 million worth of cryptocurrency assets.
Last year, shortly after the attackers took control of the MultiSigWallet contract and used it to transfer large amounts of tokens to their addresses, Elliptic blockchain analysts linked the attack to Lazarus activity, noting that the stolen funds were moving to wallets previously associated with this group.Now, the FBI has officially confirmed that the conclusions of the security experts were correct: North Korean hackers from the Lazarus (APT38) groups were behind this attack.
According to law enforcement, North Korean hack groups are stealing and laundering virtual currency to support government programs to build ballistic missiles and weapons of mass destruction.
The link between Lazarus and the robbery was revealed due to one of the attempts to launder the stolen assets, undertaken by hackers last week. On January 13, 2023, attackers reportedly attempted to transfer 41,000 ETH (about $63.5 million) through Railgun, which is being used as a replacement for the recently sanctioned Tornado Cash cryptocurrency mixer, before converting the funds into BTC and withdrawing to multiple addresses on three cryptocurrency exchanges.
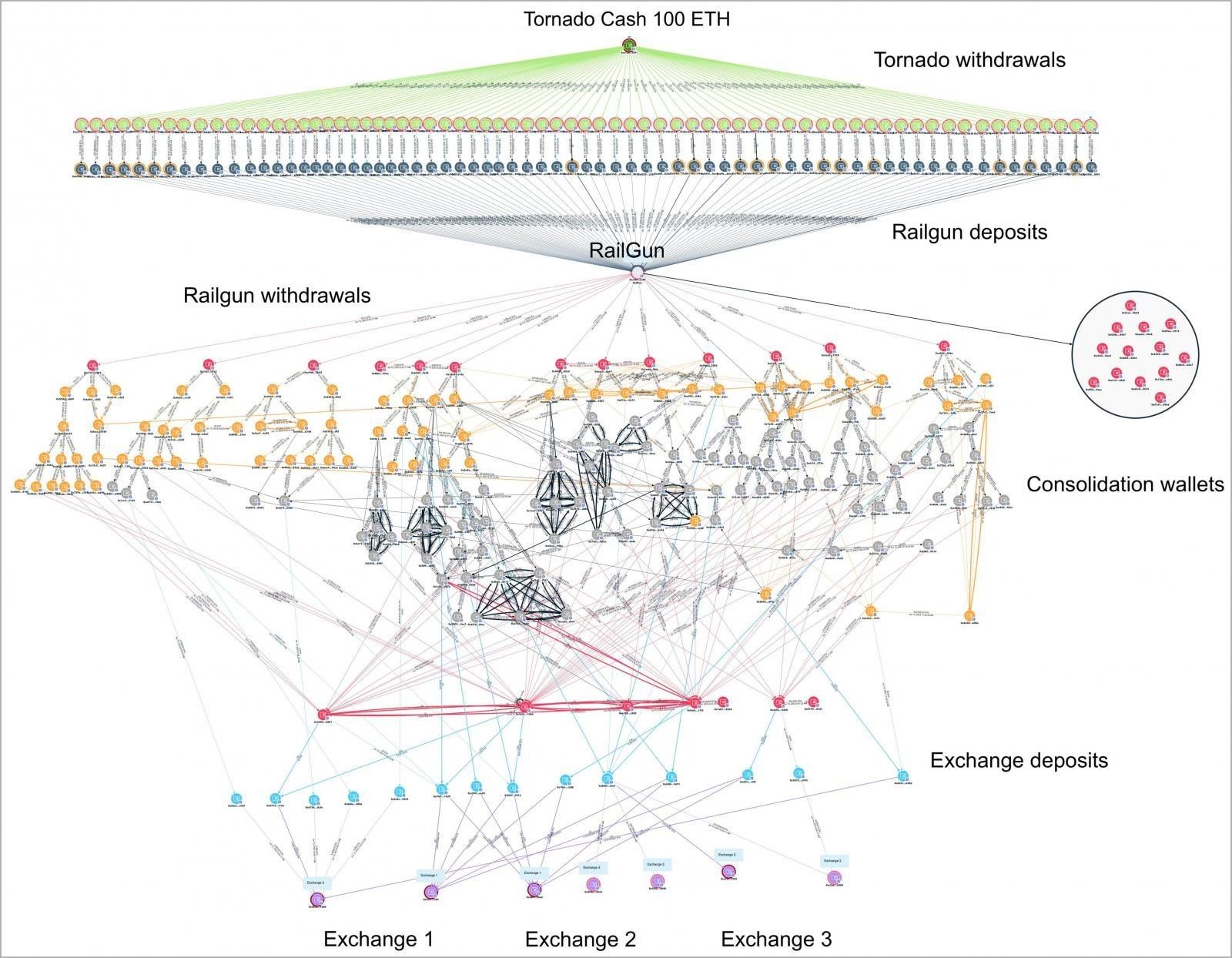
Money laundering scheme
It was found that about 350 addresses are under the direct control of Lazarus, and part of the stolen funds was eventually frozen on the accounts of the Binance and Huobi exchanges. However, the bulk of the assets still remain under the control of hackers in these wallets:
- 1BK769SseNefb6fe9QuFEi8W4KGbtP8gi3;
- 15FcqYRbwh2JsRUyBjvZ4jJ2XAD3pycGch;
- 1HwSof6jnbMFpfrRRa2jvydYdopkkGB4Sn;
- 15emeZ7buVegqhYh9PekH7cwFEJcCeVNpS;
- 3MSbCJCYtx5sj1nkzD4AMEhhvvviXBc8XJ;
- 17Z79rZpkk8kUiJseg5aELwYKaoLnirMUn;
- bc1qp2vvntdedxw4xwtyd4y3gc2t9ufk6pwz2ga4ge;
- 3P9WebHkiDxCi8LDXiRQp8atNEagcQeRA3;
- 37fnBxofDeph2fpBZxZKypNkwdXAt9nT6F;
- 185NxhFAmKZrdwn9rVga3kqbvDP4FkbTNw;
According to the authorities, during this attack, as well as during the attack on Axie Infinity and the Ronin sidechain, hackers used the TraderTraitor malware, which was aimed at compromising the machines of employees of target companies. This malware is usually delivered to victims through social engineering (via email or private messages) disguised as high-paying job offers.
The malware is written in cross-platform JavaScript that runs inside Electron and is capable of deploying secondary payloads on both Windows and macOS systems (depending on the platform used by the compromised employee).
Let me also remind you that the media wrote that Lazarus Hack Dell Devices Through Vulnerable Driver.





