News
Nobelium hack group uses FoggyWeb malware to inject backdoors
Microsoft specialists discovered a new malware of the Nobelium group and named it FoggyWeb. The malware is used to deploy additional payloads and steal sensitive data from Active Directory Federation Services (AD FS) servers.
The Nobelium hack group (aka APT 29, Cozy Bear, or The Dukes) is believed to be linked to the Russian government and is named as the one responsible for the SolarWinds hack, one of the largest supply chain attacks in history.Microsoft continues to work with partners and customers to track and expand our knowledge of the threat actor we refer to as NOBELIUM, the actor behind the SUNBURST backdoor, TEARDROP malware, and related components. As we stated before, we suspect that NOBELIUM can draw from significant operational resources often showcased in their campaigns, including custom-built malware and tools.the company said.
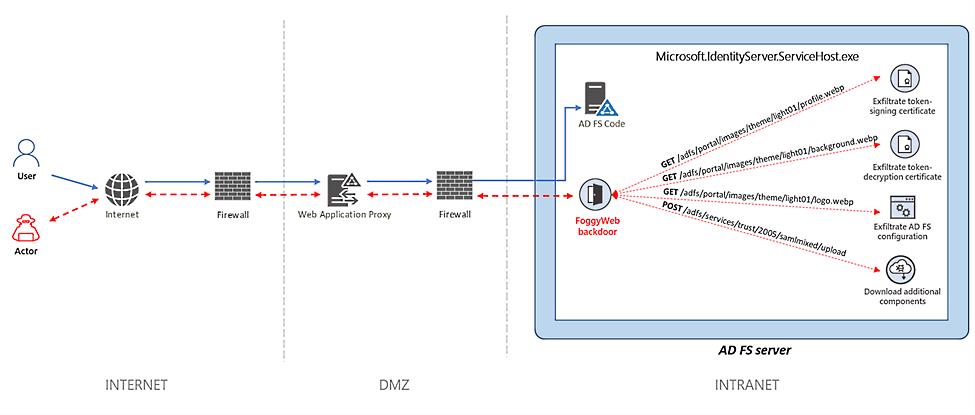
The malware, now discovered by Microsoft Threat Intelligence Center experts, is called FoggyWeb and is a “passive and highly targeted” backdoor that abuses Security Assertion Markup Language (SAML) tokens.
Nobelium uses FoggyWeb to remotely retrieve the configuration database of compromised AD FS servers, decrypt token-signing certificates and token-decryption certificates, and download and execute additional components. Also, FoggyWeb can receive additional malicious components of the C&C server and run them on a compromised server.Microsoft says.
This tool has been in use since April 2021 and has been helping attackers remotely extract sensitive information from compromised AD FS servers by configuring HTTP levers for specific URIs to intercept GET and POST requests sent to the AD FS server.
After obtaining credentials and successfully compromising the server, Nobelium uses the gained access to gain a foothold in the system and deepen the infiltration using sophisticated malware and tools.
To protect against such attacks, experts advise to pay attention to the security of AD FS servers in general, use hardware security modules, and regularly audit on-premises and cloud infrastructure.
Let me remind you that we also reported that Chinese hackers also took part in attacks on SolarWinds clients.
User Review
( votes)
Comments Rating
0
(0 reviews)





