Chinese hackers also took part in attacks on SolarWinds clients
At the end of last year, Microsoft researchers suggested that Chinese hackers were also involved in attacks on SolarWinds clients, and Secureworks recently confirmed this assumption.
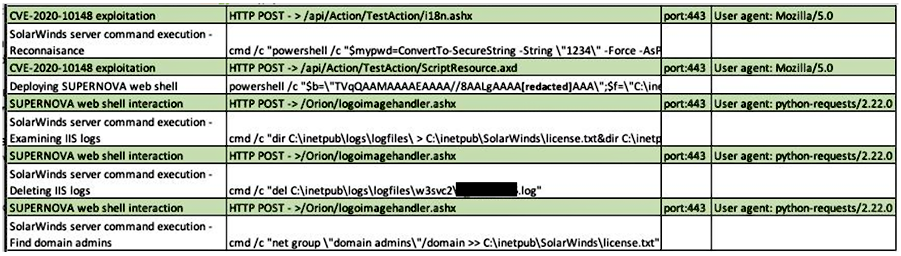
In December last year, many cybersecurity companies were investigating a large-scale attack on the supply chain that affected SolarWinds and its customers. Even then, experts’ reports mentioned not only the SUNBURST payload (aka Solorigate), which downloaded the Teardrop backdoor Trojan, but also the fact that attackers sometimes injected a web shell called Supernova into infected .NET networks.Let me remind you that we wrote that security experts linked Sunburst backdoor with the Kazuar malware.
At first, researchers believed the hackers were using Supernova to download, compile, and execute a malicious Powershell script (dubbed CosmicGale).
However, Microsoft analysts soon reported that Supernova was part of another attack, and it was not at all related to the sensational hack of the supply chain. It turned out that the Supernova web shell was injected into poorly protected SolarWinds Orion installations, vulnerable to the CVE-2019-8917 issue.
A report from Microsoft states that unlike the Sunburst DLL, the Supernova DLL was not signed with a legitimate SolarWinds certificate. Because of this, the experts concluded that this malware had nothing to do with the original attack on the supply chain and generally belonged to a different hack group.
Now Microsoft’s findings have been confirmed by Secureworks. This week the company released a report, according to which Supernova is linked to last year’s attacks on Zoho ManageEngine’s servers (this 0-day bug was simply posted on Twitter).
Secureworks is tracking the attackers who hacked Zoho ManageEngine, codenamed Spiral, and believes the hack group is based in China. So, during the August incident, hackers accidentally revealed one of their IP addresses, which turned out to be associated with the Celestial Empire.
As the researchers now write, the behavior of the Supernova malware is similar to the activity of the group in August last year, directed against the products of Zoho. It looks like Spiral could be responsible for both of these attacks, meaning Microsoft’s analysts were right.
“Similarities between SUPERNOVA-related activity in November and activity that CTU researchers analysed in August suggest that the SPIRAL threat group was responsible for both intrusions. Characteristics of these intrusions indicate a possible connection to China”, – Secureworks researchers write.
Let me also remind you that we wrote that the US government has warned agencies about cybersecurity risks for years.