Cybersecurity Cyble experts have reported that approximately 500000 Zoom accounts are sold on hacker forums and on the darknet, and some of them are distributed for free.
Only recently, IntSights specialists discovered that on the darknet is sold a dumpnet, which includes Zoom user credentials (email, passwords), as well as meeting IDs, host names and keys. It was a relatively small database containing only about 2300 records.“A database found on a darknet can contain partial information, but in other cases you can find a complete set of data in it, including a PIN code for all open sessions. Having access to the URL, identifier and PIN code, the attacker gets the opportunity to both enter the video conference and take control of it (and, for example, start removing participants just for fun)”, – said IntSights researchers.
Now Cybersecurity Cyble reports that half a million records is available.
Experts told reporters of the Bleeping Computer magazine about their finding. Researchers agree with the views of IntSights colleagues and write that the credentials they found are the result of an attack of the credential stuffing type.
The term credential stuffing refers to situations where usernames and passwords are stolen from some sites and then used against other users. That is, the attackers have a database of credentials (purchased on the darknet, collected independently, and so on) and try to use this data to log in to any sites and services.
Experts noticed Zoom trading accounts on April 1, 2020. They note that some attackers give away hacked accounts for free, thus trying to gain a reputation in the hacker community.
So, the example below shows a list of 290 accounts owned by the University of Vermont, the University of Colorado, Dartmouth College, the University of Florida, and more. All were published for free.
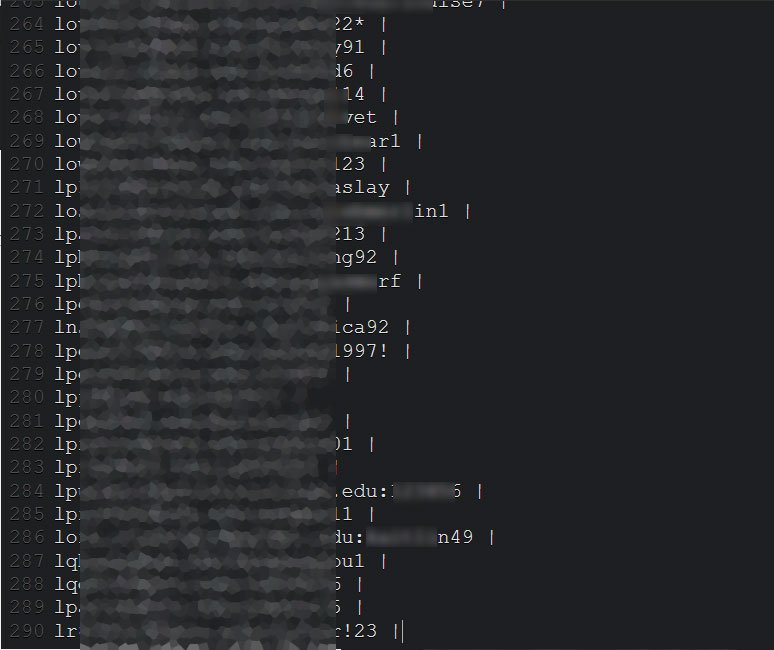
Bleeping Computer reporters contacted several victims from the list using provided email addresses and confirmed that such accounts exist. One user told the publication that the mentioned password was an old one, so, some credentials were probably the result of older credential stuffing attacks.
Noticing that one of the attackers is trading Zoom accounts on a hacker forum, Cyble specialists contacted him and agreed to purchase a large number of accounts (in order to warn their customers about potential problems).
Thus, Cyble was able to acquire information about approximately 530,000 Zoom accounts for the price of only $0.0020 per account.
Researchers bought the data including email addresses, passwords, meeting URLs, and hostkeys. Among these accounts were found those belonging to such well-known companies as Chase and Citibank, large educational institutions and many more. In addition, the researchers were able to confirm the authenticity of the data by checking the accounts owned by the company’s customers.
“Reusing the same passwords is a bad idea, and we recommend that users, which practice this, should change passwords as soon as possible”, – remind information security specialists.
While Google, SpaceX and NASA employees refuse to use Zoom, and cybercriminals spread malware through fake Zoom domains, we recommend avoid using this application at all.





