Malwarebytes experts discovered that MageCart hackers use a kind of steganography and hide web skimmers in EXIF image metadata and use images to extract stolen data.
Initially, the name MageCart was assigned to one hack group, which first began to use the so-called web skimmers on websites to steal bank card data. Hackers hack sites and then inject malicious code in their pages. Code writes and steals payment card data when users enter them during checkout.“This approach was so successful that the group soon got numerous imitators, and the name MageCart became a common name, and now it indicates a whole class of such attacks“, — say in Malwarebytes.
If in 2018 RiskIQ researchers identified 12 such groups, at the end of 2019, according to IBM, there were already about 40 of them. Hackers even inbuilt script Magecart to collect bulling information on Forbes subscription website.
Let me remind you that recently, Malwarebytes experts have already talked about the MageCart campaign, for which the hack group created a malicious site to host favicon and mask malicious code. A new expert report talks about similar malicious activity.
In an open directory of an unnamed compromised site, researchers were able to find a copy of the source code for the skimming kit, which allowed gathering a lot of new information and notice that the usual favicon.ico file contains an embedded script inside the Copyright field.
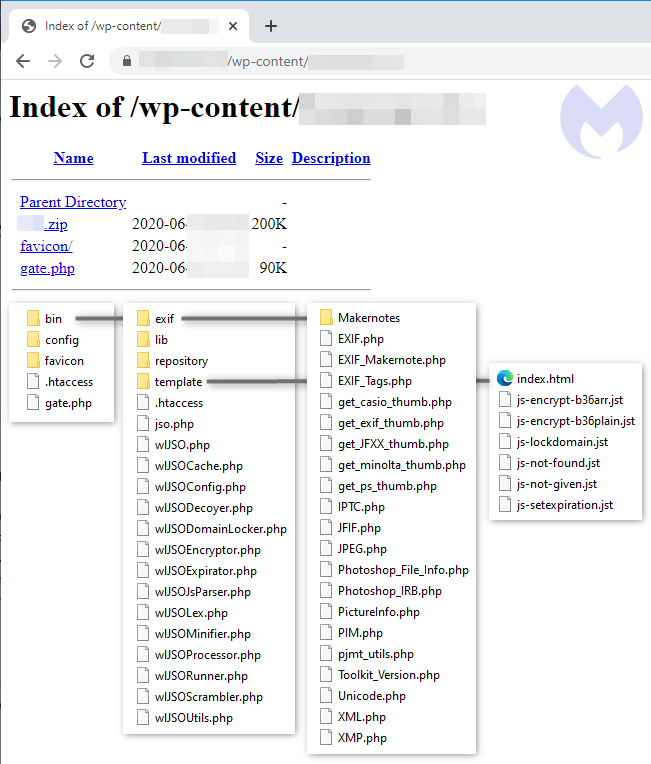
According to experts, the attack of cybercriminals has the following structure: the web skimmer was found in the metadata of the EXIF file, which was downloaded by hacked online stores with the WooCommerce plugin for WordPress on board. Extraneous code for downloading a dangerous image was added to a legitimate script, store owners themselves posted on websites.
It was possible to trace malicious activity to the site cddn[.]site, from which the malicious favicon file was downloaded. As it turned out, the attackers used favicon, identical to those in compromised stores, and the web skimmer was loaded from the Copyright field in the image metadata using the tag.
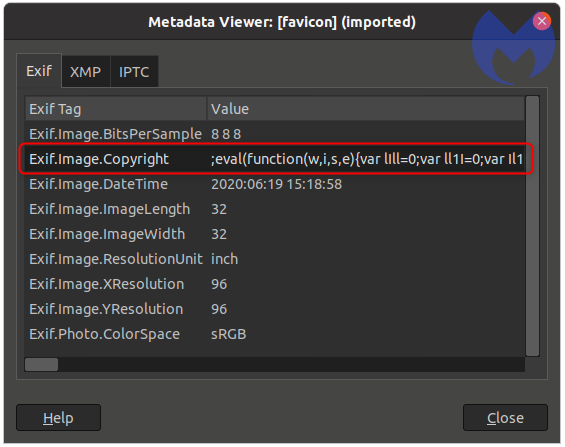
As you might guess, this web-skimmer, like other similar malware, stole the contents of input fields, where customers entered their name, billing address, credit card information and so on.
“When the information was collected, the skimmer encrypted the collected data, turned the line over and through the POST request sent the stolen information to the remote server as an image file”, – told Malwarebytes experts.
Obviously, the attackers decided to be consistent and used pictures to hide data at all stages of the attack.
Malwarebytes experts were also able to discover an early version of this skimmer, in which there was no obfuscation inherent in the latest iteration. In general, this version had the same functions, but studying behavior of both variations of the malware allowed concluding that this development may belong to the MageCart group number 9.