We recently talked about a bug discovered in the GO SMS Pro Android app, installed over 100,000,000 times. Due to the vulnerability, application data (voice messages, videos and images) exchanged by users can be available to everyone.
Trustwave researchers who found the bug wrote that even those files that were intended for users without installed GO SMS Pro can be extracted from the application server. To do this, can be used a shortened URL like https://gs.3g[.]cn/D/dd1efd/w, which is applied to redirect to the CDN used by the application for shared files. Such URLs are generated sequentially and predictably for each shared file when that content is stored on a CDN server.“As a result, a potential attacker is able to view these files without even knowing the URLs themselves and without any authentication”, – said the Trustwave expert.
Unfortunately, the problem is still relevant and the private messages of millions of users are available to anyone. The fact is that a new version of the app was uploaded to the Play Store the day before the Trustwave researchers’ report was published, and then, on November 20, Google removed the app from the Play Store (the day after the report was published).
Although the app was eventually restored, the researchers explain that the updated version only partially fixed the problem: all user media is still available, although content sharing is disabled in the latest version of GO SMS Pro.
Unfortunately, users who have already shared confidential files via GO SMS Pro do not have the option to delete them from the application servers. In essence, the developers of the application were unable to block access to millions of personal photos, videos and voice messages uploaded before the bug was partially fixed.
Therefore, anyone can still download these files using a simple script that generates a list of URLs that link to photos and videos published using vulnerable versions of the application.
“Unfortunately, we are seeing vigorous activity related to this vulnerability. Sites such as Pastebin and Github have more tools and scripts to exploit the problem than you might imagine”, — write Trustwave.
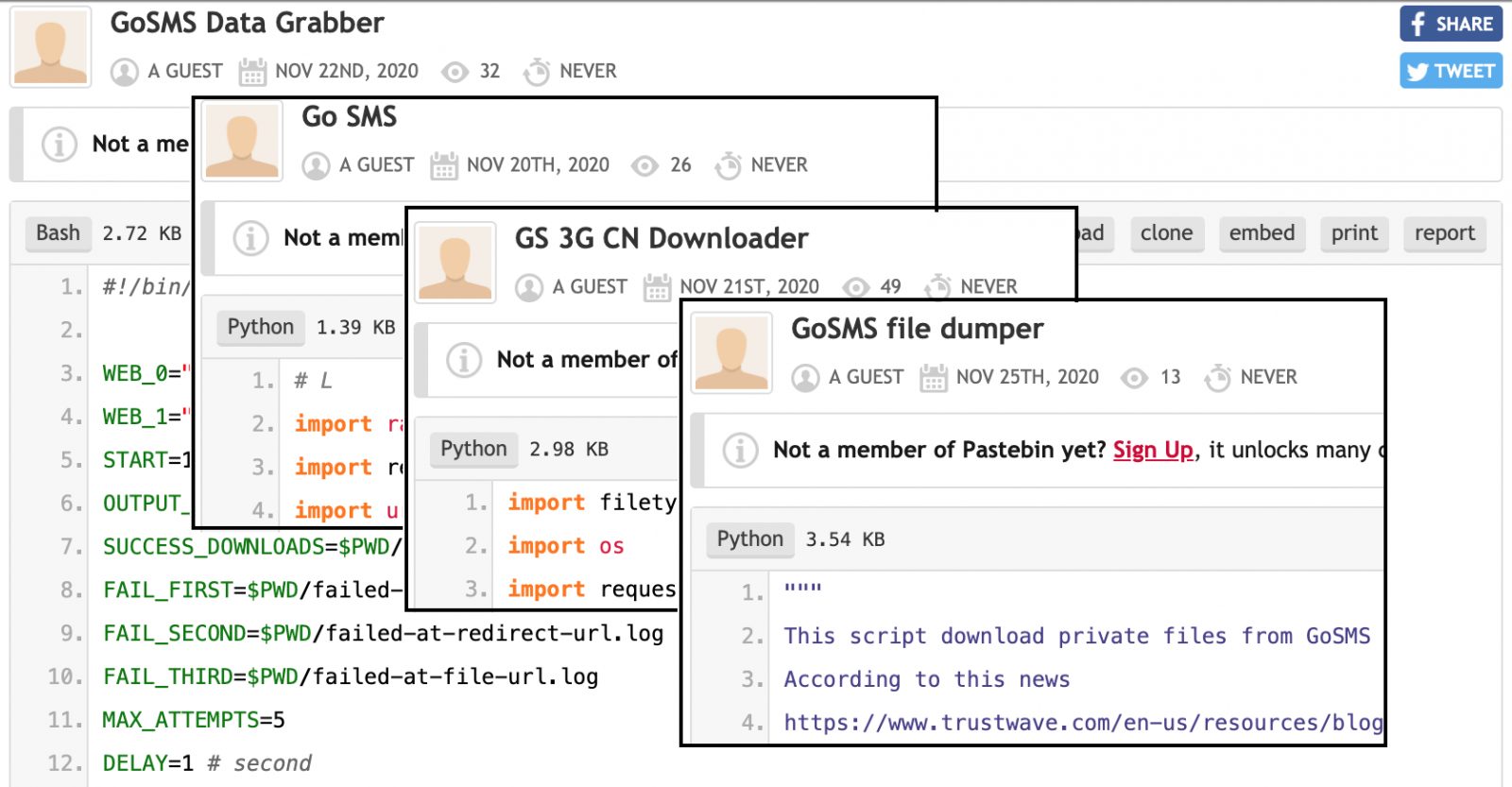
What is worse, according to analysts, images downloaded from GO SMS Pro servers are already circulating on the black market, and the developers of several scripts for downloading data and downloading private messages update them almost daily. Although not all leaked media are associated with specific users, some of them contain faces, names, and other identifying characteristics of people. Other files include driver’s licenses, health insurance account numbers, legal documents, and more “romantic” content.

The researchers note with regret that even removing the application from the Play Store will not solve this problem.
Although the GO SMS Pro developers are definitely aware of the problem and are even trying to fix it, Trustwave writes that they never received a reply from them to any of their emails.
Let me also remind you that a similar problem was found in WhatsApp: bug allows changing text of messages and sender’s identity.





