In March 2020 arrived information about the problem CVE-2020-0796, which is also called SMBGhost, CoronaBlue, NexternalBlue and BluesDay. The problem affects SMBv3, and Windows 10 1903, Windows 10 1909, Windows Server 1903, and Windows Server 1909 were vulnerable to the bug. A working RCE exploit for the SMBGhost problem has now been published on the network.
Let me remind you the SMB protocol several years ago was used to distribute WannaCry and NotPetya around the world.“The vulnerability is a buffer overflow on Microsoft SMB servers. The problem manifests itself when the vulnerable software processes a malicious packet of compressed data. That is, a remote and unauthenticated attacker can use a bug to execute arbitrary code in the application context“, – said Fortinet researchers about this bug.
Back in March, Cisco Talos experts warned that “exploiting the vulnerability opens up systems for attacks with worm potential.”
Although emergency patches for fixing CVE-2020-0796 were released in March of this year, information security specialists were still very concerned about this problem. The fact is that not all user received notification about the timely installation of patches, and according to Kryptos Logic, until recently, you can find about 48,000 hosts with an open SMB port on the Internet that are vulnerable to potential attacks using SMBGhost.
Fortunately, until recently was not published any public RCE exploit for this vulnerability.
“So, in early April, were published the first PoC exploits, but they only helped achieve denial of service (DoS) and local privilege escalation (LPE)”, — says Bleeping Computer magazine.
These exploits are already used in real attacks (for example, the Ave Maria malware uses them to increase privileges), but by the degree of danger they are far from RCE.
An RCE exploit for SMBGhost also existed, it just didn’t appear in the public domain. So, in April 2020, it was created and demonstrated by an expert from the company Ricerca Security: the researcher showed the operation of the exploit in the video and published its detailed description. However, then Ricerca Security did not publish the source of the exploit in the public domain, as experts were afraid to put such a dangerous tool in the hands of criminals.
Now, almost three months after Microsoft released the patches, Bleeping Computer reports that an information security specialist known as Chompie1337 has posted the first publicly available version of the RCE exploit for CVE-2020-0796 on GitHub.
The fact is that the specialists of the information security company ZecOps also announced the creation of an RCE exploit in April, and promised to publish it after the next Windows update. Chompie1337 believes that this should happen in a few days, so she decided to post her development in the public domain.
So far, the exploit code cannot be called completely stable, and the researcher says that it is more likely to help others expand their knowledge in the field of reverse engineering, as well as “it was written quickly and needs more work to become more reliable.” The best exploit works against Windows 10 1903.
“Sometimes BSODs are possible. Using this [exploit] for any purpose other than self-educational is a very bad idea. Your computer will light up. Puppies will die”, — writes Chompie1337.
CERT/CC analyst Will Dormann already checked the researcher’s code on a computer running Windows 10 1909 and received conflicting results.
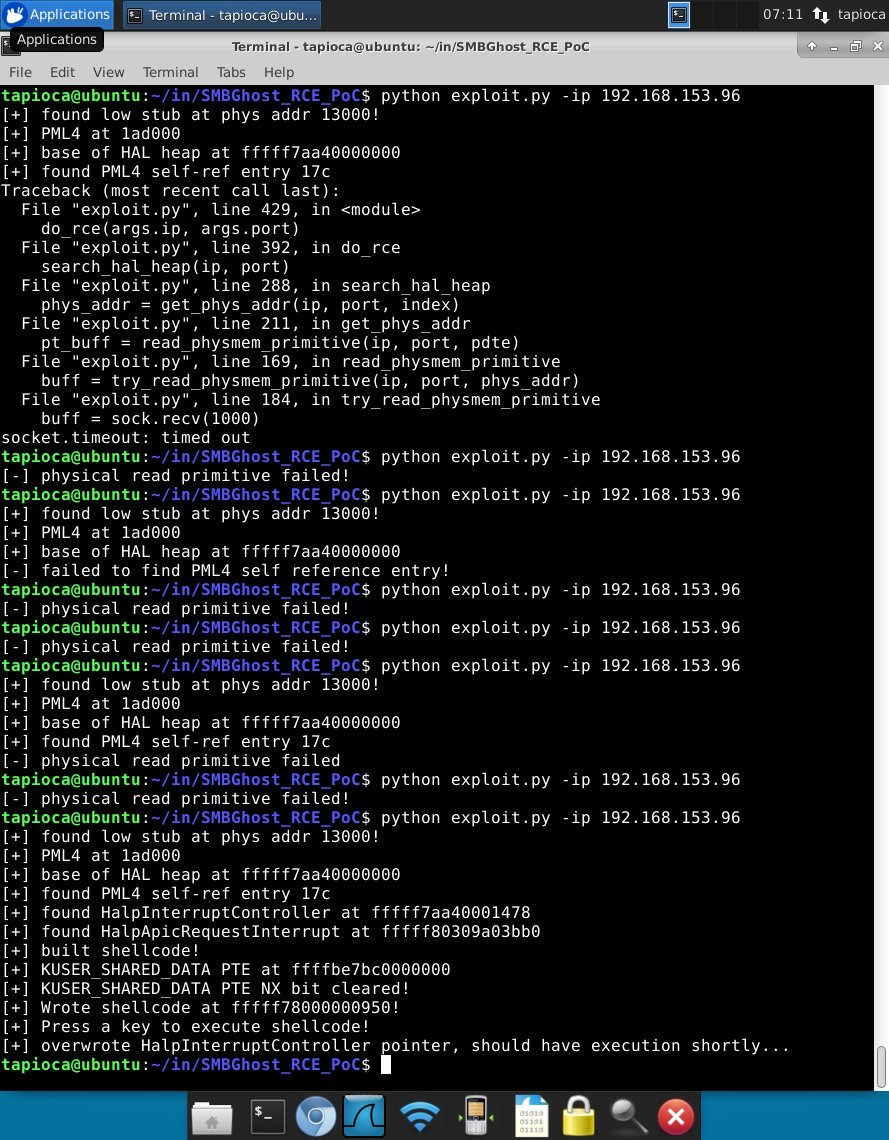
So, sometimes an exploit can lead to a crash of the test system, and sometimes it just doesn’t work.
At the same time, Dormann notes that from the point of view of the attacker, the exploit does not have to be 100% reliable. Failure in this case is nothing more than the threshold of the next attack attempt. If the exploit does not work, nothing prevents the attacker from continuing to try until he achieves the desired effect. Worse, trained attackers with the proper skills can modify the exploit themselves.





