ESET experts reported that an extraordinary attack on the supply chain was carried out by unknown hackers in Vietnam.
Unknown hackers have embedded malware into applications distributed by the Vietnam Government Certification Authority (VGCA) – this government organization issues digital certificates that can be used for creating electronic signatures.As a result, both private companies and government agencies suffered from the compromise. The researchers named this hacking operation SignSight.
“Any Vietnamese citizen, company and even government agency that wants to send files to the Vietnamese government is required to sign their documents with a VGCA compliant digital certificate”, – say ESET representatives.
However, VGCA not only issues certificates, but also provides ready-made “client applications” that citizens, companies and government officials can install on their computers and automate the process of signing documents.
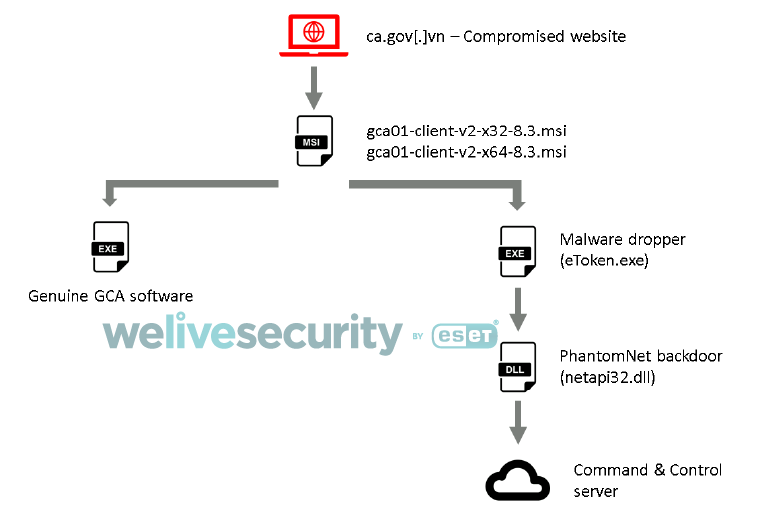
ESET analysts say that such applications were compromised by unknown attackers. Earlier in 2020, hackers broke into the VGCA website (ca.gov.vn) and injected malware into applications that could be downloaded from the site. The files gca01-client-v2-x32-8.3.msi and gca01-client-v2-x64-8.3.msi intended for Windows systems were infected.
“Between July 23rd and August 5th, 2020, these files contained the PhantomNet backdoor Trojan, also known as Smanager”, — the researchers report.
In their report, experts describe this malware as not too complex and conclude that it was used as a framework for more powerful plugins. In particular, PhantomNet plugins were able to obtain proxy settings for bypassing corporate firewalls, and were also able to download and run additional malware. It is assumed that all of this was used to conduct reconnaissance in the networks of victims and prepare for more serious attacks.
Interestingly, PhantomNet infections have also been identified in the Philippines, but how these users were compromised is not yet clear. Experts believe that a different malware delivery mechanism was used for these attacks.
The researchers report that in December 2020, they notified the VGCA of the compromise, but by that time, the certification centre already knew about the hack. Simultaneously with the publication of the ESET report, VGCA representatives officially announced the hack and prepared a guide for victims, instructing how to remove the malware.
Although ESET does not draw any conclusions in its report regarding the attribution of this malware in particular and the malicious campaign in general, previous reports from researchers usually associate PhatomNet (Smanager) with cyber-espionage activities of Chinese hackers.
Let me remind you that Lookout experts discovered link between Chinese hackers and a defence contractor. Additionally, Microsoft linked Vietnamese government hackers Bismuth to mining campaigns.





