Hackers Broke into the Home PC of the Developer of the LastPass Password Manager and Penetrated the Company’s Cloud Storage
Increasingly vexing details of the LastPass password manager hack, which was first reported last year, continue to emerge. The company now says the same attackers compromised an employee’s home computer and, as a result, stole data from LastPass cloud storage on Amazon AWS for two months.
By the way, we wrote that Phishers Target Users Affected by the Passwordstate Hack, and also that only 26% of users agreed to change their password when they learned that it was compromised.Let me remind you that in December 2022, LastPass developers reported that unknown attackers hacked into the company’s cloud storage and gained access to customer data. It is noteworthy that for this hack, the hackers used data stolen from the company earlier, during a previous attack that occurred in August 2022.
At the same time, it was reported in December that not only corporate data was affected by this hack, but also customer data, including password vaults, which could theoretically be hacked.
Now, LastPass has released new details of this hacking spree, and it turns out that things are even worse than previously thought.
According to the company’s specialists, the attackers used information stolen during the August incident, as well as data obtained during another hack, and an RCE vulnerability in a third-party multimedia software package (according to media reports, we are talking about Plex) to install a keylogger on the computer of a senior DevOps -LastPass engineer.
The company calls what happened the second coordinated attack aimed at gaining access to encrypted LastPass buckets in Amazon S3. Since only four engineers had access to the required decryption keys, the attackers targeted one of them. As mentioned above, the attack was successful, and as a result, a keylogger was installed on the developer’s personal machine.
Usage of the real credentials of one of the employees made it difficult to detect the actions of the attackers. As a result, hackers maintained access to and stole data from LastPass cloud storage servers between August 12, 2022 and October 26, 2022.
The anomaly was discovered only after warnings received from AWS GuardDuty, when attackers tried to use Cloud Identity and Access Management (IAM) roles to perform unauthorized actions.
The company said in a statement that it has since upgraded its security system, rotated sensitive credentials as well as authentication keys and tokens, revoked a number of certificates, added additional logs and warnings, and generally adhered to stricter security policies.
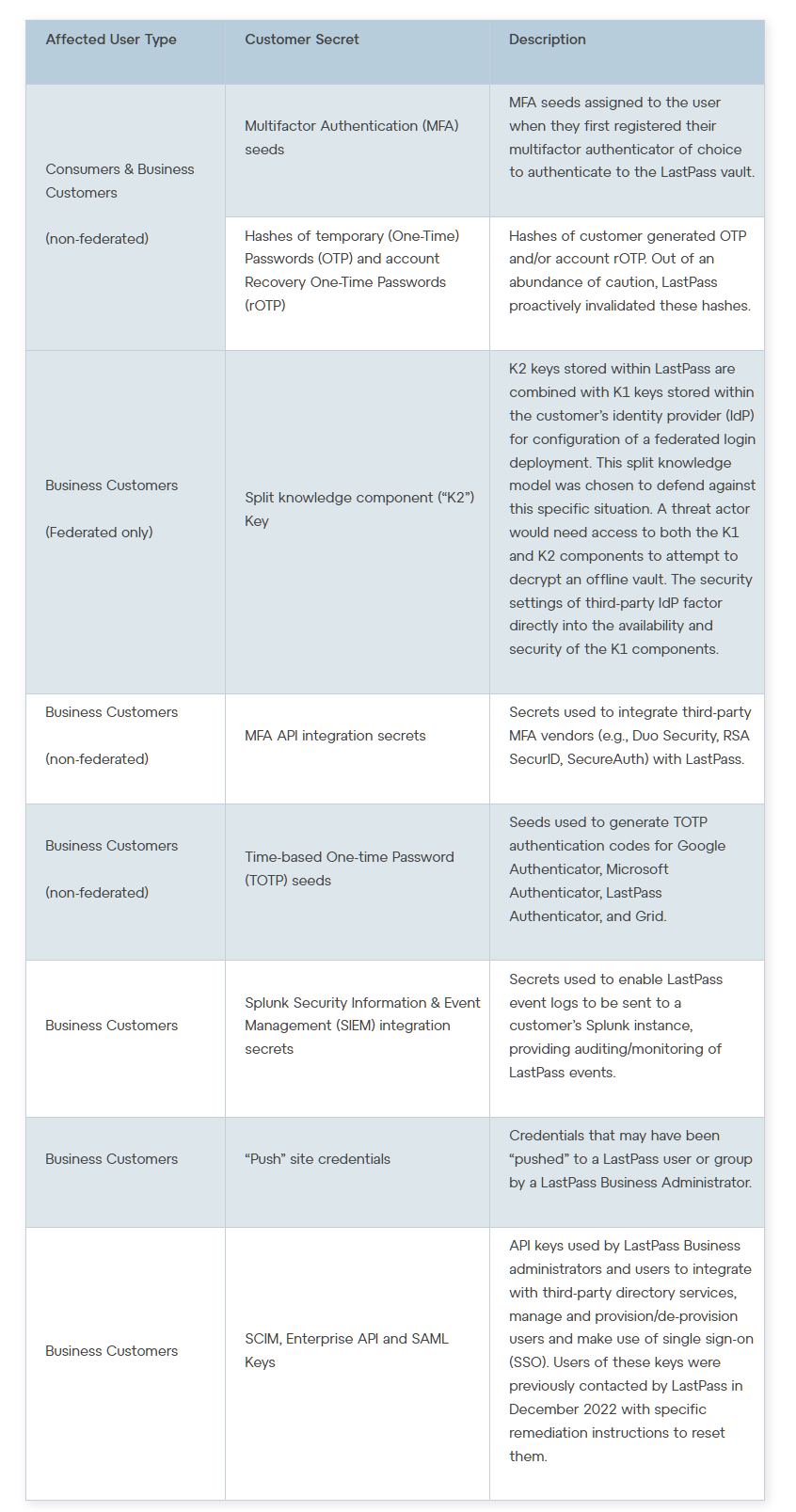
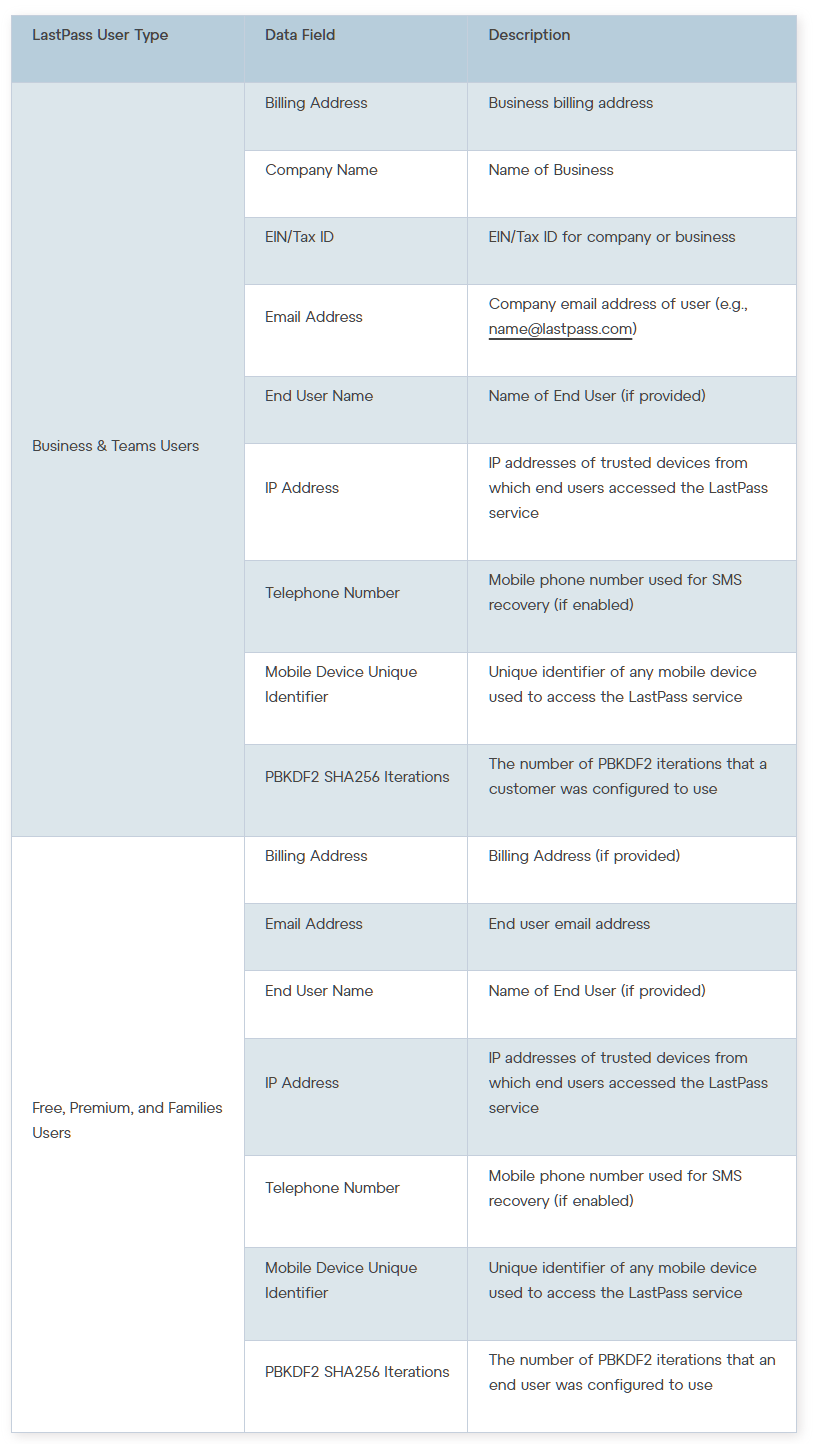
Representatives of LastPass attached to their statement a list of data stolen by hackers. According to it, it turned out that, among other things, the attackers had access to encryption keys for backup copies of customer storages.
In general, LastPass customers could have been affected to varying degrees, as there was a lot of stolen data: ranging from multi-factor authentication (MFA) seeds, MFA API integration secrets, to business customer K2 keys, as well as customer metadata and backups of all data customer storage.