Lookout experts published a 52-page report that details the multi-year campaign aimed at the Uighurs, Muslim minority living mainly in western China. Lookout experts describe a link between Chinese hackers who led this campaign and a defense contractor.
As part of this campaign, citizen’s devices since 2013 have been infected with malware, which allowed hackers to monitor the activities of Uyghur communities in the border regions of China and abroad in at least 14 countries.Recall that also the Chinese Bank was recently caught on the fact that it installs tax software with a backdoor to Western companies.
Lookout is confident that a hacker group operating under the auspices of the Chinese government is standing behind this campaign.
“Some of the previous operations of this group were documented by other information security experts, and in the past the group received code names such as APT15, GREF, Ke3chang, Mirage, Vixen Panda and Playful Dragon”, – say Lookout experts.
Most of the past APT15 attacks were related to Windows malware, but Lookout has now reported that Android tools are also in the arsenal of hackers. Some of them were already known to experts earlier, including such types of malware as HenBox, PluginPhantom, Spywaller and DarthPusher. But besides this, Lookout analysts also discovered four new malware: SilkBean, DoubleAgent, CarbonSteal and GoldenEagle.
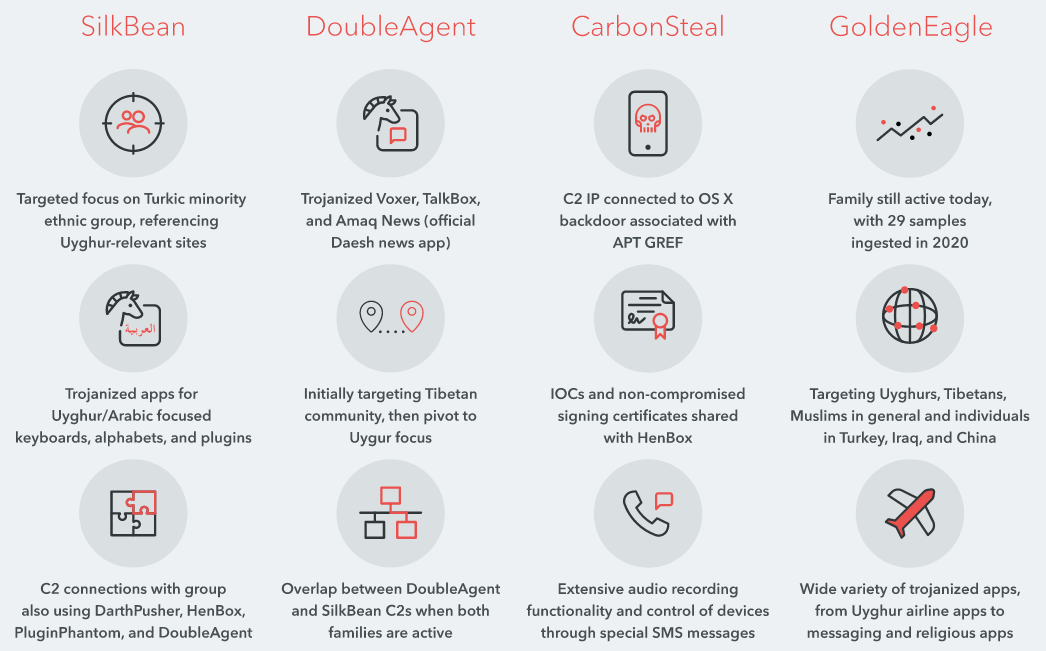
These new varieties of Android malware were able to be associated with other well-known APT15 tools, as they use a common infrastructure and the same digital certificates for signing samples.
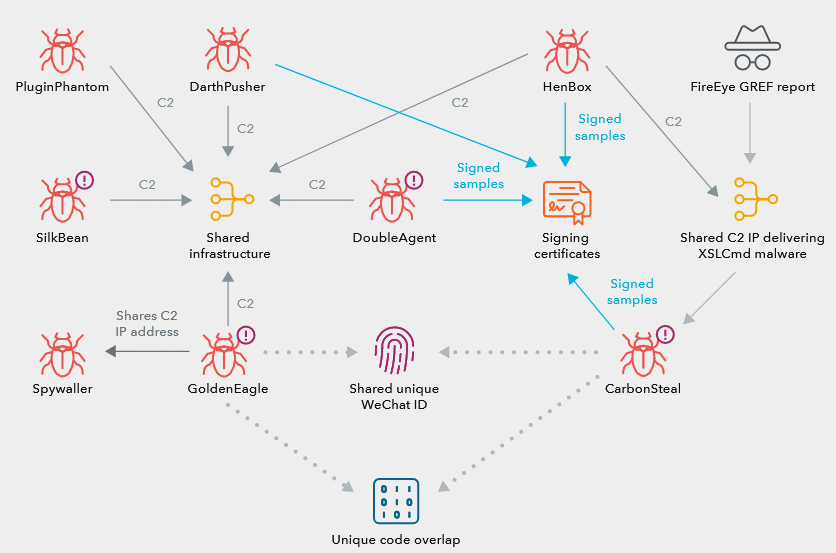
Researchers note that APT15 did not upload its malicious applications to the Google Play Store, but hacked into various legitimate sites and used the watering hole technique. Such attacks are called by analogy with the tactics of predators who hunt at a watering hole, waiting for prey – animals that came to drink. Thus, malicious code was injected into legitimate sites that redirected visitors to pages, forums, application stores and other sites where they were asked to download and install applications infected with APT15 malware.
“In the early stages of exploring the new APT15 malware, they discovered the GoldenEagle spyware management server, which hackers mistakenly left unprotected”, — say Lookout researchers.
Researchers gained access to this server and collected information about both hacker victims and malware operators.
Looking through the obtained logs , the researchers found data from the first devices infected with GoldenEagle. It turned out that the GPS coordinates obtained from these devices are concentrated around the same area. Soon, it was possible to understand that these were the GPS coordinates of the building in Xi’an, central China, where the office of Xi’an Tianhe Defense Technology, a major military contractor, is located.
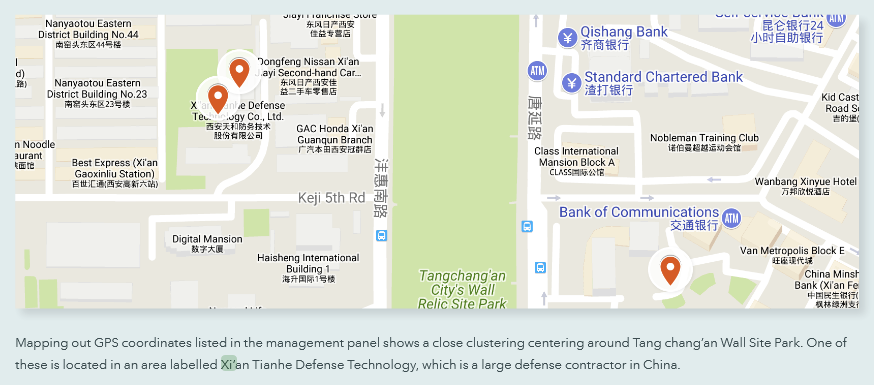
Researchers believe that these initial infections can be related to devices infected at an early stage in the development of malware. In combination with their GPS coordinates, we can assume that these are test devices on which the developers of the GoldenEagle malware tested effectiveness of their malicious programs. The developers seemed to be the engineers at Xi’an Tianhe Defense Technology.
I must say that this is not the first exposure of this kind. So, for many years now, the Intrusion Truth group has deanonymized the Chinese “government hackers.” Between 2017 and 2019, Intrusion Truth linked four hacker groups to various Chinese intelligence contractors:
- APT3 – affiliated with Boyusec, which cooperates with the Chinese authorities and is associated with state security in Guangdong Province;
- APT10 – associated with a number of companies that cooperate with the Chinese authorities and are associated with state security in the city of Tianjin;
- APT17 – is associated with a number of companies that cooperate with the Chinese authorities and are associated with state security in the city of Jinan;
- APT40 – associated with a number of shell companies that collaborate with the Chinese authorities and are associated with state security in Hainan.
I also recall that information security experts suspect Chinese company Xiaomi of spying on users.





