ESET experts discovered the malware, which is used by the hack group Evilnum, aimed at fintech companies and their customers, and talked about the activity of this group, which exists since 2018. ESET found that the same people are developing malware for both Evilnum hack group, FIN6 and Cobalt.
According to researchers, the largest number of Evilnum attacks is concentrated in the EU and the United Kingdom, several attacks are also recorded in Canada and Australia.Evilnum malware is focused on the theft of all kinds of confidential data. Like many other financial hackers, this group seeks to infiltrate corporate networks, gain access to credentials and steal valuable financial information, which can then be used for fraudulent purchases or sold in bulk to other criminals.
So, Evilnum is interested in:
- information on customer bank cards and identification documents;
- spreadsheets and documents with lists of clients, information about investments and trading operations;
- internal company presentations;
- software licenses and credentials for trading software/trading platforms;
- Email credentials.
Evilnum operators can also collect information related to the IT infrastructure of the victim company, such as VPN configurations.
Interestingly, according to ESET, behind the development of the malware for the Evilnum group stand hackers from the Golden Chickens group, working according to the malware-as-a-service scheme. These same people are malware providers for such well-known hack groups as FIN6 and Cobalt.
Their tools include ActiveX components (OCX files) containing TerraLoader, and a dropper for other malicious programs available to Golden Chickens clients (for example, the More_eggs backdoor and complex RAT malware).
“We believe that FIN6, Cobalt and Evilnum are not the same thing, despite all the coincidences in their toolkits. It just so happened that these groups have the same MaaS provider”, — write the experts and note that while the Evilnum group can hardly be associated with other well-known APTs.
Typically, an Evilnum attack involves the following steps: the user receives a phishing email with a link to Google Drive, from which can downloaded a ZIP file. This archive contains several LNK files (shortcuts) that extract and launch a malicious JavaScript component when displaying a bait document.
Bait files, in turn, are disguised as very interesting things, and the letters themselves were supposedly written by representatives of technical support and customer service managers.
As a rule, files are various KYC-information (Know Your Customer): photographs of bank cards, identity documents, or address-confirming bills, as many financial institutions require their clients to provide such data.
Essentially, if a victim opens a malicious document, are launched Evilnum malware, Python tools, and components created by Golden Chickens. For example, the mentioned JavaScript component is able to deploy additional malware in the victim’s system. In addition, each of the components has its own control server and can act independently.
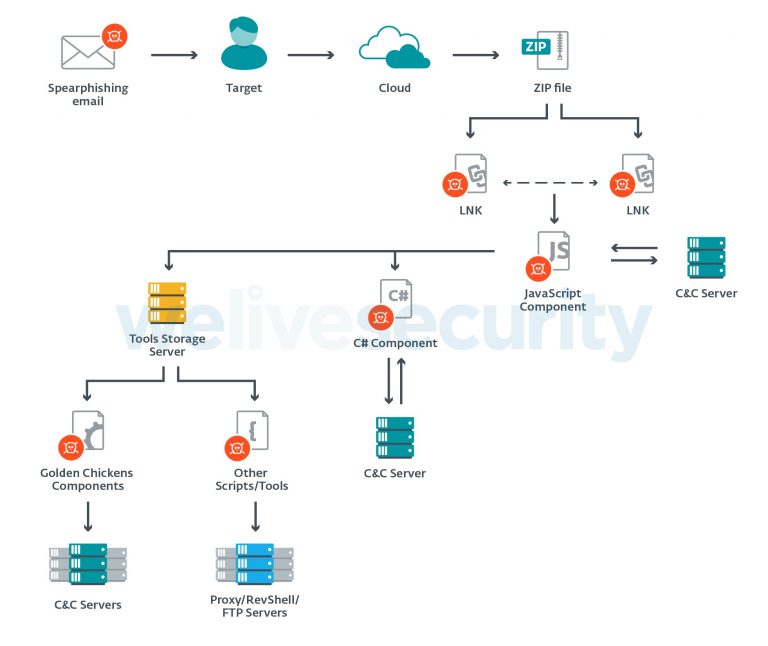
Evilnum’s main payload is aimed at collecting various confidential information, which was already mentioned above, including theft and sending of passwords stored in Google Chrome, cookies from Google Chrome to the management server, as well as saving screenshots.
Cybercriminals are not particularly happy when their actions are detected and even sometimes take revenge – I recall that recently ESET security company became a victim of a DDoS attack.





