ESET expert Lucas Stefanko told in the company’s blog about the malicious application Updates for Android, which launched a DDoS attack on the ESET website.
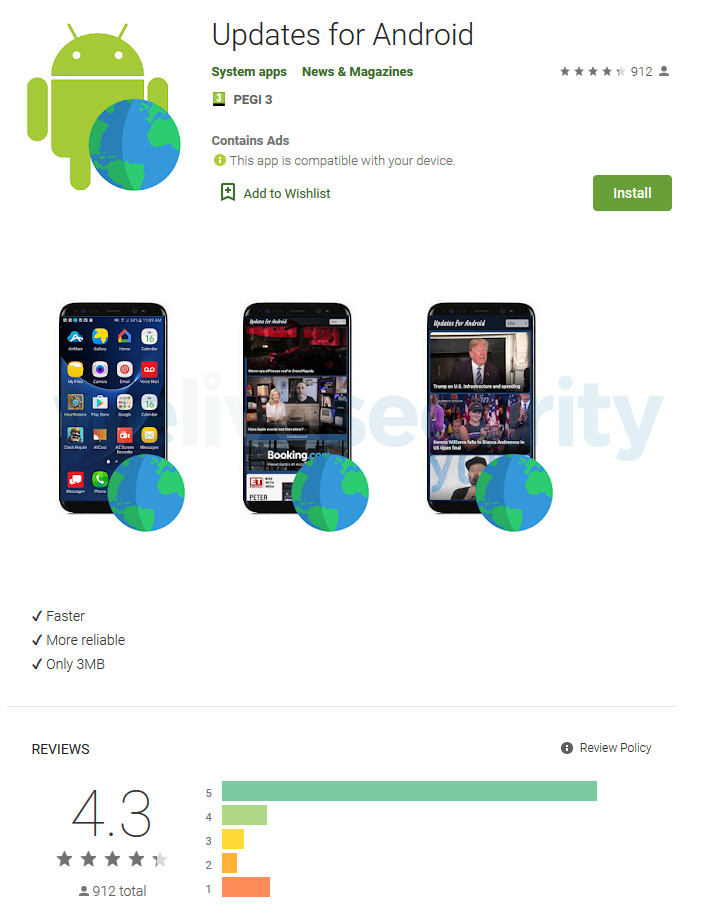
Initially, the application promised to provide users with an updated news feed from i-Updater[.]Com. The site still works, as it is not malicious itself.The application arrived on Google Play in September 2019, was installed more than 50,000 times and had good reviews (average score 4.3), but secretly from users it was used to conduct DDoS attacks, for which were used about 10% of users devices.
The researcher also notes that the name of the product has already misled people.
“Immediately after downloading and installing Updates for Android, it did not have any malicious functionality, which helped it bypass the protection of the official application directory. Malicious features appeared after only one update”, – says Lucas Stefanko.
In fact, the malicious functionality was simple: the application was able to download JavaScript code from the attackers’ server and run it on a user device. In addition, after the update, the application checked for new commands on the management server every 150 minutes, and the identifier of each device with an active installation was transferred to the same server.
As a result, based on the commands received from operators, Updates for Android could display ads in the user’s browser, hide its presence from the user, and execute arbitrary JavaScript on the device.
JavaScript execution functionality that was used to conduct the DDoS attack on the ESET website (eset.com), which occurred in January 2020. The attack lasted seven hours and was carried out using 4000 unique IP addresses.
Overall, DDoS attacks began with the hacked device receiving a command to load a script that pointed to the target domain. After that, the infected device sent requests to the target domain until the C&C server provided another script. As a result, infected devices connected to the target site every second to create an excessive load on the resource.
“ESET experts witnessed the work of six more such scripts, each of which contained a new target domain for the devices included in the botnet. Were attacked famous news sites and e-commerce sites, most of which are located in Turkey”, – notes Lukas Stefanko.
Since February 2, 2020, the script has been distributed empty, which means that attackers tried to exploit their botnet for two more days after Google stopped Updates for Android.
Let me remind you that China declared a real war on DDoS services, and in a rather non-obvious way, they decided to fight DDOS attacks in Ubisoft: DDoS attacks on Ubisoft almost completely stopped after company threatens with a lawsuit.