Yandex spoke about the largest DDoS attack in the history of the Internet
Yesterday, the media reported that Yandex was subjected to a powerful DDoS attack, behind which was an unnamed new botnet. The attack was called the largest in the history of Runet, but no details were known.
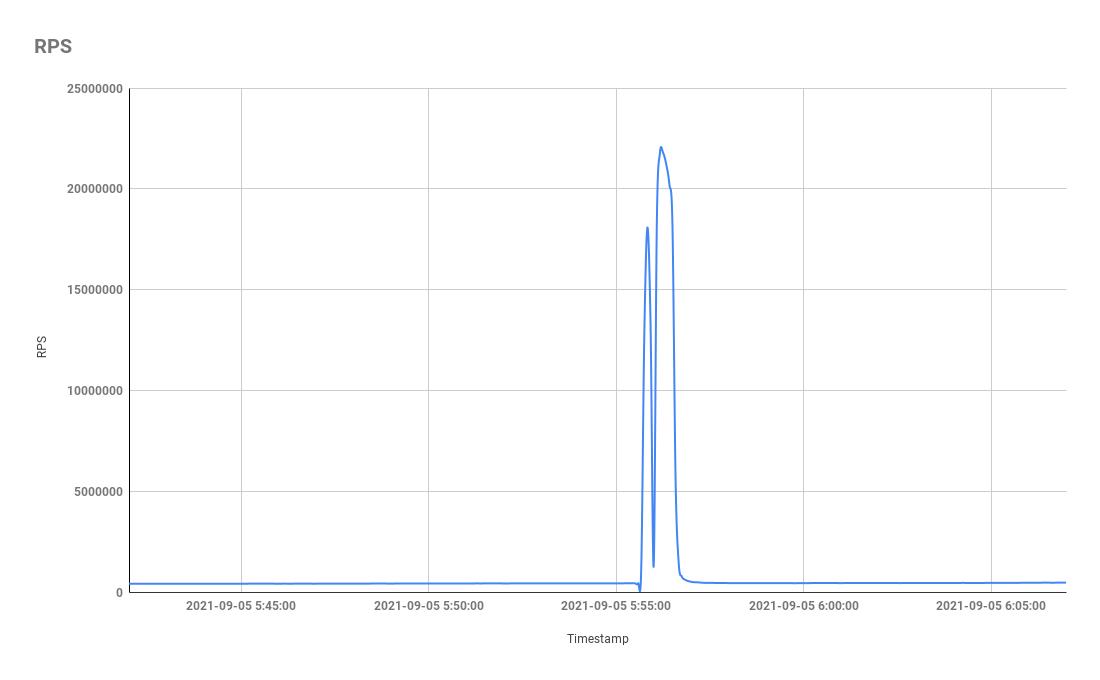
Today, representatives of Yandex and Qrator Labs published a large article on Habré, in which they shared the details of the incident: it turned out that the attack power was more than 20 million requests per second, and the Mēris botnet was behind it.The companies’ specialists note that the attack was not only the largest in the Russian Internet, but also set a new record among all DDoS attacks in general. The fact is that until recently, the largest attack in history was considered to be DDoS with a capacity of 17.2 million requests per second, which was reflected by Cloudflare this summer.
Currently, the statistics on the growth in the scale of attacks on Yandex are as follows:
- August 7 – 5.2 million RPS (Requests Per Second);
- August 9 – 6.5 million RPS;
- August 29 – 9.6 million RPS;
- August 31 – 10.9 million RPS;
- September 5 – 21.8 million RPS.
The Mēris botnet was spotted in July 2021, and initially Qrator Labs specialists observed 30,000 infected hosts, while Yandex collected data on 56,000 attacking devices. However, it is assumed that the number of bots actually exceeds 200,000.
While many believe that the new botnet is related to the well-known IoT malware Mirai, experts say that they have not yet had the opportunity to study a sample of malicious code, and they are not ready to claim that the botnet belongs to the Mirai family. So far, the researchers are generally sure of the opposite, since “the devices united under a single command center seem to belong only to the Mikrotik manufacturer.” At the same time, experts do not yet know which vulnerabilities lead to the fact that devices of the Latvian company Mikrotik are exposed to such large-scale attacks.
Among the most striking features of the new botnet, researchers list the following:
- use of pipelining (pipelining in HTTP / 1.1) for organizing DDoS attacks (confirmed);
- attacks focused on the exploitation of RPS (confirmed);
- open port 5678 (confirmed);
- SOCKS4 proxy on the infected device (not confirmed, although Mikrotik devices are known to use SOCKS4).
The botnet is known to continue to grow. Experts from Yandex and Qrator Labs believe that the problem is not just some old vulnerability in Mikrotik devices. The fact is that the current distribution of RouterOS versions in the botnet indicates that many devices using the OS of the last three years are infected, up to the latest stable version. The largest share falls on the penultimate version.
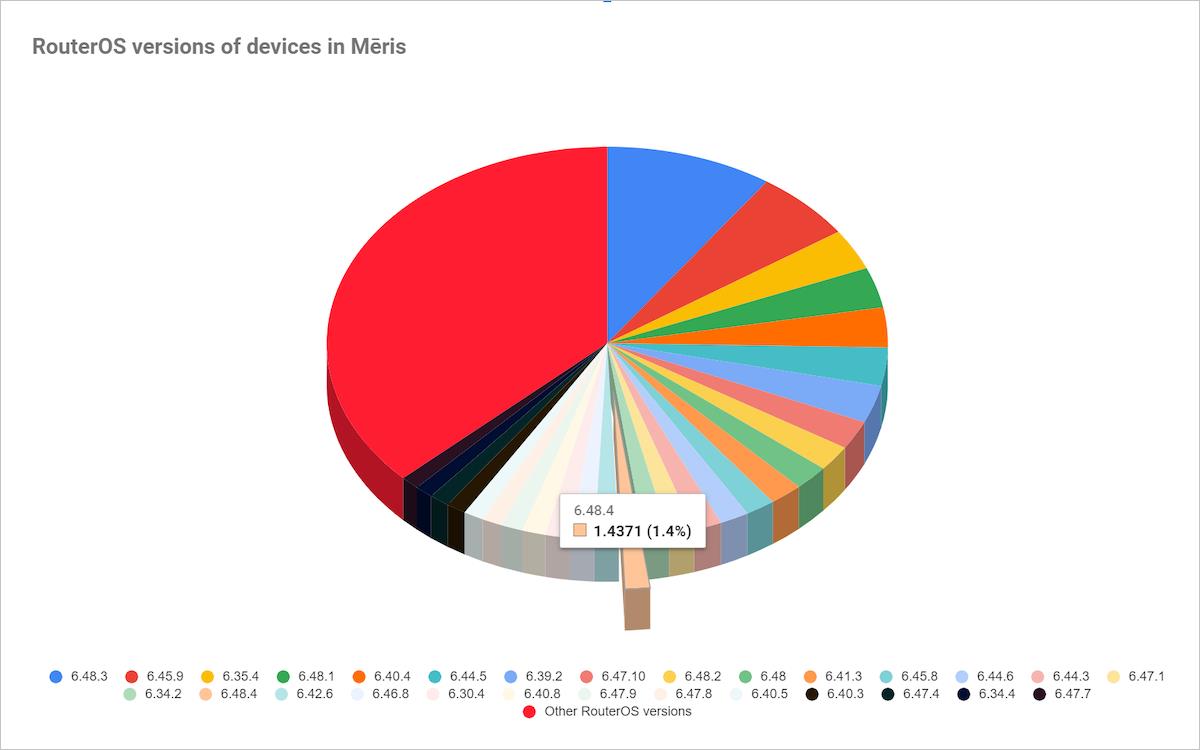
The researchers also say that Mēris can grow due to brute force, although this option is not the main one. The situation rather indicates that a certain vulnerability in Mikrotik equipment was either kept secret until the start of this full-scale campaign, or was sold on the black market.
Interestingly, the aforementioned 17.2 million requests per second attack recorded by Cloudflare is also attributed to the Mēris botnet. Yandex observed a similar pattern in terms of duration and distribution of source countries.
The same applies to the recent DDoS attacks in New Zealand, due to which the Internet in the country stopped working in some places, banks, post offices and so on arose problems.
Let me also remind you that we talked about AWS handled the most powerful DDoS attack in history, reaching 2.3 Tb/s.





