Check Point reports that it has discovered a new and dangerous version of the Qbot Trojan, which steals other people’s emails from Outlook and then uses them to create more convincing phishing emails.
Let me remind you that for the first time Qbot (aka QuakBot, QakBot and Pinkslipbot) was discovered back in 2008, and over the years it has evolved from an ordinary info-stealer into a real “Swiss knife” for hackers. Today, Qbot is capable, for example of delivering other types of malware to an infected system, and can even be used for remote connection to a target system to carry out banking transactions using the victim’s IP address.As a rule, Qbot spreads in a classic way: through phishing emails that contain dangerous attachments or lure users to malicious sites controlled by hackers”, — say Check Point researchers.
Check Point experts also write that the updated version of Qbot was activated between March and August 2020. In one of the campaigns, Qbot was distributed using Emotet and as a result of this “collaboration” in July 2020, attacks affected about 5% of organizations around the world.
A Qbot attack traditionally starts with sending of a malicious email to the user with a ZIP archive as an attachment. The archive contains a malicious VBS script that downloads additional payloads to the victim’s machine and communicates with the attackers’ command and control server.
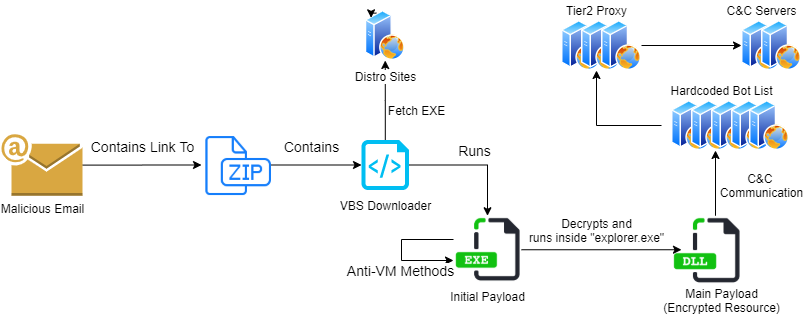
If such an attack is successful, Qbot, using a special module, collects chains of user emails from Outlook and sends them to a remote server. The stolen emails are then used by attackers to prepare new spam emails and help create more believable decoys.
For example, hackers are using thieves in ongoing campaigns, the topics of which are mainly related to the COVID-19 pandemic, reminders to pay taxes, and fake job offers”, – told at Check Point.
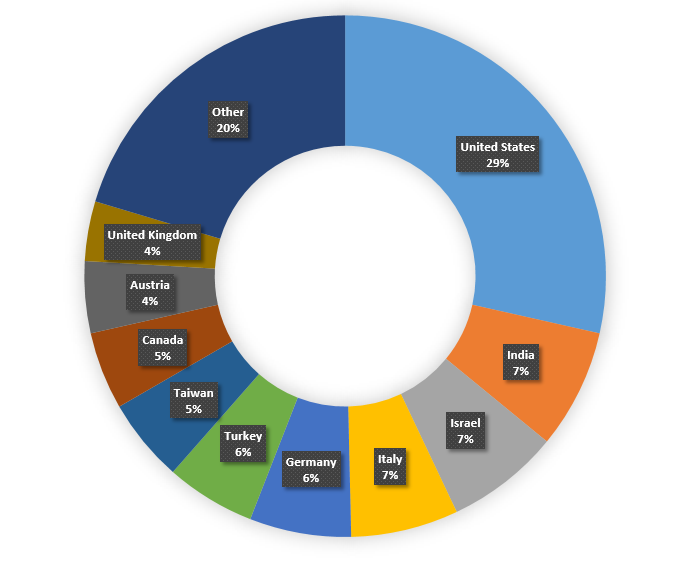
According to a Check Point study, the United States is currently the leading country in the number of Qbot attacks, with 29% coverage of organizations. This is followed by India, Israel and Italy, with a share of 7% each. The target industries for hackers were the government, military and manufacturing sectors.
Let me remind you that with the spread of this malware is associated an unusual story: unknown hackers interfere in the work of the Emotet botnet and Qbot by replacing malware with GIF files.





One Comment