Unknown hackers interfere in the work of the Emotet botnet by replacing malware with GIF files
Earlier this month, the Emotet botnet, which has shown no signs of life since February 2020, returned to service with a new spam campaign. However, not everything went smoothly with the cybercriminals – some unknown hackers interfere with the work of the Emotet botnet by replacing the malware with gif files.
After observing the malware, cybersecurity specialists reported that the botnet had changed its main payload and is now spreading the QakBot (QBot) banking trojan, which replaced the usual TrickBot botnet.However, now unknown well-wishers are successfully sabotaging the botnet.
Researchers from the Cryptolaemus group first noticed the strange activity, as they have been closely monitoring the botnet’s activity for several years and were trying to counteract it.
“Effective July 21, 2020, they replace Emotet payloads with animated GIFs, effectively preventing victims from getting infected. It is not yet clear who exactly is behind this action, it can be either competing hack groups or an unknown information security specialist”, – reported in Cryptolaemus.
According to them, currently about a quarter of all Emotet payloads are replaced with GIFs, which caused a significant decrease in botnet activity.
What happens is directly related to how the Emotet functions. For example, the botnet sends its potential victims spam containing attachments or links leading to malicious Office files. If you open such a file and enable macros, the actual payload will be downloaded from the remote source to the user’s machine.
The fact is that the botnet places such payloads mainly on hacked WordPress sites, which are accessed by Emotet operators through web shells.
“Moreover, cybersecurity experts have already discovered that cybercriminals use open source solutions for these purposes, and also use the same password for all web shells, thereby putting their infrastructure at risk”, – write Cryptolaemus researchers.
Apparently, now someone managed to find out a password, which is the same for all web shelves, and did not fail to use it. These “Good Samaritans” replace Emotet payloads on hacked WordPress sites with animated GIFs. Over the past three days, unknown people have replaced Emotet payloads with different GIFs. The files are usually taken from Imgur or Giphy.
So, on Tuesday, the payload was swapped with a file associated with Blink 182.
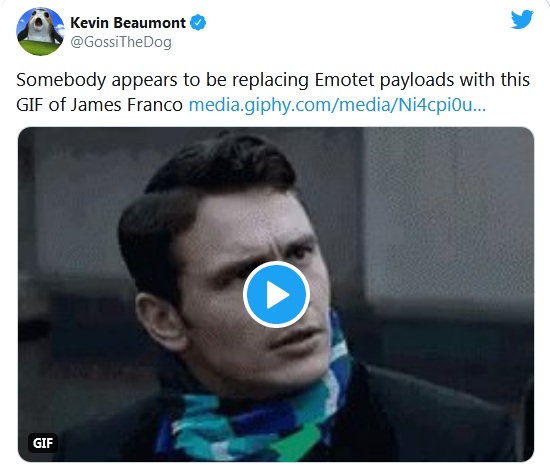
Then the unknown turned to using the image with James Franco.
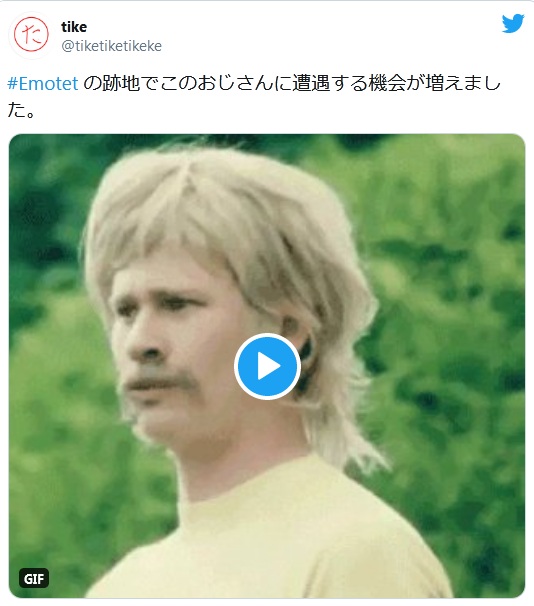
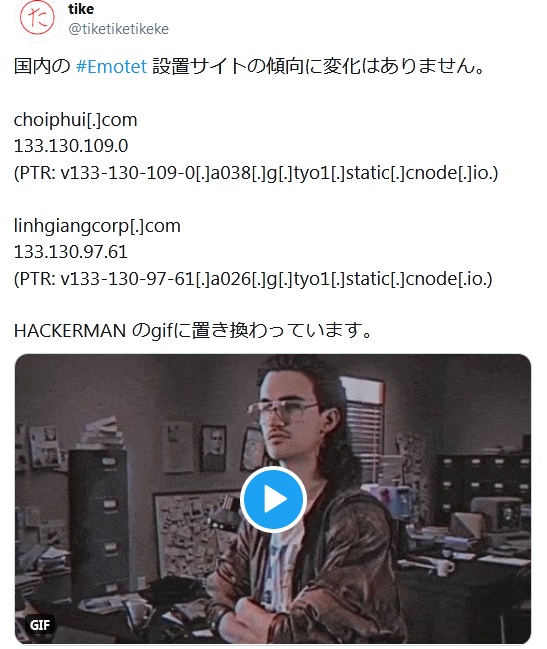
Later the trolling peaked, and appeared a Hackerman.
According to one of the Cryptolaemus contributors, Joseph Roosen, Emotet operators are well aware of this issue. The specialist told ZDNet reporters that the botnet went offline on Thursday, July 23rd, as hackers tried to “recapture” their web shells from saboteurs. Despite their efforts, unknowns today continue to change the payloads of GIF files, although Emotet operators have begun restoring the original payloads much faster than before.
Rosen estimates that Emotet is currently running at about a quarter of its normal capacity as hackers are still battling for control of web shells.





