Microsoft engineers presented a report at the RSA conference, according to which 99.9% of compromised accounts did not use multi-factor authentication, which can stop most automatic attacks on accounts.
The technology giant reported that it tracks over 30 billion login events and more than one billion monthly active users every day.“On average, about 0.5% of all accounts are compromised every month, and in January 2020 their number was about 1.2 million”, — Microsoft said.
Although hacking of any account is bad, Microsoft separately monitors compromise of corporate accounts, which the company considers highly sensitive.
Recall that Google also claims that only 26% of users agreed to change their password when they learned that it was compromised.
According to analysts, of all compromised accounts, only 11% used multi-factor authentication (MFA) in January 2020.
In the majority of cases, hacking of accounts is possible in very simple attacks: the main source of most hacks are attacks using the password spraying technique. This is a method, in which attackers sort try to use different user names with the same simple, easily guessed password, hoping in this way to find a poorly protected account.
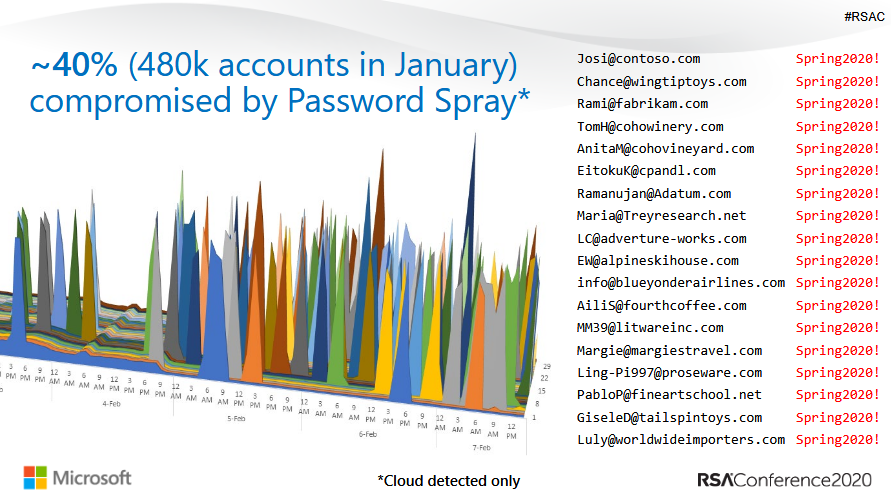
So far, we, an adware.guru team, have seen only one problem with multifactor authentication, and that was the fault of Twitter advertisers.
The second source of hacks, according to Microsoft’s presentation, is the problem of password reuse. In this case, the attackers take previously leaked credentials and try to use them for the Microsoft account, hoping that the user will reuse the same usernames and passwords again.
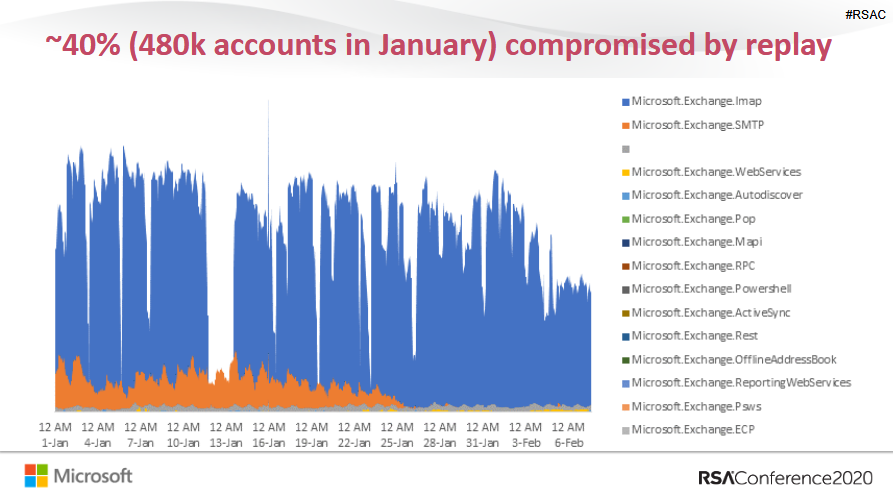
“We know that 60% of users reuse passwords. This is very common,” – says Microsoft. – Do not be embarrassed. People reuse their corporate accounts even in unincorporated environments.”
Most of these attacks target legacy authentication protocols such as SMTP, IMAP, POP, and so on. So, 99% of the total number of attacks using password spraying and 97% of attacks using reused passwords are carried out using outdated authentication protocols. The reason is that these legacy protocols usually do not support MFA, which makes them ideal targets for hackers.
Microsoft experts recall that companies that leave these legacy authentication protocols enabled for their cloud systems and networks are at risk of attack, and should disable them as soon as possible.