Magento fixes 0-day vulnerability under attack
Over the weekend, Adobe released an emergency update to fix a 0-day vulnerability in Magento and Adobe Commerce. The company warned that hackers have already abused the problem.
0-day has been identified as CVE-2022-24086 (CVSS 9.8 out of 10) and it is a bug that allows remote arbitrary code execution without authentication. According to Adobe, the root of the problem was incorrect input validation.
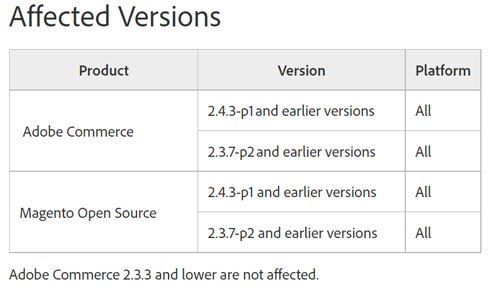
All sites and resources running Adobe Commerce and Magento Open Source versions 2.4.3-p1 and 2.3.7-p2 and below are considered vulnerable, and their administrators are advised to upgrade as soon as possible. It emphasizes that sites running Adobe Commerce 2.3.3 and earlier are not affected by the vulnerability.
It is noted that resource operators using Magento 2 (versions 2.3.3 to 2.3.7) can install the released patch manually, since this process requires changing only a few lines.
In a security bulletin, the company describes the attacks associated with this bug as “very limited” and related to Adobe Commerce, that is, the mass exploitation of the problem has not begun yet.
It is not yet clear how difficult it is to exploit CVE-2022-24086, but it appears to be a difficult process. Bleeping Computer quotes cybersecurity expert Willem de Groot, founder and managing director of Sansec, as saying that he has not yet seen the full chain of remote code execution attacks, indicating that “this is not a trivial exploit.”
You might also be interested to know that IS experts discovered a connection between North Korean hackers and MageCart attacks.





