Crowdstrike: the creation of the Chinese Comac C919 aircraft was accompanied by hacker attacks and cyber espionage
Crowdstrike experts published a voluminous report on the development of the Chinese Comac C919 aircraft: it was accompanied by hacker attacks and espionage.
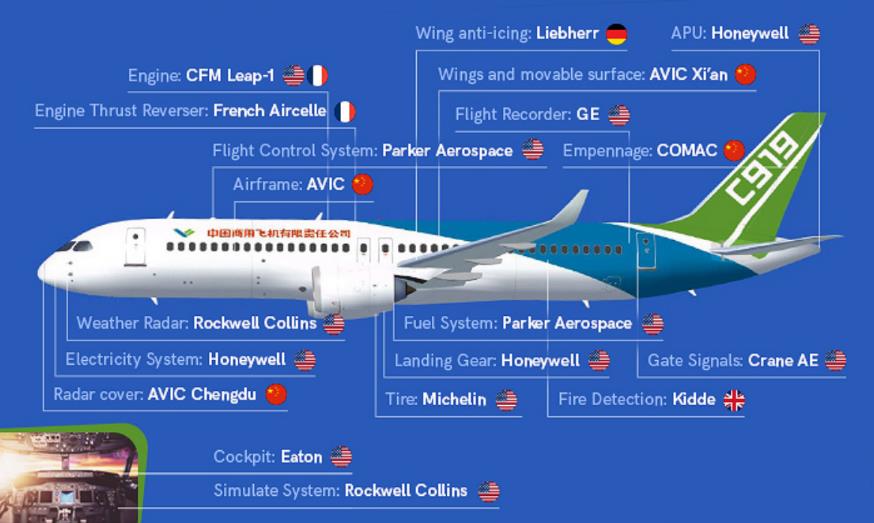
According to the company, Chinese hackers, employees of the country’s Ministry of State Security, information security researchers and many others joined forces to create this airliner.The purpose of this large-scale operation was to obtain intellectual property and development that would help China narrow the technological gap in the aviation industry so that Chinese state-owned aerospace manufacturer Comac could build its own airliner that could compete with industry giants such as Airbus and Boeing.
So, according to researchers, the resulting intellectual property was necessary for the production of all C919 components within China.
“The Ministry of State Security (MSS) assigned this task to the Jiangsu Bureau (MSS JSSD). There, in turn, the attacks were delegated to two leading employees who were supposed to coordinate the common efforts. One of them was directly responsible for the work of the hacker team, while the second found insiders working in aviation and aerospace companies”, – reported in the Crowdstrike report.
In the period from 2010 to 2015, this hacking team successfully attacked companies such as Ametek, Honeywell, Safran, Capstone Turbine, GE and so on.
Interestingly, according to Crowdstrike and the US Department of Justice, MSS used a different approach to this operation. Therefore, the hack group, which the researchers called Turbine Panda, did not consist of proven cyber operatives from among the military: instead, local hackers and information security researchers, including well-known in the underground circles, were recruited for work.
Then they were instructed to find an entry point to the target networks, where they usually used such malware as Sakula, PlugX and Winnti, using malware to search for confidential information and its theft.
“In the vast majority of cases, hackers used malware specifically designed for these attacks. This malware is named Sakula, and information security specialist Yu Pingan developed it as a legitimate tool”, – reported in the Crowdstrike report.
In rare cases where Turbine Panda members could not find a loophole for entering the network, the second coordinator from JSSD MSS entered into the matter.
He found and hired a Chinese citizen working for the target company and used his services to host Sakula on the victim’s network (usually via a USB stick).
Read also: Spamhaus released botnet statistics for Q3 2019
Crowdstrike analysts write that Turbine Panda can be called extremely effective. So, in 2016, after almost six years of constant attacks on foreign aviation companies, Aero Engine Corporation of China (AECC) introduced the CJ-1000AX engine, which will be used in the C919 liner under development, and will replace the engine created by a foreign contractor.
Experts have already noted that the CJ-1000AX shows many similarities (1, 2) with the LEAP-1C and LEAP-X engines produced by CFM International, a joint venture of the American company GE Aviation and the French aerospace firm Safran, the latter is a foreign contractor who worked on engines for the C919.
The attention of US authorities was drawn to Turbine Panda after attacks on such large targets as the healthcare provider Anthem and the U.S. Office of Personnel Management, OPM. Although these hacks brought many useful data to hackers, including for the recruitment of future insiders, they also provoked a large-scale investigation.
Law enforcement officers were the first to figure out and arrest insiders in 2017, as they were easier to detect, and they did not have the protection of the Chinese government, since they acted on foreign territory.
Then, in the same year, while participating in a security conference in Los Angeles, the creator of the Malvari Sakula was arrested, who was later accused of involvement in hacker attacks on Anthem and OPM.
In response to Yu Pingan’s arrest, the Chinese government banned its specialists from participating in foreign security conferences, fearing that US authorities might take other “assets” into their hands.
And if at first these arrests looked rather strange, the Record future report shed light on the fact that the Chinese Ministry of State Security has extensive connections on the Chinese cybersecurity scene, accumulating and hiding information about vulnerabilities discovered by Chinese information security experts. Next, these problems, before they are publicly disclosed, are used in practice by MSS hackers.
Apparently, the last nail in the lid of the Turbine Panda coffin in 2018 was the arrest of Xu Yanjun, JSSD MSS officer in charge of recruiting employees from foreign companies. The US authorities hope that he will cooperate with the investigation to commute the sentence.
“Currently, the remaining members of Turbine Panda have moved to other Chinese hack groups, including Emissary Panda, Nightshade Panda, Sneaky Panda, Gothic Panda, Anchor Panda and so on“, – note in Crowdstrike.
However, analysts believe that attacks on foreign aviation companies will continue in the future, as the Comac C919 is not at all as good and successful as the Chinese government expected. Efforts are already underway to create the next version of the airliner, the C929.






One Comment