Emotet Botnet Returns After Law Enforcement Operation and Teams With TrickBot
The Emotet botnet is back after Europol, the FBI and law enforcement agencies around the world, including Canada, the Netherlands, France, Germany, Lithuania, the United Kingdom and Ukraine, carried out a large-scale coordinated operation to eliminate it in January this year.
Then law enforcement officers managed to seize control over the Emotet infrastructure, disrupting its work. As a result, the criminals were no longer able to use the hacked machines, and the malware stopped spreading to new targets.Moreover, law enforcement officers used their access to the Emotet control servers, which came under the control of the German Federal Criminal Police Office (Bundeskriminalamt), to deploy a special update to all infected hosts. A special module for Emotet, created by Bundeskriminalamt specialists, was distributed to all infected systems in the form of a 32-bit file EmotetLoader.dll. This spring, the update contained a “ticking time bomb” that is a the mechanism that led to the removal of Emotet from all infected machines. In fact, the botnet was destroyed.
Now, ten months after the operation to eliminate the botnet, researchers have re-discovered malware activity. Last weekend, cybersecurity researcher Luca Ebach reported that another botnet, TrickBot, is helping Emotet operators get back on their feet by installing Emotet malware on systems already infected by TrickBot itself.
One of the enthusiasts from the Cryptolaemus group, which includes more than 20 information security specialists from all over the world, united back in 2018 for a common goal – to fight the Emotet malware, told The Record that in the past, when Emotet was distributing Trickbot, and not on the contrary, this activity was called ReachAround. This essentially means that Emotet is being rebuilt using the existing TrickBot infrastructure.
Let me remind you that Cryptolaemus researchers played a decisive role in tracking the botnet and actively assisted law enforcement agencies in destroying Emotet. In this regard, it is interesting that new versions of Emotet appeared almost simultaneously with the three-year anniversary of Cryptolaemus on Twitter, although it is unclear whether this was an accident, or the operators of Emotet really conveyed a kind of “greeting” to the researchers.
The screenshot below, provided to the media by Cryptolaemus member Abuse.ch, shows Emotet’s period of inactivity (January to November 2021), as well as when the hackers deployed new control servers.
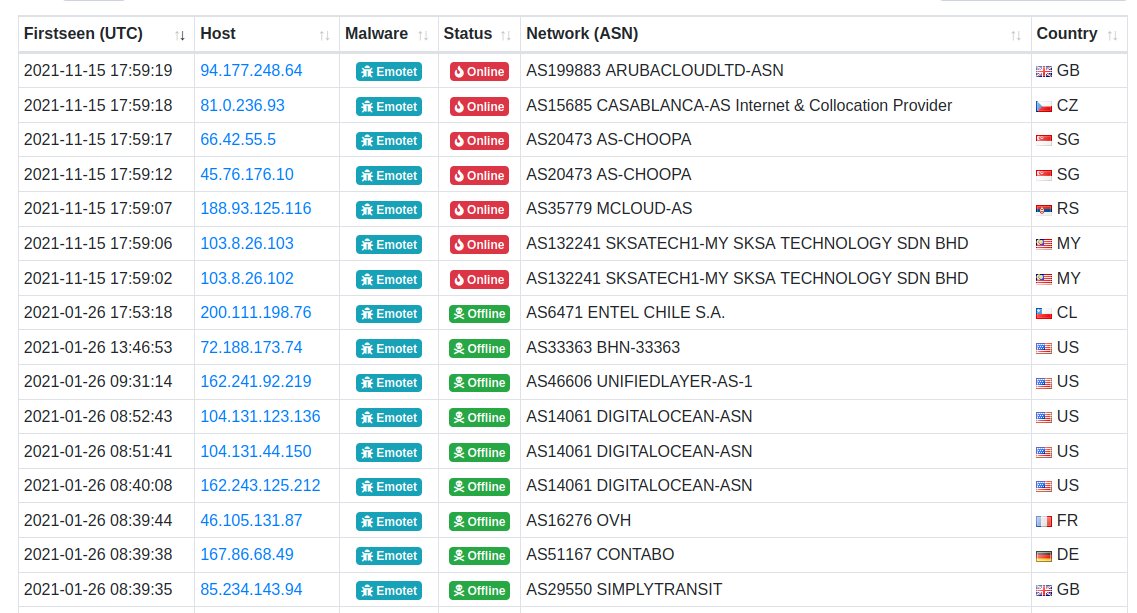
According to Cryptolaemus, Emotet’s operators are still not acting as usual, that is, they are not sending spam by e-mail. Instead, they rely on the help of the TrickBot group to help them rebuild the botnet before it goes back to spam.
The researchers note that it will be difficult for Emotet to reach its previous size in the coming months, but the malware remains a very complex and effective threat that cannot be ignored. Emotet’s new infrastructure is growing fast enough: more than 246 infected devices are already acting as C&C servers.





