Chinese hackers use a new backdoor to spy on the country’s government from Southeast Asia
Check Point specialists discovered a spy operation carried out by Chinese hackers, during which they used a new backdoor of their own design. The operation was aimed at the government of one of the countries of Southeast Asia.
Researchers say an unnamed Chinese hack group has been developing a new backdoor for Windows for three years. With its help, hackers could monitor victims in real time: take screenshots, edit files, and execute other commands.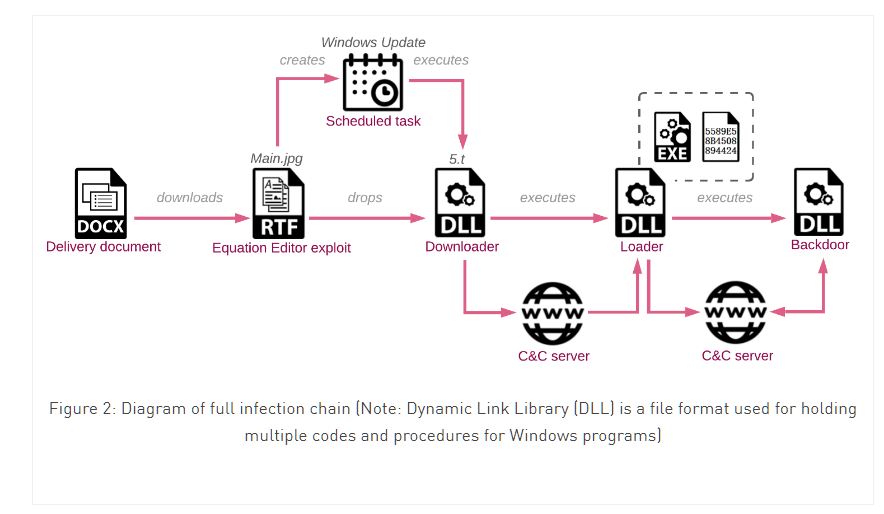
The company’s report states that the criminals sent malicious documents to the Foreign Ministry, posing as employees of the government of the same country. By opening the document, the victim launched a chain of actions that eventually led to the deployment of the backdoor. This malware, in turn, collected any information about the infected system (for example, a list of files and active programs), and also provided attackers with remote access to the infected device.

The backdoor, which the group has been developing for about three years, overrides the usual authentication procedures for accessing the system. The backdoor module with the internal name VictoryDll_x86.dll contains custom malware with many hacking tools.
Experts associate this spy campaign with China, basing on the following artifacts and signs:
- control servers were only online from 01:00 to 08:00 UTC. According to the researchers, this indicates working hours in a particular country/region; attackers – therefore, the territorial range of possible sources of this attack is limited;
- C&C servers did not return any payload (even during business hours) between May 1 and May 5, during which Labor Day is celebrated in China.
- Some test versions of the backdoor had records of checking network connectivity from www.baidu.com;
- The RoyalRoad RTF exploit kit used in malicious documents for the attack is mainly associated with Chinese APT groups.
- some test versions of the backdoor dated 2018 were uploaded to VirusTotal from China.
Let me remind you that we talked about the fact that the Chinese authorities use Tianfu Cup as a source of exploits, as well as that the Chinese authorities use AI to analyze emotions of Uyghur prisoners.





