Transport company CMA CGM attacked by Ragnar Locker
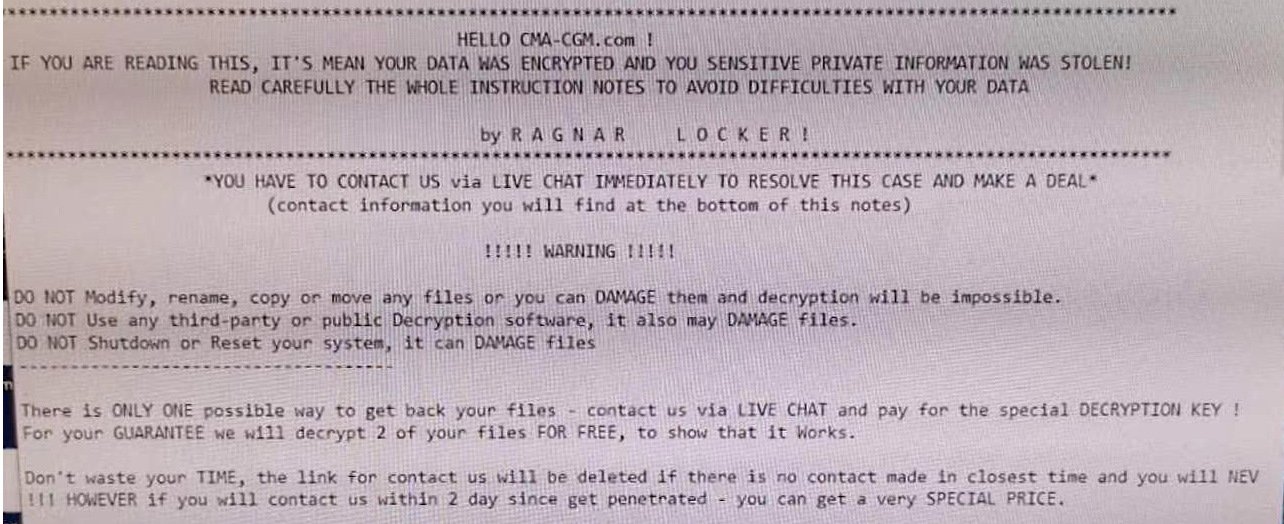
The French transport company CMA CGM, mainly engaged in container shipping, was attacked by the Ragnar Locker ransomware.
CMA CGM is one of the largest logistics companies in the world with 755 offices, 750 warehouses and more than 110,000 employees in 160 countries.
The official announcement states that the attack affected a number of the company’s peripheral servers, forcing IT staff to disable external access to applications to prevent further spread of the threat.
Currently, restoration work and investigation of the incident are underway. Currently, customers are advised to contact their local CMA CGM offices directly as IT systems may not work.
“External access to CMA CGM IT applications are currently unavailable. IT teams are working on resolving the incident to ensure business continuity. For all bookings, please contact your local agency. We will keep you posted regularly on the current situation”, — reported on Twitter CMA CGM Group.
ZDNet and other media outlets report that the attack targeted the Chinese offices of CMA CGM in Shanghai, Shenzhen and Guangzhou. Journalists also write that the company has become a victim of the Ragnar Locker ransomware, although there is no official confirmation of this yet.
Let me remind you that recently RagnarLocker ransomware operators attacked Energias de Portugal energy holding and demanded a ransom of 10 million euros.
However, it is noted that this attack on CMA CGM is already the fourth attack on a large transport company in the last couple of years.
For example, all the most serious players in the industry have already suffered from such incidents: in 2017, NotPetya ransomware invaded the network of the sea logistic company Maersk; in 2018, ransomware paralyzed the work of COSCO for several weeks; In April 2020, the Mediterranean Shipping Company data center went out of order for several days due to an attack by an unnamed encryptor.
“After Maersk was hit by the NotPetya crytper, I believe criminals realized the opportunity to bring a critical industry down, so payment of a ransom was perhaps more likely than other industries,” — said Ken Munro, a security researcher at Pen Test Partners, a UK cyber-security company that conducts penetration testing for the maritime sector.
Maritime industry groups have responded to these increasing risks of malware by publishing two sets of IT security guidelines to address maritime security aboard ocean-bound vessels.
But the incidents where malware gangs have done the most damage were the attacks that targeted shore-based systems that sit in offices, business offices, and data centers.
Therefore, the shipping industry needs to stop prioritizing less likely hacking scenarios and focus on its onshore systems, at least for now.
I think that in the context of this post, you will also be interested to know that Ragnar Locker ransomware uses virtual machines to hide their actions.