Chinese Hacker Group Volt Typhoon Attacks Critical US and Guam Infrastructure
Microsoft has reported on the Chinese hacker group Volt Typhoon, which has been active for at least two years and specializes in cyber espionage.
During this time, the group has established itself in critical infrastructure environments throughout the United States and Guam (an island that has the status of an unincorporated organized territory of the United States, which hosts several military bases), stealing credentials, confidential information and remaining virtually unnoticed.Let me remind you that we also wrote that Chinese hackers use a new backdoor to spy on the country’s government from Southeast Asia, and also that Chinese hackers attacked the largest industrial companies in Germany.
The media also wrote that US Authorities List Vulnerabilities That Chinese Hackers Attack.
The Volt Typhoon group was originally discovered when Microsoft was investigating an attack on a port in the US, and later it turned out that the hackers were also targeting the telecommunications sector in Guam. Further investigation revealed multiple breaches in several critical sectors of the US infrastructure. The hackers’ targets are now reported to span a wide range of critical sectors, including government, shipping, communications, manufacturing, IT, utilities, transportation, construction, and education.
In addition to Microsoft’s report, this malicious campaign is now documented in a bulletin jointly published by member countries of the Five Eyes alliance (which brings together the intelligence agencies of Australia, Canada, New Zealand, the US and the UK).
Experts say that for greater stealth, hackers use tools that are already installed or built into infected devices, which attackers control manually, rather than automatically. This tactic is commonly referred to as “living off the land“.
In addition, hackers mask their activity using compromised SOHO routers and other network devices (from Asus, Cisco, D-Link, Netgear, FatPipe and Zyxel) as an intermediate infrastructure that allows them to communicate with infected computers under the guise of local Internet -providers.
According to the researchers, this malicious campaign is forward-looking and develops the ability to “disrupt critical infrastructure between the US and the Asian region during future crises.” The fact is that Guam is important to the US military because of its Pacific ports and airbase. And the strategic importance of Guam seems to be of interest to hackers in connection with the growing tensions around Taiwan.
Typically, Volt Typhoon attacks begin by compromising Internet-accessible Fortinet FortiGuard devices and by exploiting an unknown 0-day vulnerability. Volt Typhoon has also been seen exploiting vulnerabilities in Zoho ManageEngine.
Ultimately, the privileged access gained from compromised Fortinet devices allows hackers to steal credentials using the Local Security Authority Subsystem Service (LSASS).
After infiltrating target networks, attackers proceed with “living off the land” attacks, manually using LOLBins, including PowerShell, Certutil, Netsh, as well as Windows Management Instrumentation Command-line (WMIC). The group also uses open source tools, including Fast Reverse Proxy (frp), Mimikatz and Impacket.
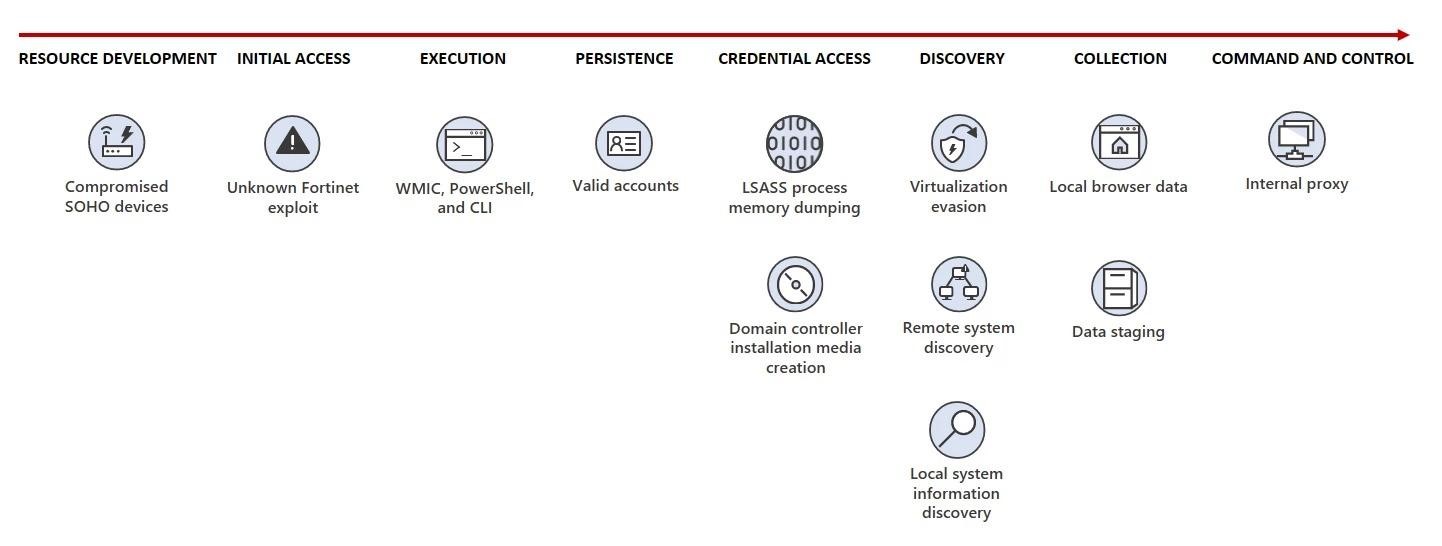
Scheme of attacks





