Encrypted ZIP Archives Have Two Different Passwords
Recently, information security specialist Arseniy Sharoglazov demonstrated on his Twitter that two passwords can be used for password-protected ZIP archives at once.
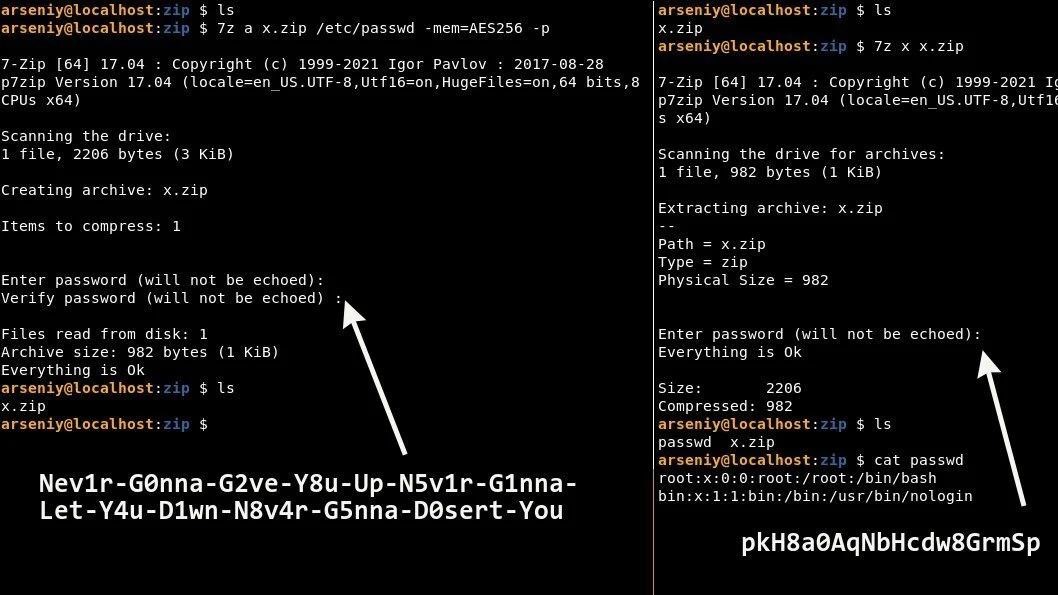
During the experiment, he created an archive called x.zip, the password for which was a line from Rick Astley’s unforgettable meme song “Never Gonna Give You Up”: “Nev1r-G0nna-G2ve-Y8u-Up-N5v1r-G1nna-Let-Y4u -D1wn-N8v4r-G5nna-D0sert-You”.The researcher demonstrated that it is possible to successfully unpack the archive both with this password and with the password “pkH8a0AqNbHcdw8GrmSp”.
Let me remind you that we reported that Hunter Biden’s top-secret laptop was protected with a simple password.
Commentators began to ask Sharoglazov how he did it, but the essence of this “trick” was explained by another Twitter user under the nickname Unblvr. The fact is that when creating password-protected archives with AES-256 mode enabled, ZIP uses the PBKDF2 standard and hashes the password created by the user if it is too long. Any passwords over 64 bytes (characters) are considered too long in this case.
As a result, the hash obtained in this way actually becomes the second password suitable for the archive: in this case, “pkH8a0AqNbHcdw8GrmSp” instead of the overly long “Nev1r-G0nna-G2ve-Y8u …”.
When the user tries to decompress the file and enters a password longer than 64 bytes, the input is again hashed by the ZIP application and compared to the correct password (which is itself a hash). A match leads to successful unpacking of the archive.
Thus, the second “correct password” shown by Sharoglazov is actually an ASCII version of the SHA-1 hash for an overly long password. For example, the SHA-1 checksum for the password “Nev1r-G0nna-G2ve-Y8u…” is 706b4838613041714e62486364773847726d5370. When converted to ASCII, the output is: pkH8a0AqNbHcdw8GrmSp.
Bleeping Computer journalists drew attention to another interesting aspect of this “trick”: the ASCII representation for the SHA-1 hash does not have to be an alphanumeric string at all, as happened with the “pkH8a0AqNbHcdw8GrmSp” password.
For clarity, the publication gives the following example: if you use the password “Bl33pingC0mputer-Sh0w-M3-H0W-t0-pR0Duc3-an-eNcRyPT3D-ZIP-File-in-the-simplest-way” for a ZIP archive, its checksum is SHA-1 will look like this: bd0b8c7ab2bf5934574474fb403e3c0a7e789b61.
However, the ASCII representation for this checksum is a jumble of bytes, and it’s not at all the elegant “alternative password” shown in Sharoglazov’s example.

Then the journalists asked the researcher how he managed to guess the password, the SHA-1 checksum for which is a pure alphanumeric string in ASCII. Sharoglazov said that he used a slightly modified version of the hashcat open source password recovery tool. He generated various variations of the string “Never Gonna Give You Up…” using different alphanumeric combinations until he came up with the perfect password for his experiment, “pkH8a0AqNbHcdw8GrmSp”.





