Nearly 300 Restaurant Customers Hit by MageCart Attacks
Three restaurant ordering platforms (MenuDrive, Harbortouch and InTouchPOS) were hit by two MageCart skimming campaigns. As a result, at least 311 restaurants and their customers were compromised.
Let me remind you that initially the name MageCart was assigned to one hack group, which was the first to introduce web skimmers (malicious JavaScript) on the pages of online stores to steal bank card data. But this approach was so successful that the group soon had numerous imitators, and the name MageCart became a common name, and now they designate a whole class of such attacks.We wrote that Sites on the Magento 1 platform were overwhelmed by a wave of MageCart attacks, and that Attackers hide MageCart scripts even in CSS files.
Analysts at Recorded Future report that in total, this hack led to the compromise of more than 50,000 payment cards that were stolen from customers of the affected restaurants and put up for sale on the dark web.
The first attack is believed to have started around January 18, 2022 and continued until the malicious domain used in the campaign was blocked on May 26. The campaign against InTouchPOS, in turn, has been active since November 12, 2021.
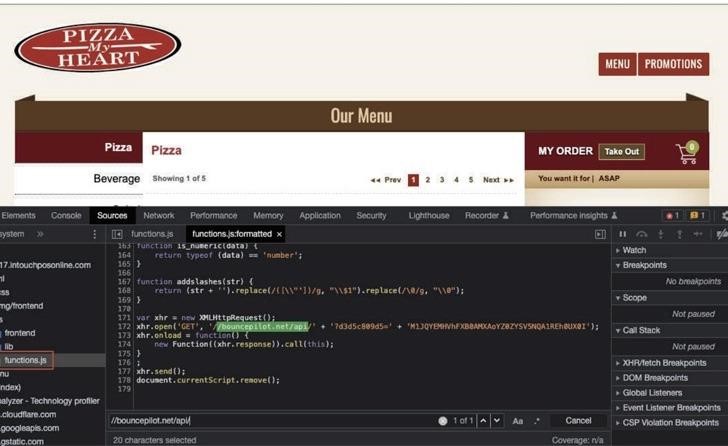
The ultimate goal of these attacks was to inject malicious PHP code into payment pages (for which known vulnerabilities are usually used) and then transfer customer data to the attackers’ server.
The researchers say the attackers definitely knew what they were doing when they targeted online ordering platforms. After all, even when attacking one such platform, the transactions of dozens or even hundreds of restaurants are compromised, which allows hackers “to steal huge amounts of data, disproportionate to the number of systems they actually hack.”





