Check Point specialists spoke about the Rampant Kitten hacker group, which steals 2FA codes from SMS, as well as data from Telegram and KeePass, and which has been tracking Iranian opposition organizations, dissidents and expats for at least six years.
The researchers emphasize that other companies and journalists have previously reported about separate attacks from this group, but the Check Point investigation has allowed several to link together several campaigns and correlate them with Rampant Kitten.We also wrote that the Iranian hacker group Cobalt Dickens attacked over 60 universities around the world.
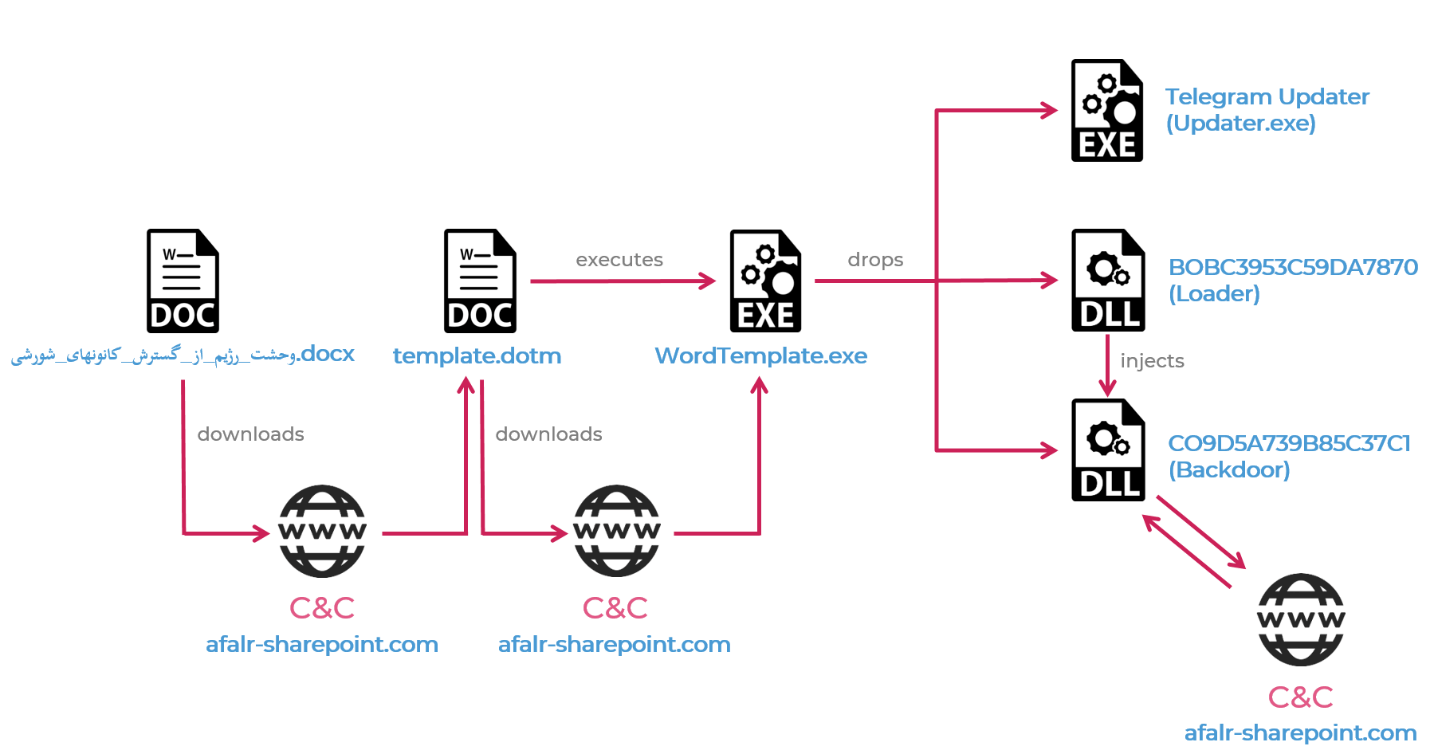
“The hackers used a variety of malware for their operations, including four info-stealers for Windows that spread via malicious Microsoft Office documents, and an Android backdoor that usually hid inside malicious applications”, — write the researchers.
In particular, the malware was found in an application that helped Persian speakers to obtain a driver’s license in Sweden.
Malware for Windows was mainly used for stealing personal documents of victims, as well as files from the Telegram desktop client, which ultimately allowed hackers to gain access to a user’s account. In addition, the malware stole files from the KeePass password manager, intercepted data in the clipboard, and took screenshots.
Although the main Rampant Kitten malware targeted Windows, researchers also found a powerful backdoor for Android. This malware can steal a victim’s contact list and SMS messages, as well as discreetly spy on the user through the device’s microphone, take screenshots and lure them to phishing pages.
At the same time, the hackers clearly paid special attention to the interception of SMS messages, namely two-factor authentication codes. For example, malware intercepted and forwarded to attackers any messages containing the string “G-“, which is usually used as a prefix in 2FA codes for Google accounts. Apparently, at the same time, the hackers used Android malware to show the victim a Google phishing page in order to find out the user’s credentials and then gain access to his account (after all, the two-factor authentication code was not a problem).
It was also noticed that the malware automatically forwards any incoming SMS messages from Telegram and other social networking applications to attackers. Such messages also contain 2FA codes, that is, the group was definitely interested not only in other people’s Google accounts.
“After doing our research, we noticed a few things. First, special attention was paid to surveillance of instant messaging. Although Telegram cannot be decrypted, it can be compromised. Second, mobile, PC, and phishing attacks were all part of the same operation”, — comments Check Point specialist Lotem Finkelsteen.
We remind you that just recently the US Department of Justice accused three Iranian hackers of hacking aerospace companies.





