Iranian hacker group Cobalt Dickens attacked over 60 universities around the world
The Iranian group, which IS experts call Cobalt Dickens, is still active and attacks universities and other educational institutions around the world.
In the spring of 2018, U.S. authorities indicted in absentia nine Iranian citizens who were members of the “government” hack group affiliated with the Mabna Institute, a company created in 2013 specifically for attacks on universities, editorial boards of scientific journals, technology companies and government organizations.It was reported that over the years of its existence, the group stole more than 32 terabytes of academic and research data. According to investigators, hackers targeted 100,000 accounts of professors and employees of educational institutions around the world and successfully cracked about 8,000 of them.
Attackers sold the stolen information on the darknet later.
Now, 18 months after this, Secureworks researchers have reported that this group, which experts call Cobalt Dickens, is still active and attacks schools around the world, including the United States, Canada, Britain, Switzerland and Australia.
Read also: Over 600,000 GPS trackers use default passwords and are available to everyone
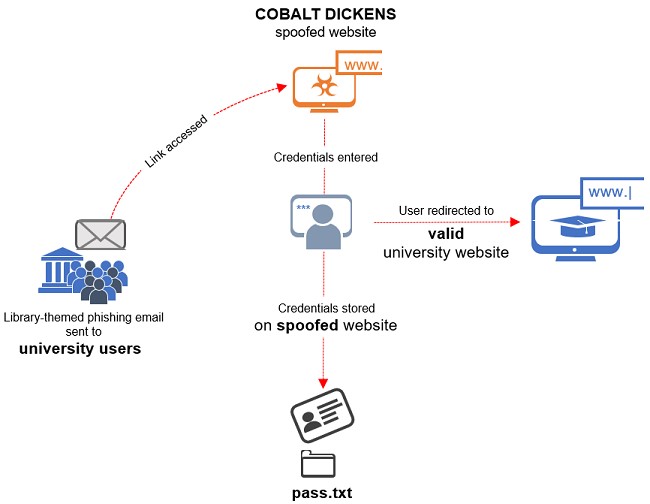
According to researchers, a recent Cobalt Dickens phishing campaign has targeted 60 different schools. Since July of this year, hackers have used malicious web pages that disguised themselves as real university resources to steal the credentials of their goals.
People were forwarded on such sites using phishing emails containing relevant links.
“As a rule, phishing emails informed victims that their online library account will expire unless they immediately re-activate it by logging in. By clicking on the link from such a message, users were taken to pages that looked like real library resources that are widely used in educational institutions. Of course, all the credentials entered on such pages were handed over to the attackers”, – Secureworks experts report.
To make it harder to detect malicious resources, Cobalt Dickens members protected many of them with HTTPS certificates and also filled fake resources with content extracted from real sites.
So, Cobalt Dickens has registered at least 20 new domains with valid SSL certificates in the .ml, .ga, .cf, .gq and .tk zones. To do this, members of the group used free services and solutions: they used the services of the Freenom hoster, Let’s Encrypt certificates, and found some tools on GitHub.





