Google Threat Analysis Group (TAG) analysts warn that North Korean hackers attack cybersecurity experts involved in vulnerability research.
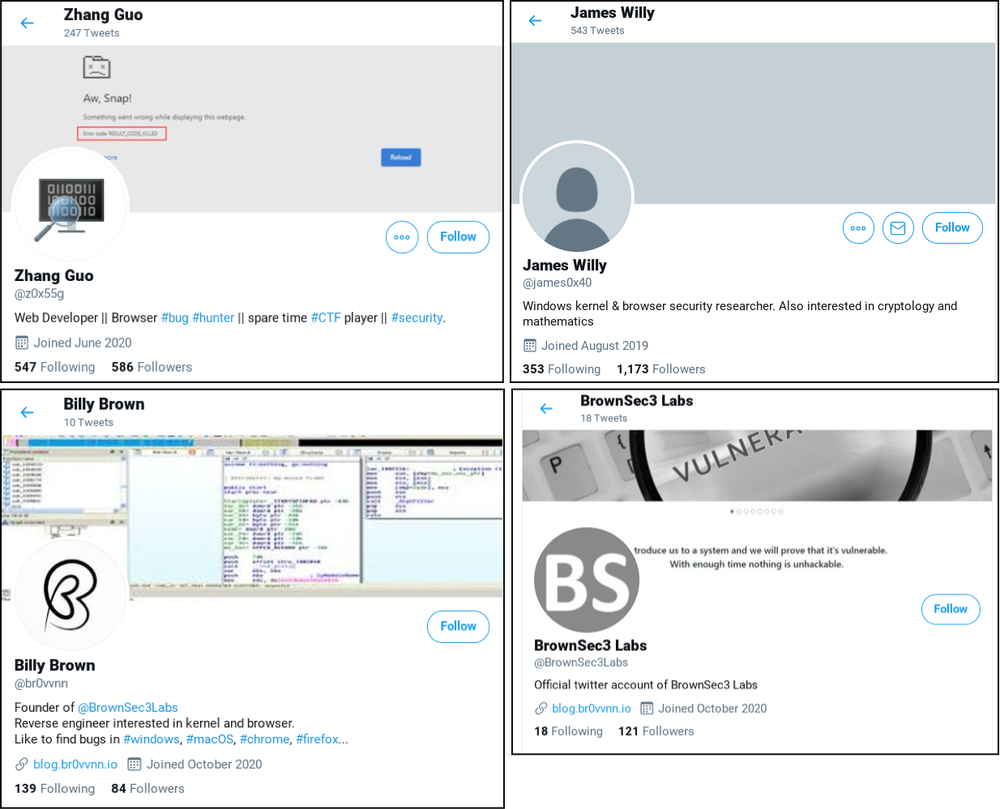
An expert report said North Korean “government” hackers used a number of social media profiles, including Twitter, LinkedIn, Telegram, Discord and Keybase, to contact researchers using fictitious identities.“In order to build credibility and connect with security researchers, the actors established a research blog and multiple Twitter profiles to interact with potential targets. They’ve used these Twitter profiles for posting links to their blog, posting videos of their claimed exploits and for amplifying and retweeting posts from other accounts that they control”, — write TAG researchers.
Occasionally they also used e-mains for this purpose.
Let me remind you that we wrote that IS experts discovered connection between North Korean hackers and MageCart attacks.
Having established contact with a specialist, the hackers invited him to work together on some research and provided access to the Visual Studio project.
Of course, this project contained malicious code that infected the specialist’s system with malware. The malware, which later was associated with the well-known hack group Lazarus, worked like a regular backdoor, communicating with a remote server while waiting for commands.
“KTAE code similarity analysis for the malware used to target security researchers involved in 0day analysis and development. “Manuscrypt” (also known as FALLCHILL) is typically used by the Lazarus APT”, — told Romanian anti-hacker Costin Raiu in his Twitter account.
However, cybercriminals did not always directly infect the systems of their targets with malware. In some other cases, they asked researchers to visit the blog at blog[.]Br0vvnn[.]io, which also hosted the malicious code. Google TAG points out that many of the victims who visited the site were using “completely safe and updated versions of Windows 10 and Chrome”, but were still compromised.
While there is no detailed information about browser attacks yet, researchers believe the North Korean group may have used a combination of zero-day vulnerabilities in Chrome and Windows 10 to do so.
Now Google TAG experts are asking members of the information security community to share more detailed information about attacks, especially if some of the researchers believe that they have become victims of such a compromise.
Let me remind you that US authorities reveal new North Korean malware to mark WannaCry attack anniversary.





