Kaspersky Lab discovered a set of malicious modules MontysThree, which is written in C++ and has existed since at least 2018. The MontysThree malware is targeting industrial enterprises.
The malware authors themselves called this set MT3, and following this abbreviation, the experts gave it the name MontysThree.“MontysThree uses techniques to help avoid detection, including communicating with the C&C server via public clouds and steganography”, – say Kaspersky Lab experts.
In fact, malware consists of four modules. Thus, the MontysThree attack begins with the classic phishing.
By the way, read our article on how to avoid spam and phishing scams in email.
Using phishing, a bootloader is distributed via self-extracting archives (SFX, RAR).
The file names of these archives can be associated with employee contact lists, technical documents, or medical test results. The archives contain malicious PE files disguised as .pdf or .doc. If the user opens such a file, the loader will decrypt the main malicious module from the steganographic bitmap. For this purpose hackers specifically developed an algorithm.
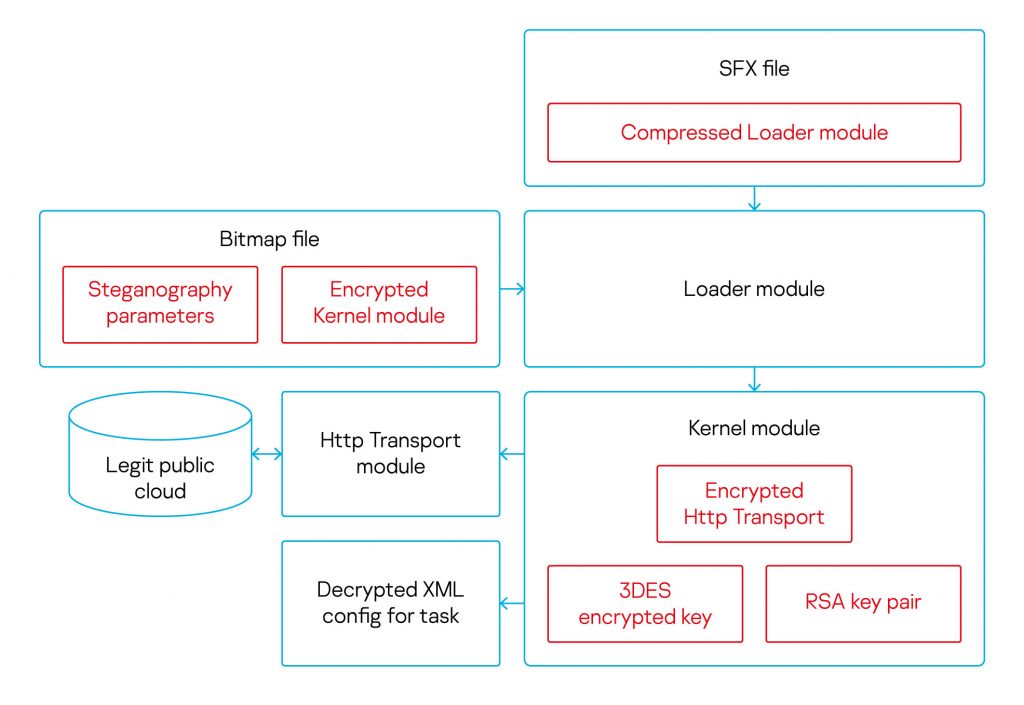
The main malicious module uses several encryption algorithms to avoid detection, mainly RSA for communicating with the command and control server and decrypting configuration data. This XML-based data describes the tasks of malware: finding documents with specified extensions, in specified directories, and on removable media. MontysThree operators are primarily interested in Microsoft Office and Adobe Acrobat documents.
Also, MontysThree modules are able to take screenshots of the desktop, determine if a victim is interesting to operators by analysing its network and local settings, and so on. The collected information is encrypted and transferred to public cloud services (Google Drive, Microsoft One Drive, Dropbox), through are received new files.
MontysThree uses a very simple method for pinning to an infected system – the Windows Quick Launch. Users, without knowing it, launch the primary malware module every time they open legitimate applications, such as browsers, using this panel.
The experts write that they have not found any similarities between this malicious code and the code of other targeted campaigns.
“Attacks using MontysThree tools stand out not only for targeting industrial enterprises (although not unique, they are not the most popular targets for targeted attacks), but also for their combination of advanced and amateur tactics and methods. MontysThree developers use modern secure cryptographic standards and customized steganography. The level of development is not as high as that of large APT players, but the authors have invested a lot of effort into creating this set of tools and continue to develop it.”, — comments Denis Legezo, Senior Cybersecurity Expert at Kaspersky Lab.
Let me remind you that more than half of industrial enterprises still use outdated OS, and therefore are vulnerable to many other viruses.




