Bug in HiSilicon and Qualcomm chips turns hotspots into surveillance devices
At least 55 models of Wi-Fi routers with Qualcomm and HiSilicon Network Processing Units (NPUs) have a bug that can be used to “listen” to data transmitted over a wireless network.
Let me remind you that we also wrote that Experts found vulnerability in Qualcomm processors that endangers all Android-devices owners, and also that Huawei success in 5G may be due to cyber espionage.And also the media wrote about the fact that Qualcomm Snapdragon vulnerabilities endanger nearly half of smartphones in the world.
The vulnerability report was submitted by a joint group of experts from China and the United States. The bug received the identifier CVE-2022-25667 and is due to the fact that devices cannot block malicious ICMP (Internet Control Message Protocol) messages, which are eventually used to intercept the victim’s wireless connection and spy.
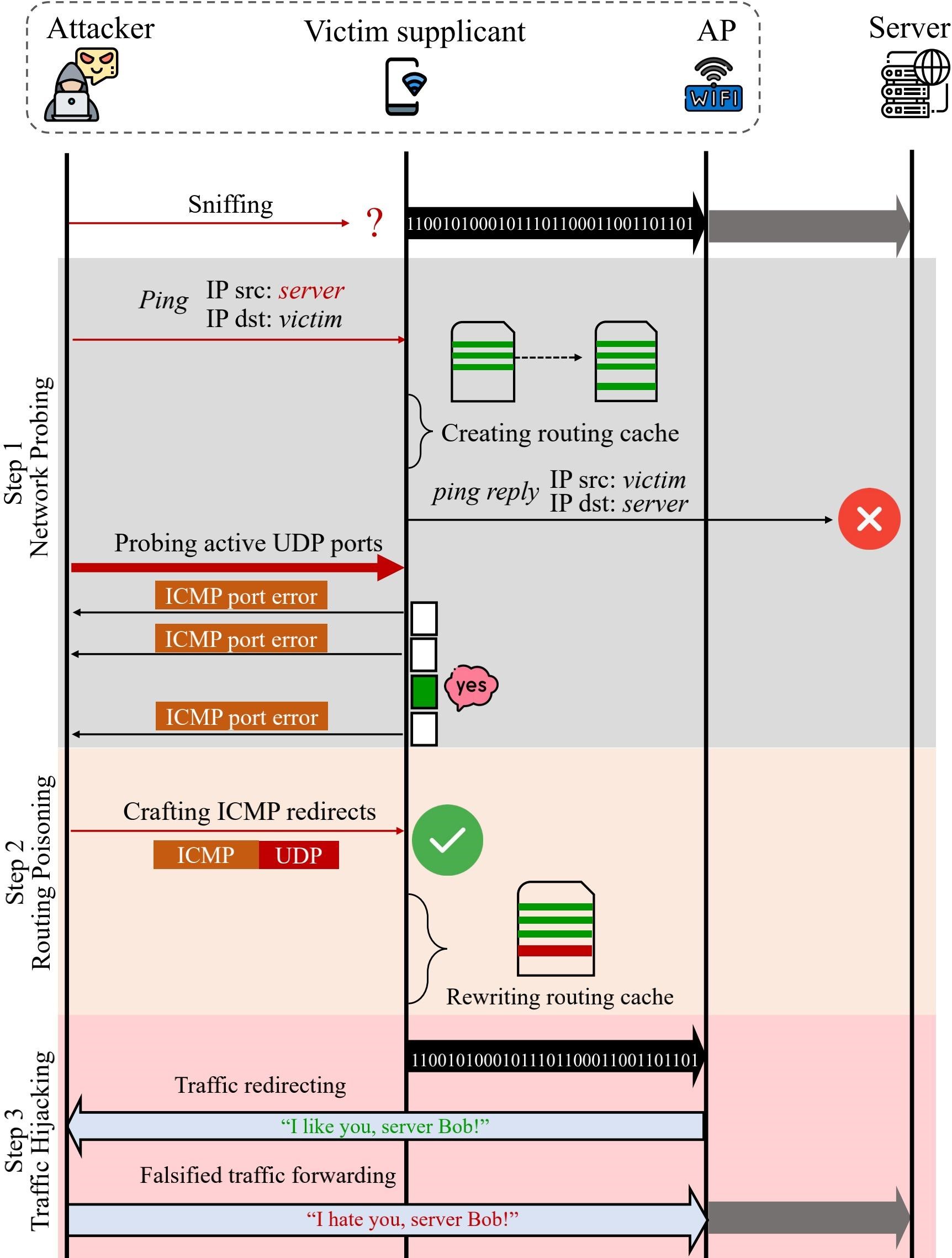
Attack scheme
The researchers remind that the ICMP protocol is mainly used to diagnose problems with network traffic and report errors (for example, its requested service is not available or the host or router is not responding), although cybercriminals often use it for DDoS attacks, arranging an ICMP flood .
Experts write that ICMP can also be used to bypass Wi-Fi Protected Access (WPA) protection in order to intercept and “listen” to traffic on a foreign wireless network. WPA (including WPA2 and WPA3) is supposed to protect devices on a wireless network from spying: traffic between each client-router pair is encrypted individually so that other clients, even those on the same network, cannot intercept it.
For the attack proposed by the researchers to work, the attacker and his victim must be on the same network (for example, on a public Wi-Fi network). The attacker will also need to: be able to communicate directly with the victim’s device via Wi-Fi; find out its IP address; find an open UDP port on the victim’s device.
In addition, if the victim does not just rely on WPA, but protects his network traffic from interception using HTTPS, SSH, TLS, or other encryption protocols, the attacker will also have to deal with this somehow on his own.
The attack consists of several steps, including sending an ICMP redirect message to the victim’s device that looks like it came from an access point.
In theory, the router should reject such spoofed messages if it is asked to relay them to a device on the network, since the router did not actually generate these messages. But the researchers found that fake messages can still be sent to other devices through the vulnerable access point. As a result, the receiving device believes that everything is in order with the redirect, and it came from the access point.
Such messages force the victim’s devices to redirect their traffic to another destination. That is, the ICMP redirect is formatted as if it is real and comes from the Wi-Fi router. The victim’s access point receives this message and redirects the network traffic to a system under the control of the attacker, allowing the attacker to intercept and examine other people’s traffic.
According to the researchers, they tested 55 access points from ten manufacturers, and not a single device was able to block fake ICMP messages. They also claim that 109 out of 122 (89%) Wi-Fi networks they tested were vulnerable to this attack.
Since the problem is related to the NPU, Qualcomm was notified of the vulnerability at the end of 2021, and in November 2022 the company issued a security bulletin addressing this issue. However, the company does not provide additional information about the status of the patch deployment.
Chinese company HiSilicon, owned by Huawei, has also been made aware of the issue.
And while 6 out of 10 access point manufacturers mentioned in the study confirmed the problem in their products, many devices may still not receive fixes.
In the paper, the researchers propose a number of possible options to mitigate the problem in the NPU, and also propose adding additional security checks for cross-layer network interactions. They say they have already developed a prototype of such a mechanism for Linux 4.18 and have been able to confirm its effectiveness.
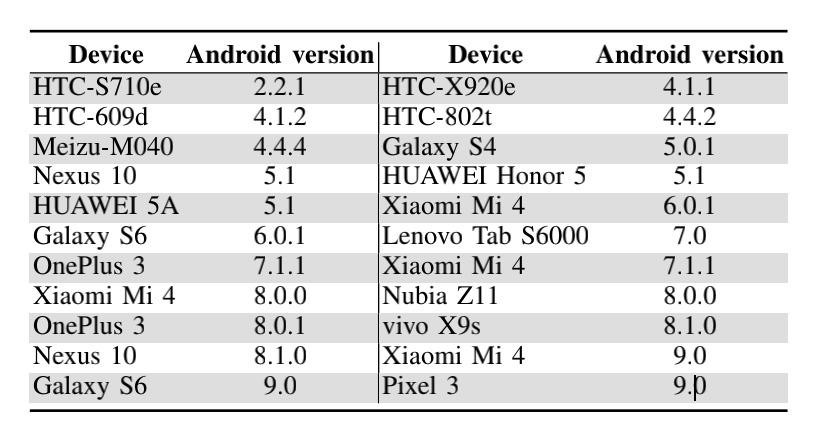
Android-devices that are susceptible to the issue
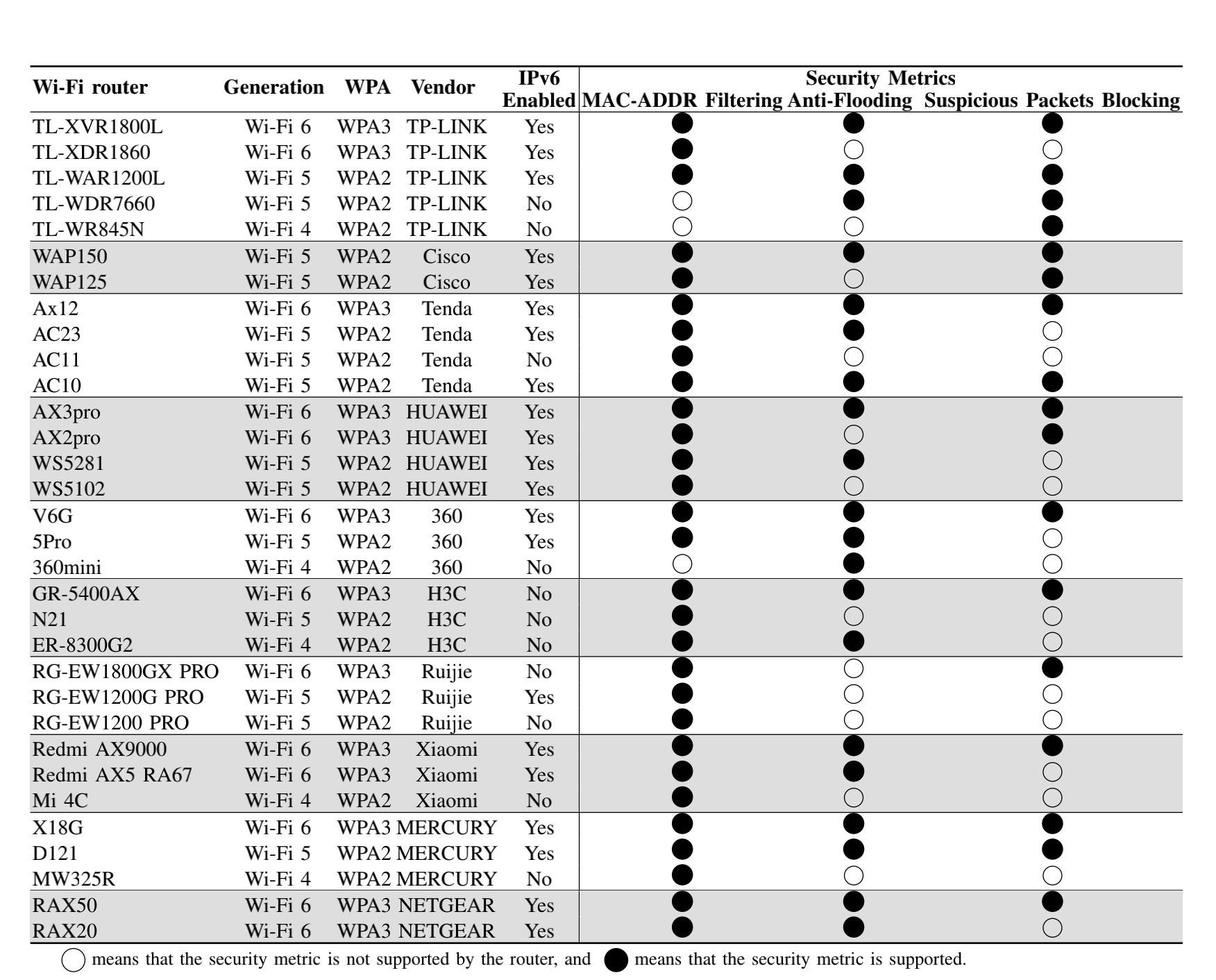
Vulnerable devices according to test results





