Mining malware Pro-Ocean attacks Apache and Oracle servers
Palo Alto Networks reports that the Rocke hacker group is using the new Pro-Ocean mining malware to attack vulnerable installations of Apache ActiveMQ, Oracle WebLogic and Redis.
Let me remind you that Rocke was discovered by Cisco Talos experts back in the distant summer of 2018. The main focus of the group has always been mining the Monero cryptocurrency, and hackers even competed with other attackers for control of vulnerable servers.Experts now write that Rocke still does not change its habit of attacking cloud applications and exploiting various known vulnerabilities to take control of unpatched Oracle WebLogic servers (CVE-2017-10271), Apache ActiveMQ (CVE-2016-3088) and insecure Redis installations.
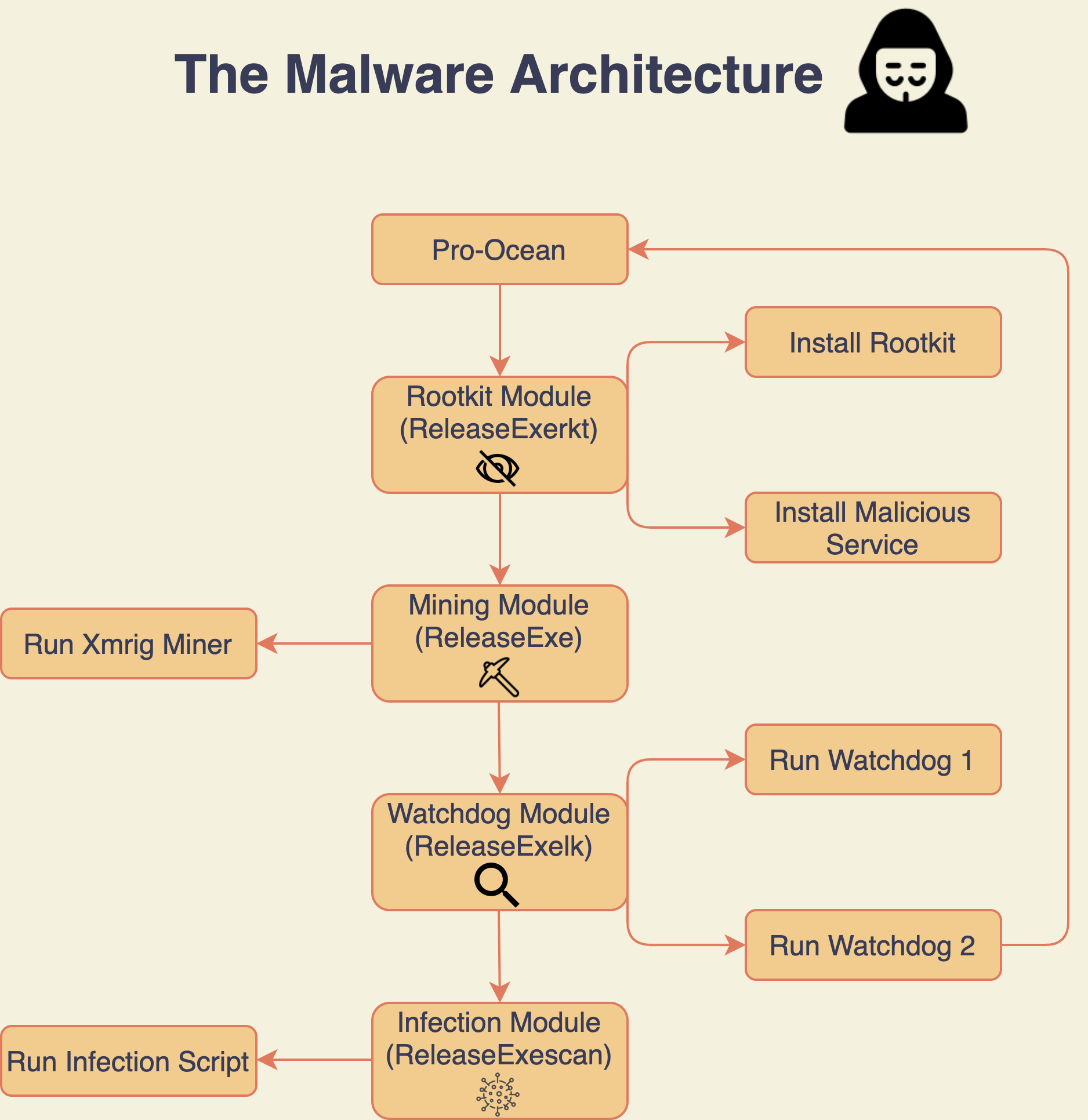
The Pro-Ocean malware discovered by analysts contains “new and improved” tools in the area of rootkits and worms. These features enable Pro-Ocean to effectively hide its malicious activity.
For example, to go unnoticed, Pro-Ocean uses the Linux function LD_PRELOAD, which helps prioritize the loading of certain libraries, as well as the Libprocesshider library.
Let me remind you that we wrote about Australian, that mined cryptocurrency on CSIRO supercomputer.
As noted above, Pro-Ocean has the potential of a worm, and it is very simple to implement such malware propagation. A special Python script uses the public IP address of the infected machine and the identity.me service, and then tries to infect any available machines on the same 16-bit subnet.
“At the same time, the malware does not try to somehow sort out potential victims and simply tries to apply exploits to any hosts it finds in the hope that one of them will work. If successful, the script delivers the payload to the system, which in turn downloads the installation script for Pro-Ocean from a remote HTTP server”, – say Palo Alto Networks specialists.
This Bash obfuscated setup script plays an important role in Rocke’s operations. The fact is that in addition to delivering Pro-Ocean malware to the infected host, it also eliminates competitors by removing any malware and miners already present in the system. In addition, the script gives Pro-Ocean full access by removing the iptables Firewall and any monitoring agents that might notice the attack and understand the alarm.
Since Monero mining is still a top priority for hackers, Pro-Ocean comes with a special module that monitors CPU usage and kills any legitimate processes if they are using more than 30% CPU. The same module regularly checks if the miner is active and restarts it if something goes wrong.
Researchers warn that so far, the malware is using only two vulnerabilities, but their number may increase in the future if the malware authors decide to target Pro-Ocean to other cloud applications and servers. In the meantime, experts are confident that the main targets for Pro-Ocean attacks are cloud services from Alibaba and Tencent.
Let me remind you about the fact that Specialists of the Chinese company Tencent Security reported about the MrbMiner malware, which is used to install cryptocurrency miners on Microsoft SQL databases.





