Microsoft fixes vulnerability in Azure Container Instance
Information security experts from Palo Alto Networks spoke about a new vulnerability in Azure Container Instances named Azurescape. The problem affected the cloud service Azure Container Instances, which allows companies to deploy packaged applications (containers) in the cloud.
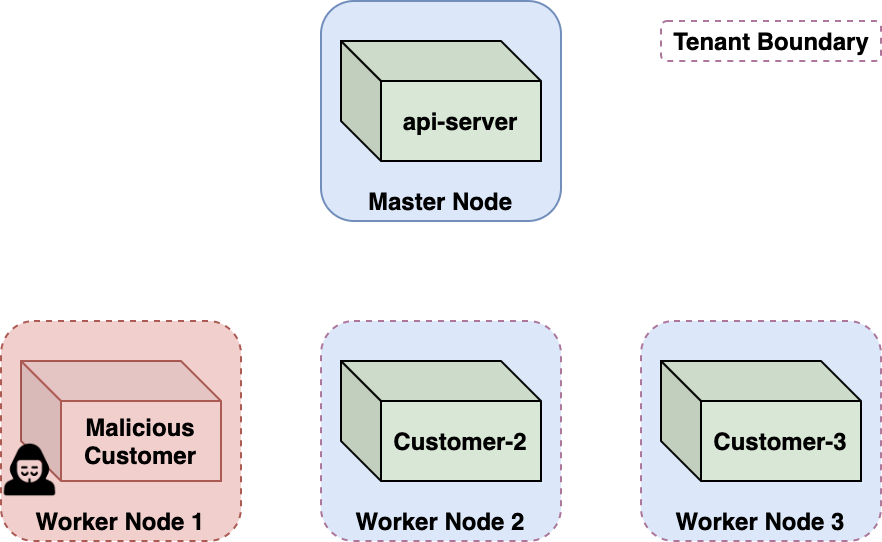
The issue allowed a malicious container to hijack other containers owned by platform users. In essence, an attacker exploiting Azurescape could execute commands in someone else’s containers and gain access to all data from other clients.It is believed that hackers could use the bug to execute code in other users’ containers, steal confidential information, and deploy miners and other malware.
Microsoft has already sent out notifications to its customers warning them to change the privileged credentials for containers deployed on the platform before August 31, 2021.
The company stressed that this is only a precautionary measure, since so far no signs of attacks using Azurescape have been found.
Palo Alto Networks experts note that the vulnerability allowed attackers to compromise multi-user Kubernetes clusters hosting ACI.
The problem was easily discovered when it was revealed that ACI was using code released almost five years ago, vulnerable to bugs related to escaping from the container.
Experts also note that the use of CVE-2019-5736 was enough to escape from the container and execute the code with elevated privileges on the base host.
Let me remind you that we also said that Reserchers discovered in Google Cloud, AWS, and Azure Explore 34 Million Vulnerabilities.