FBI and NSA discovered Drovorub malware, created by Russian Intelligence services
The FBI and NSA issued a joint warning, full of technical details, in which they said they had discovered Drovorub malware, targeting Linux systems and designed to create backdoors.
According to the researchers, Russian hackers from the APT28 group (aka Fancy Bear, Strontium, Pawn Storm, Sofacy, and so on) created this malware. Researchers from this group have been long associated with the Russian special services, namely the 85th main center of the GRU special service.Let me remind you that a year ago US Senator asked FBI to investigate creation of FaceApp, and possible linkage of Russian intelligent organizations with this application.
FBI and NSA officials claim they managed to connect Drovorub to APT28 due to the fact that hackers reuse the same servers for different operations. For example, Drovorub connects to the command and control server, which in 2019 was already used for attacks targeting IoT devices. Then Microsoft specialists documented IP address of its server.
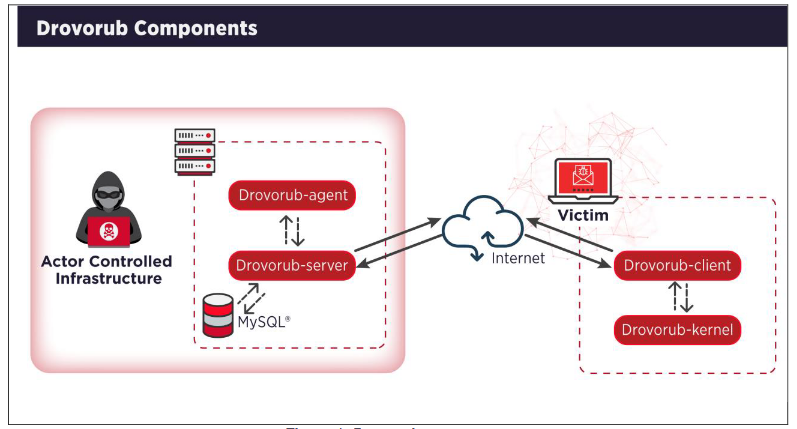
Drovorub is a multi-component system that comes with an implant, a kernel module rootkit, a file transfer tool, a port forwarding module, and a command server.
“Drovorub is a Swiss knife that allows attackers to perform many different operations, including stealing files and remotely controlling victim’s computer. It was built to work stealthily and uses rootkits to make it difficult to detect”, — said McAfee.
Interestingly, the name Drovorub was given not by the researchers, but by the hackers themselves. The well-known information security specialist Dmitry Alperovich, who has been studying Russian hacker campaigns for a long time, recalls that “firewood” in Russian slang indicates drivers.
“Malware name “Drovorub”, which as @NSACyber points out, translates directly as “woodcutter”. However, more importantly, “Drova” is slang in Russian for “drivers”, as in kernel drivers. So the name likely was chosen to mean “(security) driver slayer”, — reported Dmitri Alperovitch in his Twitter.
To protect themselves from Drovorub, US law enforcement agencies recommend that organizations in the US upgrade their systems to a version from the Linux 3.7 kernel or later so that forced verification of kernel and module signatures would interfere with Drovorub.
The 45-page document also contains a guide to running Volatility, Snort and Yara rules, and other useful information for detecting potential compromises.
Let me remind you that recently we talked about FBI warning about cybercriminals, which are looking for money laundering partners through dating sites.





