In 2020, the Pwn2Own Tokyo hacking competition was held, as announced by the organizers back in the spring, in an online format. The event was coordinated by the Zero Day Initiative from Toronto, and participants demonstrated their exploits remotely.
Nevertheless, the contest took place, and the participants raised $136,000 by discovering and demonstrating 23 unique vulnerabilities on six different devices. Manufacturers now have 120 days to release fixes before ZDI releases the details of the bugs.Dozens of teams and individual researchers have signed up for Pwn2Own Tokyo this year. The winner of the competition was Team Flashback, which includes the real veterans of Pwn2Own – Pedro Ribeiro and Radek Domanski.
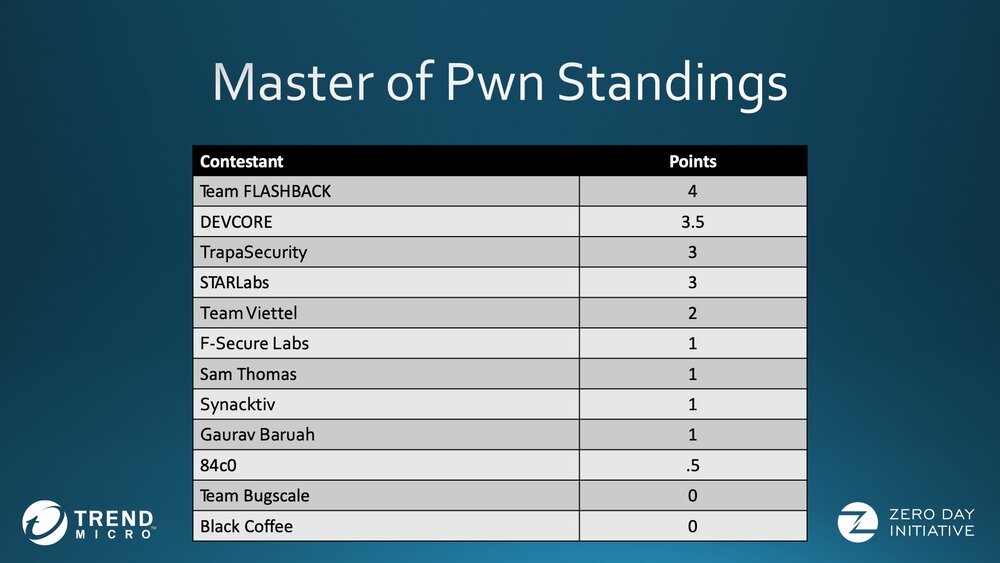
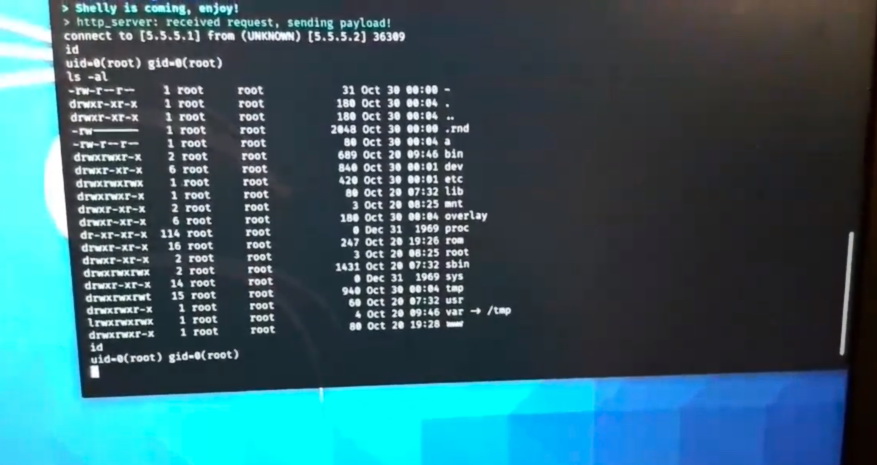
For example, on the first day of the competition, Team Flashback successfully hacked the WAN interface of the NETGEAR Nighthawk R7800 router. To do this, they not only combined the two vulnerabilities, but were also able to leave a persistent backdoor on the device, which preserved even after a factory reset. This hack earned the team $20,000 and 2 Master of Pwn points.
On the second day, Team Flashback compromised a TP-Link AC1750 Smart WiFi router using three arbitrary code execution vulnerabilities. These efforts earned the researchers another $20,000, rising their reward to $40,000, and they also came out on top in the Master of Pwn rankings with 4 points.
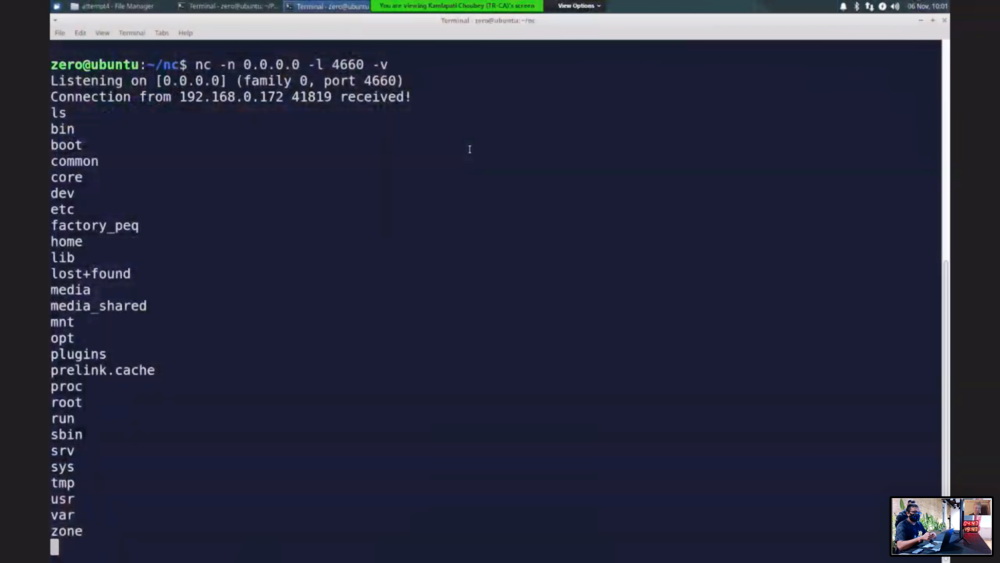
The runner-up team, DEVCORE, earned $20,000 for successfully demonstrating an exploit against Synology DiskStation DS418Play NAS. It is worth saying that their first hack attempt failed, but the second attempt took only 3.5 minutes, and root access to the server was gained thanks to a heap overflow.
Another $17,500 DEVCORE brought an exploit targeting the Western Digital NAS My Cloud Pro Series PR4100. To do this, the team used a chain of six vulnerabilities, but, unfortunately, two of these bugs have already been reported earlier.
The third place is shared by the Trapa Security and STARLabs teams. For example, the first one earned $20,000 for an exploit aimed at a Western Digital My Cloud Pro Series PR4100 device (by the way, this was the first NAS hacked within the framework of Pwn2Own). To do this, the researchers used authorization bypass as well as the command injection problem. Another $5,000 was raised by hacking the NETGEAR Nighthawk router.
The STARLabs team made the same amount of money for exploits targeting the LAN interface of the NETGEAR Nighthawk R7800 router and the Synology DiskStation DS418Play NAS.
In addition, this year, Pwn2Own members successfully compromised smart TVs Samsung (Samsung Q60T) and Sony (Sony X800), but this did not bring money to hackers, since the vulnerabilities they used were already known earlier.
It’s worth noting that Facebook sponsored the event this year, and the company invited researchers to try to hack into Oculus and Portal devices. However, the specialists preferred to focus on routers, NAS and TVs.
Let me remind you that recently in China ended almost a clone of the Pwn2Own championship called Tianfu Cup (the Chinese do not welcome openness) and it was reported that were hacked both iOS and Chrome.





