Last summer, Doctor Web experts discovered an unremarkable malware on Google Play that was distributed under the mask of an OpenGL Plugin application. The malware allowed remotely control infected Android devices and monitor their users. It turned out that this incident is part of the PhantomLance backdoor’s large malware campaign that has been spreading through Google Play for years.
Kaspersky Lab experts found that this Trojan, unlike the vast majority of other malware found on Google Play, was surprisingly complex. The company’s own investigation revealed that the malware was part of the PhantomLance malware campaign, dating back to the end of 2015.Researchers have identified several versions of PhantomLance. Despite the differences in time they arrived and increasing complexity with each version, they are quite similar in their capabilities.
“PhantomLance’s primary goal is to collect sensitive information from the victim’s device. To do this, malware can obtain root rights on the device, and thus gain the ability to transmit geolocation data, call logs, SMS messages, a list of installed applications and full information about the infected device to its operators. Moreover, its functionality can be expanded at any time by loading additional modules from the command server”, – write Kaspersky Lab experts.
To spread PhantomLance, the attackers seem to have used mostly Google Play. So, the malware is also found in third-party application directories, but for the most part they are only “mirrors” of the official Google app store.
Researchers claim that applications containing one of the versions of the Trojan appeared on Google Play at least since the summer of 2018. As a rule, the malware was hiding in utilities for changing the font, removing ads, cleaning the system, and so on.

Now all malicious applications have already been removed from Google Play, but so far they can be found in other directories. It’s ironic that some of these “mirror directories” report that the installation file was downloaded directly from the official Google store, and therefore does not contain viruses.
How did the attackers manage to push the trojan into the official app store?
“Firstly, hackers showed great attention to detail and, for greater reliability, created a profile for each utility on GitHub (which, however, contained only a license agreement). Secondly, the applications that were initially downloaded to the store were not malicious. The first versions of the programs did not contain any suspicious functions and therefore easily overcame all checks on Google Play. Only after a while, with the next update, the application acquired the malicious functions, desirable for its creators”, – explain analysts.
Judging by the geography of PhantomLance distribution, as well as by the presence in stores of special versions of malicious applications in the Vietnamese language, the main goal of the creators of PhantomLance were users from Vietnam (as well as users from India, Bangladesh, Indonesia and so on).
In addition, experts were able to notice a number of signs linking PhantomLance to the previously discovered hacker group OceanLotus, which is responsible for creating a whole line of malware also is focused on users from Vietnam.
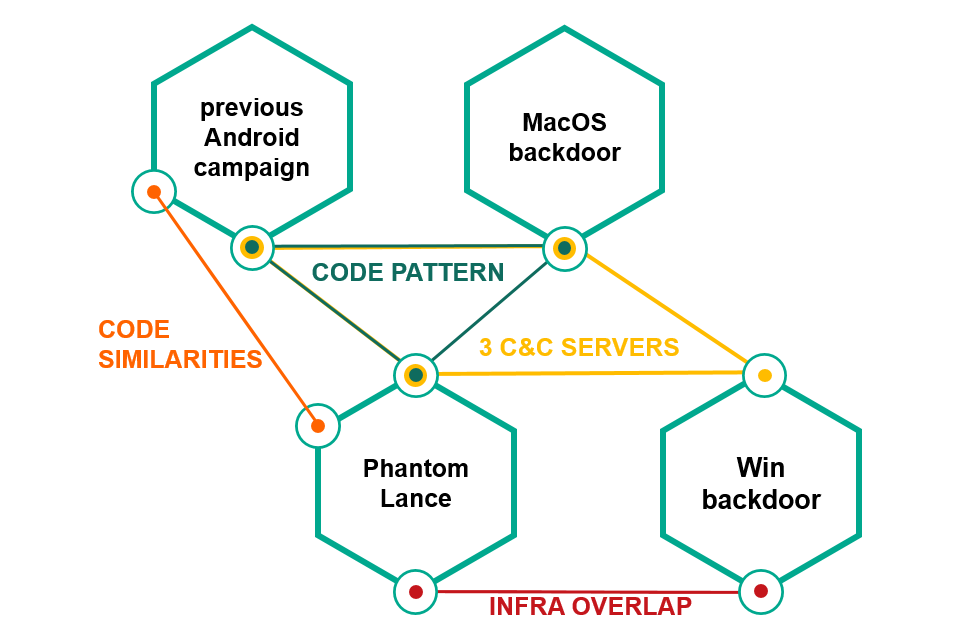
OceanLotus’s previously investigated malware tools include the macOS backdoor family, the Windows backdoor family, and the Android trojan suite, whose activity was noticed in 2014 – 2017. According to experts, since 2016 PhantomLance has replaced them. However, it is not alone.
A detailed technical report on the threat found can be found here.





