Hackers Attacked Uber and Could Steal Source Codes and Information about Vulnerabilities
Hackers attacked Uber and are currently investigating the incident with law enforcement officials. Meanwhile, the attackers shared screenshots of the company’s internal systems with the media, including the email dashboard and Slack server, but could also access the source code and the company’s bug bounty program on HackerOne.
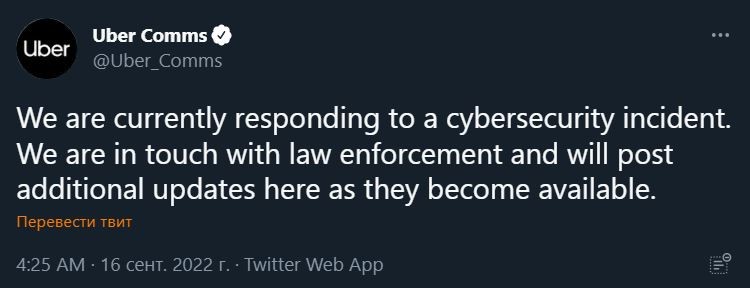
Let me remind you that we also reported that Hack group Stormous hacked Coca-Cola’s servers, and also that One of the largest American media holdings News Corp has been hacked.The New York Times was the first to report the hack, and Uber has officially confirmed the hack on Twitter.
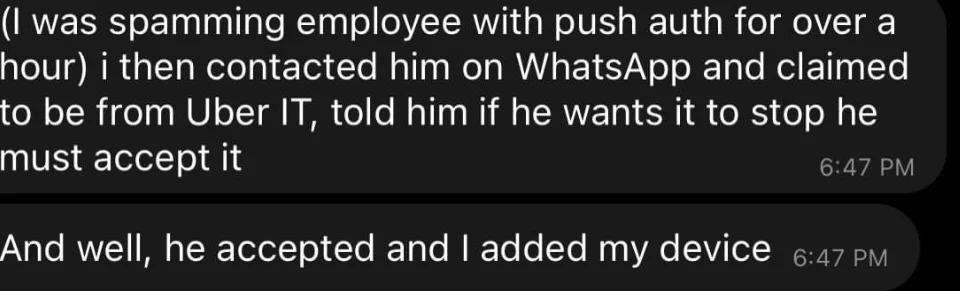
The New York Times journalists managed to communicate with the attacker, and he said that he was only 18 years old, and he hacked Uber “because the company has weak security.” To be more precise, it’s about social engineering: the hacker said that he attacked one of the company’s employees (he introduced himself as a support employee) and stole his password. The attacker says he bombarded an employee with two-factor authentication requests for more than an hour and eventually forced him to allow entry.
The attacker then gained access to the company’s corporate VPN using the stolen credentials and began scanning the internal network for sensitive information.
According to the hacker, during these scans, he found a PowerShell script that contained administrator credentials for the Thycotic access control platform. He used this information to gain access to other internal services of the company.
In turn, Bleeping Computer, which also studied the screenshots provided by the hacker, reports that the hacker seems to have gained full access to many critical Uber systems, including the company’s security software and the Windows domain. The hacker also reached the Amazon Web Services console, VMware vSphere/ESXi virtual machines, the Google Workspace email admin panel, and the Slack server where he posted messages.
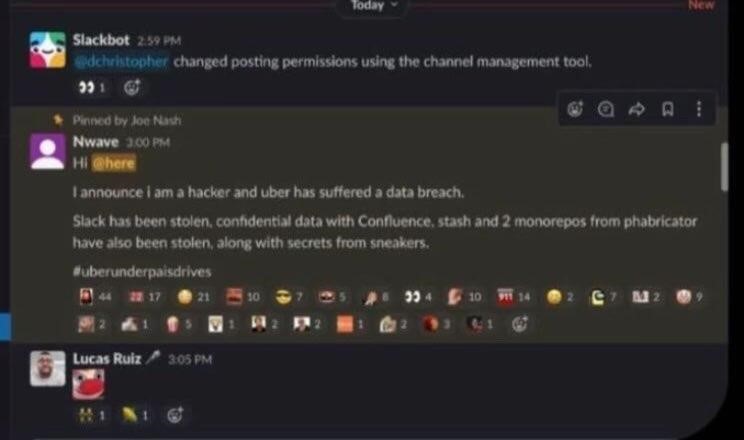
The attacker also hacked the Slack server and sent messages to employees about the hack. At first, these statements were met with memes and jokes, as the employees did not realize that a real attack was taking place.
In addition, experts noticed that the hacker had access to even more important data: the company’s bug bounty program on HackerOne. There, the hacker commented on all the tickets, as shown in the screenshot below.
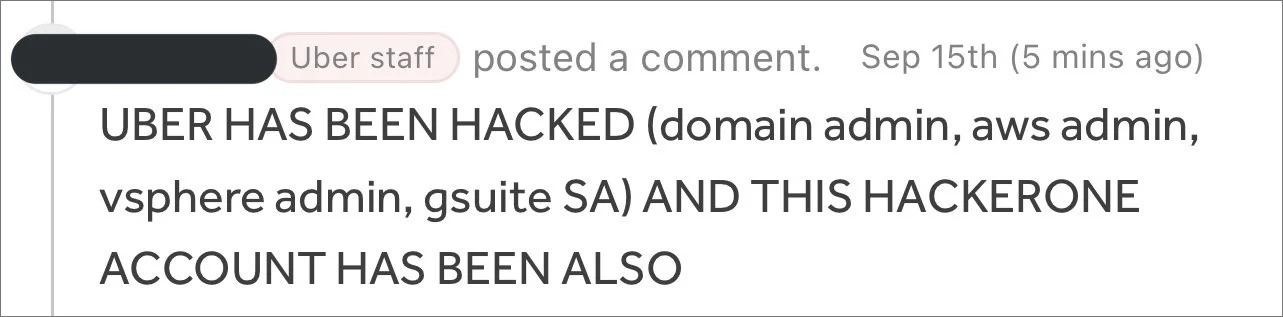
According to Yuga Labs engineer Sam Curry (the hacker commented on his two-year-old bug report, which attracted the attention of an expert), the attacker had access to all reports of vulnerabilities in Uber on HackerOne, including those for which there are no fixes yet. Bleeping Computer journalists write that the hacker managed to download all the data before losing access.





