Firefox bug allowed stealing cookies from Android devices
Independent information security expert Pedro Oliveira spoke about the CVE-2020-15647 bug, which he discovered in the spring of this year in Firefox for Android devices. Using a specially crafted HTML file, it was possible to steal cookies from the victim’s device.
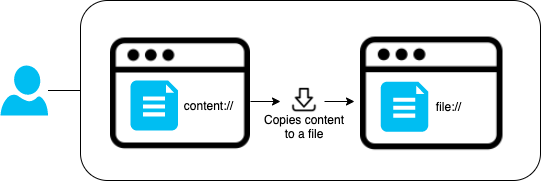
The vulnerability is linked with the way how Firefox handles local files through the content://URI. The exploitation of the bug made it possible to remotely obtain copies of cookies from the device, which gave an attacker access to some sites viewed by the user.“To exploit the problem, you had to convince the user to open a specific HTML file. The malicious file opened an iframe that called the content://URI for profiles.ini, which contains the Firefox user’s profile information as well as cookies”, – writes Pedro Oliveira.
Because Firefox was handling the URI incorrectly, the researcher was able to obtain a copy of this local file, which should not be accessible through the web page.

The researcher explains that the browser redirects the content://URI to access local files on the device to the file://URI, indicating that it saved a copy of the requested resource in a private cache directory before loading it.
“This content://URIs requires reading and writing permissions to be available to other applications. When you share a URI between apps (for example, via Share with), the source app must provide permissions for that URI (before sharing). As a result, the URI has permissions when it is shared with the receiving application, and only that application can access it. However, when the application itself processes its URIs (and not other applications), these permissions are not applied, which means that the application can freely access the content”, — says Oliveira, noting that any file downloaded by Firefox prior to version 68.10.1 was processed in this way.
Since the malicious file mentioned above and the local file loaded by the exploit have the same names, a substitution occurs in the private directory. As a result, the expert explains, the attacker receives an open malicious cached file, and the original file is replaced. After the iframe is loaded, the cached malicious file sends its content to the malicious page, where the attacker sees it. Since the path and source have not changed, no warnings are displayed.
This vulnerability was fixed back this summer, when Firefox was updated to version 68.10.1.
Let me remind you that In Firefox and Chrome fixed vulnerabilities discovered on Tianfu Cup.



![Attackers seized Bitcoin [.] Org](https://adware.guru/wp-content/uploads/2021/09/Attackers-seized-Bitcoin-.-Org-390x220.jpeg)

