Firefox 66.0 Release – 5 critical vulnerabilities fixed!
Among the critical gaps were noted “use-after-free” (CVE-2019-9790), which occurs when the pointer (raw pointer) to the DOM element is extracted via JavaScript, and the element is removed during use. This can lead to a fatal crash.
Two other critical issues affect the IonMonkey JavaScript JIT compiler (CVE-2019-9791 and CVE-2019-9792), they can also lead to a crash that an attacker can use. For example, IonMonkey can “merge” the internal “magic number” JS_OPTIMIZED_OUT, which can lead to memory corruption using JavaScript.
Among the high-risk vulnerabilities, CVE-2019-9793 can be distinguished – incorrect boundary checking with Specter patches disabled.
Also, the Mozilla team fixed the memory security bugs in Firefox 66 and Firefox ESR 60.6 — these problems were found by the Mozilla team itself.
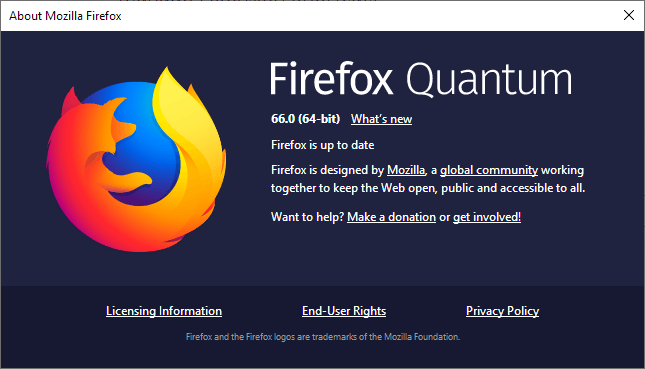
Users are advised to install the new version of the browser as soon as possible.
https://www.mozilla.org/firefox/new/