“No Fly List” – A List of People Who Are Forbidden to Board the Planes, Published on a Hacker Forum
Last week, a researcher discovered that the American airline CommuteAir accidentally left a list of people who should forbidded to board aircraft flying to or from the US (the so-called “No Fly List”) on an insecure server.
Now this file, containing more than 1.5 million entries, has been published on a hacker forum.By the way, we also wrote that DDoSecrets Activists Published 269 Gb of US Law Enforcements Data.
Let me remind you that the unsecured CommuteAir server was accidentally discovered on the network by the Swiss hacker maia arson crimew, who considers himself a hacktivist. In the past, this person was known as Tillie Kottmann, but recently officially changed his name to the above.
He said that the server stored a wide variety of data, including the personal information of approximately 9,000 CommuteAir employees, flight directions, and could also easily access flight plans, aircraft maintenance information and other data.
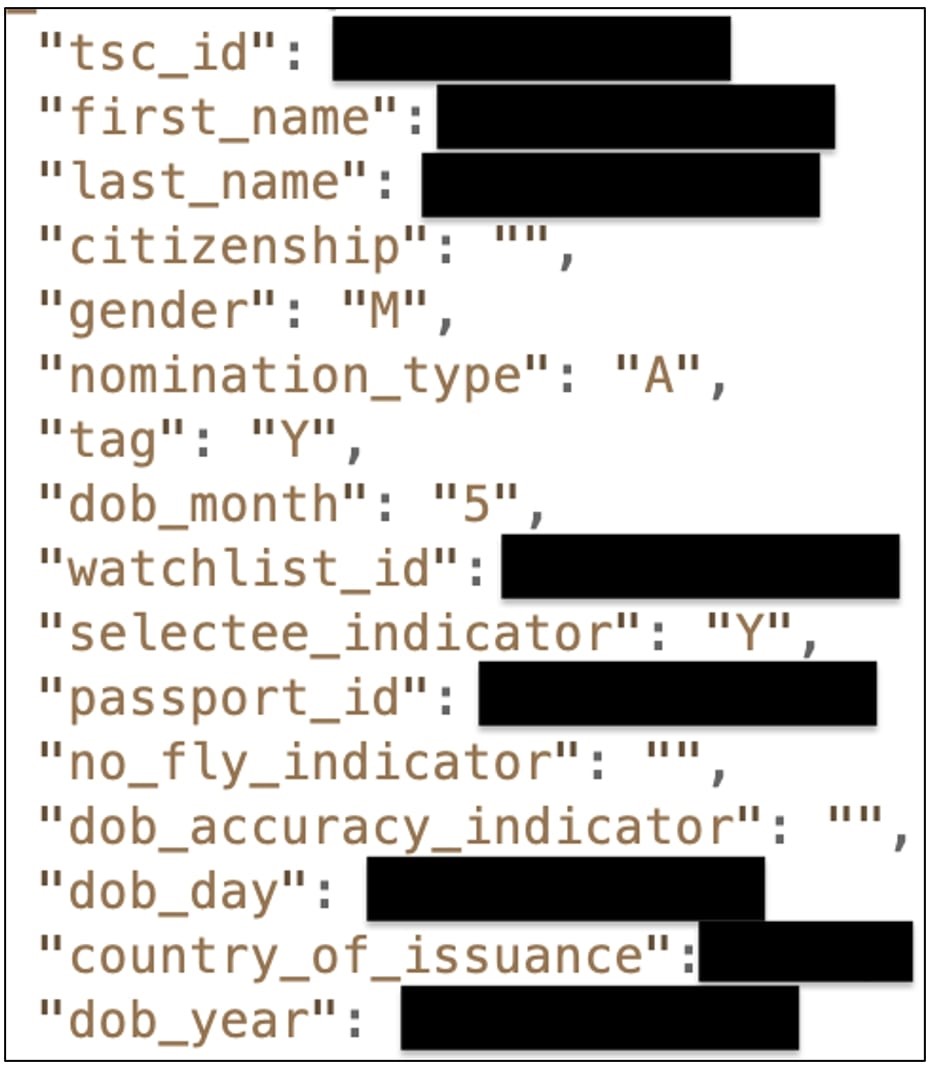
There was also a file containing a copy of the so-called “No Fly List“, dated 2019. This list contains over 1.56 million entries and includes names and dates of birth, although many entries are duplicated.

maia arson crimew shows off the list on the laptop screen
Similar lists began to appear in the early 2000s, after the September 11 terrorist attacks. At first, they contained only a few dozen names (mostly people who are “known or reasonably suspected of involvement in terrorist activities”), but after the attacks and the creation of the Department of Homeland Security, the lists began to grow rapidly.
Currently, the No Fly List, maintained by the FBI’s Terrorist Screening Center (TSC), is relied upon by many US federal agencies and is used to manage and share consolidated information for counterterrorism purposes.
Such databases are considered secret even if they are not classified, given the role they play in national security and law enforcement. Terrorists and other suspects who pose a threat to national security are “nominated” for inclusion on this list at the discretion of the authorities.
While the No Fly List is not available to the public, it is frequently referenced by private airlines and numerous government agencies, including the US Department of State, the Department of Defense, the Transportation Security Agency (TSA), and the Customs and Border Protection (CBP). This list is used to check whether a passenger is allowed to fly in principle, whether he can be admitted to the United States, and other likely risks are also assessed.
Let me remind you that arson crimew is not the first to get access to No Fly List. Back in 2021, cybersecurity expert Bob Diachenko was the first to discover a copy of the TSC database on the network. Then the list of persons who should not be allowed to fly was found in the Elasticsearch cluster, on the Iranian IP address.
Dyachenko notified the Department of Homeland Security about the leak as soon as the database was indexed by Censys and ZoomEye search engines. As a result, the server was down after about three weeks, and the expert wrote that he did not know why it took so long, and it is not known if unauthorized persons had time to get to the list.
The arson crimew find differs from this case in that now No Fly List has been seen for the first time on a public site, available to anyone. Moreover, the list found in 2021 by Dyachenko was more detailed: it contained full names, gender, passport numbers, data on the country of issue of documents, TSC identifiers, and so on. The list, discovered last week, contains only full names and dates of birth.
As Bleeping Computer now reports, at the end of last week, the list found by arson crimew was published on a hacker forum. And here it should be noted that arson crimew promised to provide the list to journalists and human rights organizations for the “public good”, but considered it wrong to publish it in the public domain.
The journalists confirmed that it was the No Fly List, originally found on the CommuteAir server, that was published on the hack forum by examining parts of the list presented as two CSV files named NOFLY and SELECTEE. The latter file seems to collect data from passengers who always go through Secondary Security Screening Selection (SSSS) at airports when flying to the United States.
The dump posted on the forum contains 1,566,062 entries and includes many duplicates and variations of the entry for some names (meaning fewer than 1.5 million people are actually on the list). The SELECTEE list consists of 251,169 entries. For example, the list mentions Viktor Bout and lists 16 of his possible pseudonyms.
Although the leak came from an insecure AWS server owned by a private airline, the incident clearly did not please the US authorities, who are already investigating the incident. In particular, journalists report that on January 27, the TSA issued a special security directive intended for airports and air carriers.





