FBI seized $ 2.3 million in cryptocurrency from partner of hack groups REvil and GandCrab
Bleeping Computer writes that in August of this year, the FBI seized $ 2.3 million from a partner of the hacker groups REvil and GandCrab. 39.89138522 bitcoins were withdrawn from the Exodus wallet on August 3, 2021, and at the current exchange rate, the cryptocurrency is estimated at about 2.3 million ($ 1.5 million at the time of the withdrawal).
The FBI did not say exactly how the agents managed to gain access to the wallet, but, apparently, law enforcement officers were able to gain access to the wallet’s private key or secret passphrase.According to court documents, this wallet contained money from the victims of the REvil ransomware and belonged to the partner of the hack group Alexander Sikerin, being linked to the email address engfog1337@gmail.com.
The GandCrab and REvil organizations operated as Ransomware-as-a-Service (RaaS), when the main partner of the operators cooperates with third-party hackers called affiliates. As part of this collaboration, major operators developed and operated encryption / decryption software, payment portal, and data leak sites. Affiliates are tasked with hacking into corporate networks, stealing data, and deploying ransomware to encrypt devices.
Any ransom payments will then be split between the affiliates and the main operators, with the operators usually receiving 20-30% of the ransom and the affiliates the rest.
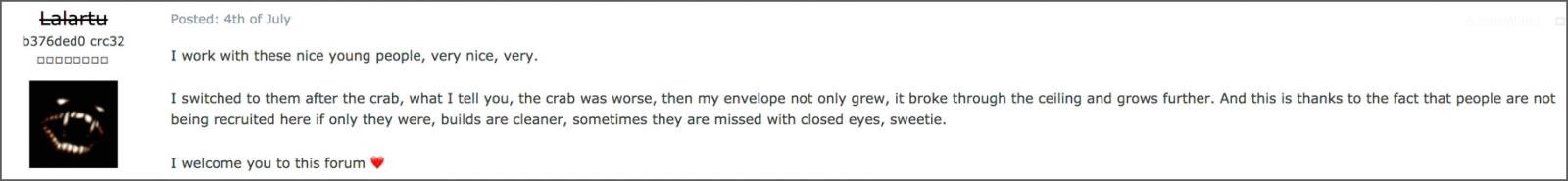
Although the FBI does not provide the attacker’s nickname, reporters note that the name engfog in the email address clearly refers to the hacker Lalartu, who previously worked with groups such as GandCrab and REvil (Sodinokibi).
Back in the McAfee report on REvil activity, researchers tracked Lalartu’s money trail. So, in 2019, he wrote on a Russian-language hacker forum that he once worked with GandCrab, and then switched to REvil after the first ransomware stopped working.
Let me remind you that we also wrote that FinCEN Tied $ 5.2 Billion Transactions to Ransomware Operations.